Today we are happy to announce the release of version 0.9.9. This release brings several new and/or improved features that we are pretty excited about:
- Offline mode for Kesakode
- Python 3.13 support (in the disassembler, and in Malcat too)
- Threat intelligence available in the lite edition
- All view can now be exported as HTML/SVG/CSV
- New view switcher control
- Several file parser improvements
The biggest one is the offline mode for Kesakode, which lets you identify malware in just a couple of milliseconds, without having to upload anything to the outside. We hope you'll make good use of this feature. But let us go through the most impactful changes together:
Kesakode
Offline Kesakode!
Kesakode is our function/strings/constants hash lookup service introduced in version 0.9.6. It is used to identify precisely (unpacked) malware. Since its release, we have seen many happy Kesakode users and most of you like the service overall, but that doesn't mean it can't be improved. The only complaint we've got so far regarding Kesakode are:
- The quota is too low (although it is quite high tbh, but I get it)
- You are not able to submit hashes online (either because even hashes are too sensitive, or you don't have any internet connection at all)
So we've decided to kill two birds with one stone and bundle an offline database of Kesakode with Malcat. The idea behind this is as follow: Kesakode's database is pretty huge (> 200 millions of unique hashes), but 99,99% of the database are clean or library files. Indeed, there are not that many malware families in the wild (Kesakode covers about 2000+ of them). So we have decided to export all function, constant and string hashes that are unique to the malware set into a single file, and it happens that this file is 27MiB big only!
Starting with 0.9.9., this offline database will be bundled with every full & pro version of Malcat. And because Kesakode lookup are well-optimized, this offline Kesakode lookup is fast enough to be run with every analysis, and its result gets displayed in the summary view. How fast is it? Just look for yourself:
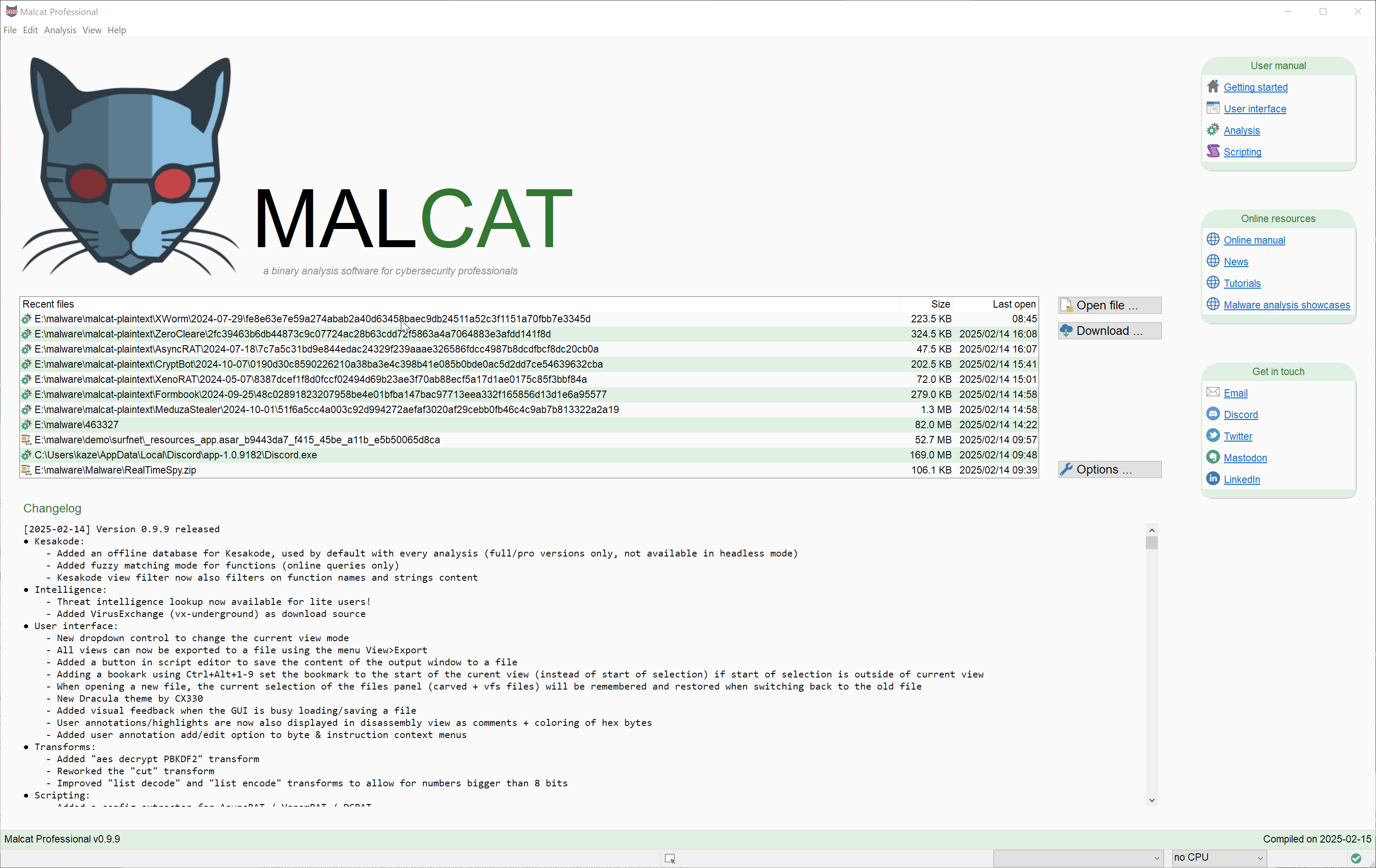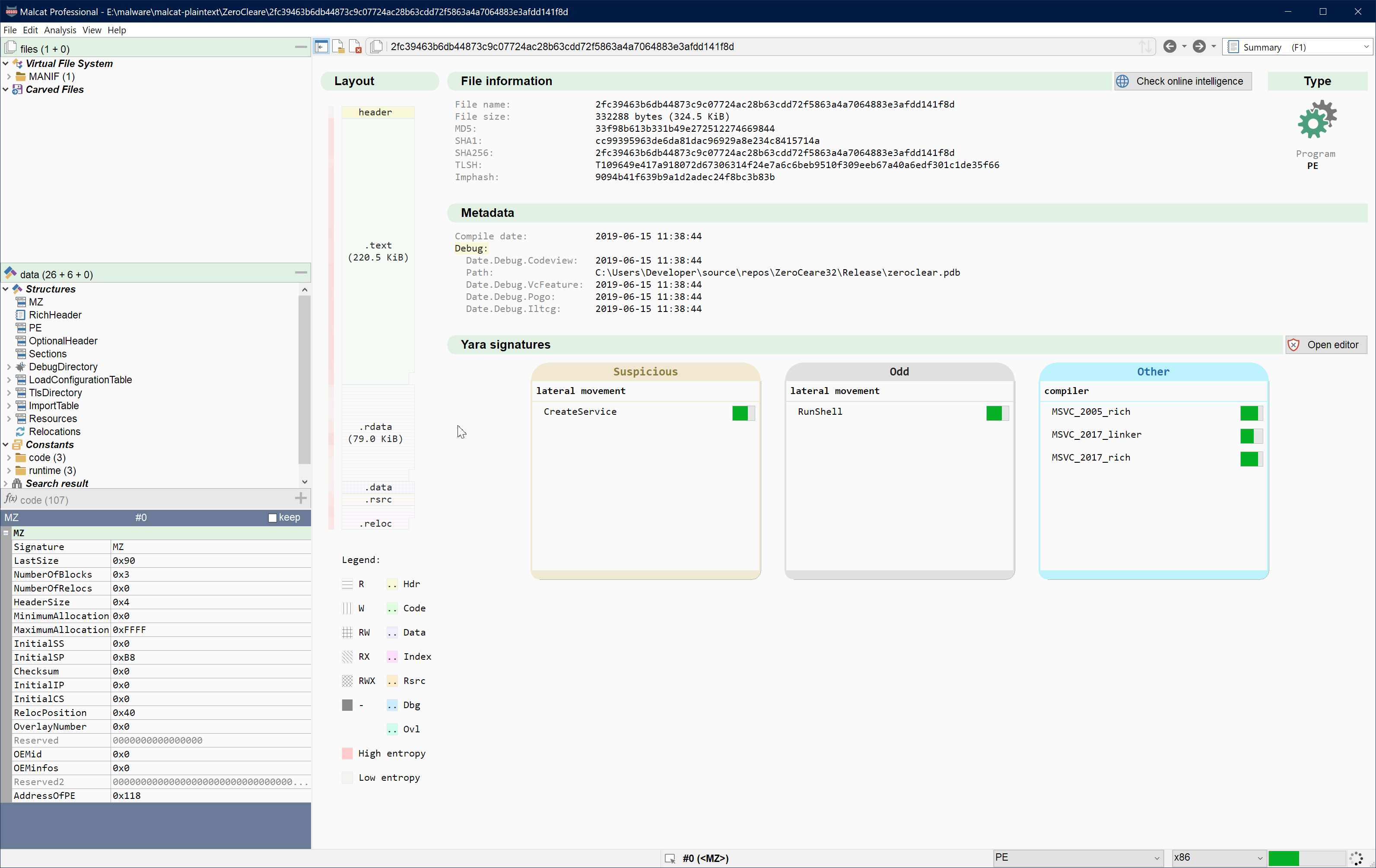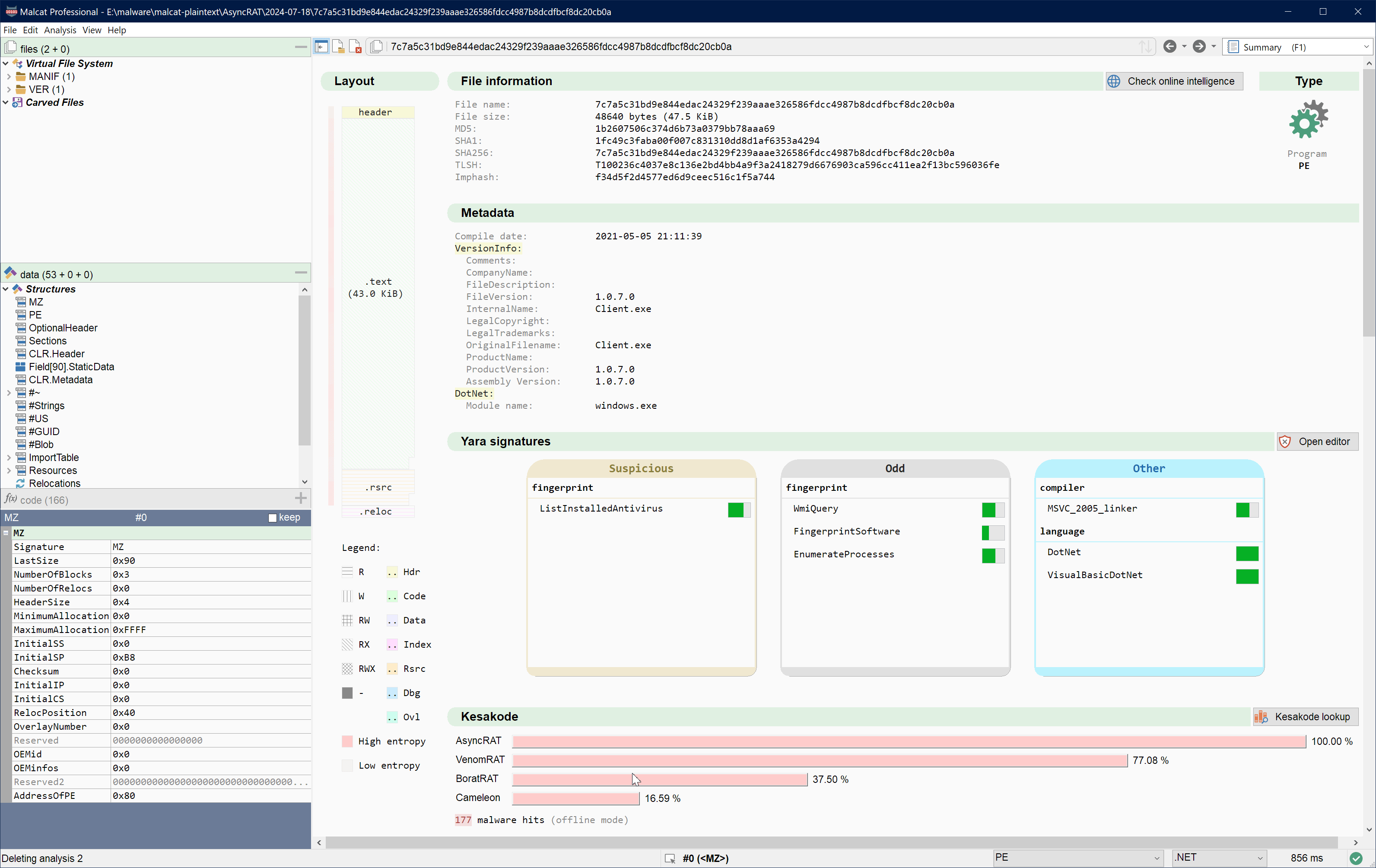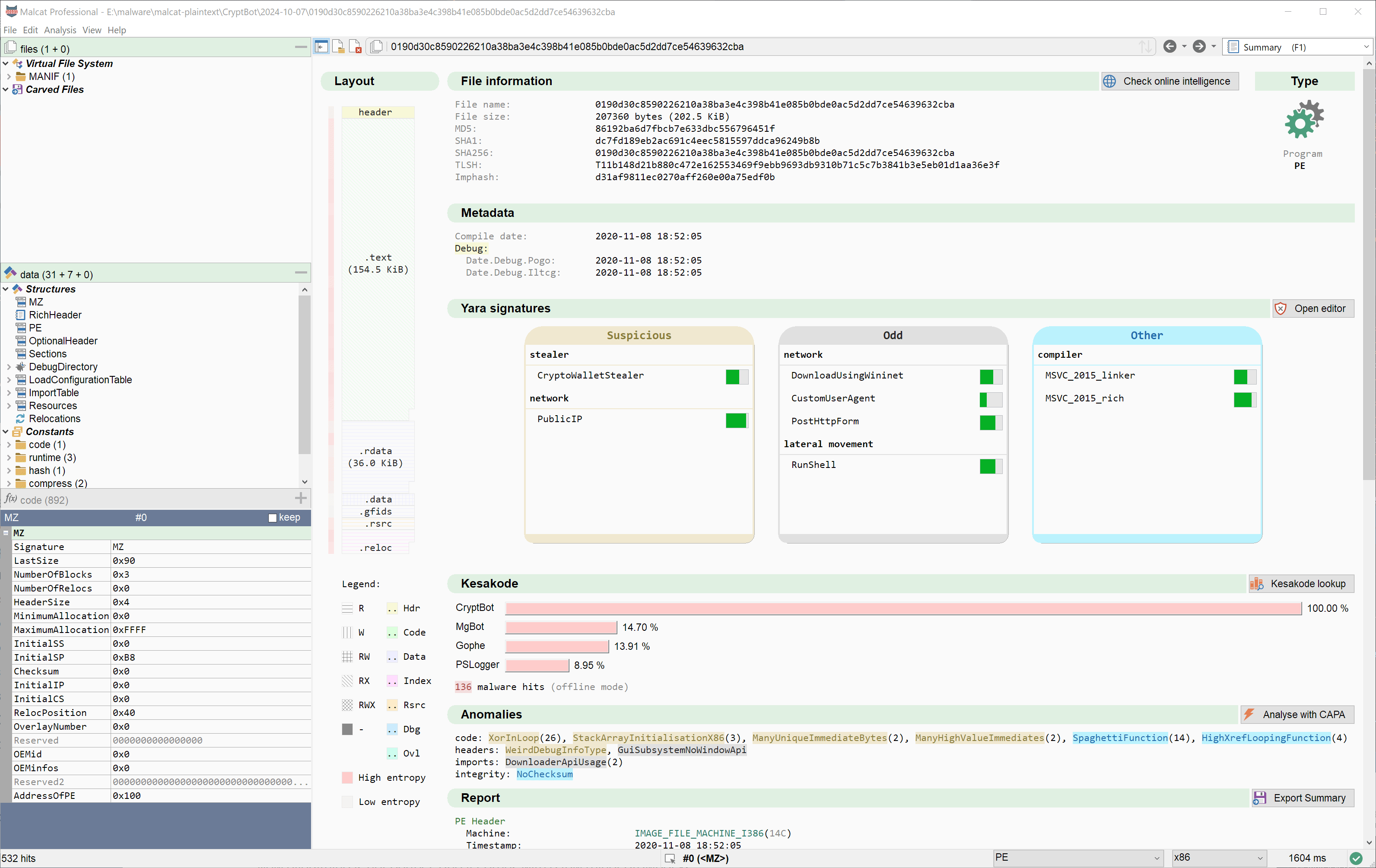
Now everything is not perfect, and it comes with a few minor drawbacks:
- Since only malware signatures are included, you are missing clean and library matches, which are also valuable for reverse engineering
- This offline database will be updated with every Malcat release (so every few months), while Kesakode's database gets updated on a ~weekly basis
- Since Malcat's scoring system takes into account clean hash hits, the score for offline Kesakode might be slightly less precise than its online counterpart. In practice, you may see detection scores be somewhat lower, but never higher
- In order to prevent abuse, the offline database is not yet available via scripting in headless mode. If you need to scan large batches of files, you can contact us: we have a OEM version optimized just for this
By chance, you still have access to the online version of Kesakode from within the Kesakode view. So if you have a doubt or need clean/library coverage, you can always perform an online query as usual (which will consume a token this time).
Since Kesakode offline is a new feature only accessible to paid paid users, we have decided to make the threat intelligence feature available to lite users. 1 feature in, 1 out, we'll try to stick to this rule in the furture.
Fuzzy match mode
Since the beginning of Kesakode, we have had two sets of hashes in our database: exact hashes (well not exact-exact since for functions, offsets are masked out) and fuzzy hashes. Fuzzy hashes are used for constants for instance, but they are actually also computed for functions. Function fuzzy hashes were just never integrated into the UI, mostly for performance reasons (fuzzy matchings is orders of magnitude slower). But since then, we have optimized a few processes in Kesakode's online service and have decided to give it a try. You will now notice a checkbox named Fuzzy matching in Kesakode's view. It is unchecked by default, but when checked, Malcat will perform the following:
- Use Kesakode's online service to perform a normal exact hash lookup as usual
- For all unknown function that have not been identified already, try to identify them using fuzzy matching (the threshold is hardcoded at 80+% similarity)
You can see it in action in the example below: I patch a few opcodes of a function and query Kesakode as usual: the function is not recognized anymore (which is standard behavior for exact hashes). But when I check the Fuzzy matching checkbox, we can see that Malcat is able to recognize the function again, albeit with a lower confidence score:
A quick note regarding performances:
- This will be slower, don't try this on very huge binaries it will take forever
- Only malware hashes are considered for fuzzy matching
- This is still a work in progress: don't expect it to be perfect. It will spot minor changes, but that's it.
At the end, while this feature is interesting on the paper, we've not found it very useful in practice. Kesakode's joint usage of function, strings and constant hashes is good-enough without fuzzy matching that you'll be able to identify malware even if the malware has changed. It is very unlikely that a malware change both its code, hard-coded constants AND its strings at the same time. And if it does, chances are that fuzzy matching won't save you neither.
3rd party providers
Threat intelligence providers in Malcat are python scripts located in data/intelligence that allow you to query multiple hash lookup services or download a sample by hash. We have finally frozen the intelligence API in Malcat and documented it extensively. And we have also added a new capability for these providers: to act as an alternative source for Kesakode function and strings lookups.
While we like our Kesakode service, maybe you don't. Or maybe you would like to use better databases such as Intezer, Threatray or Glimps. Or maybe you would like to try other methods of function identification, like your own MCrit instance, or Binlex.
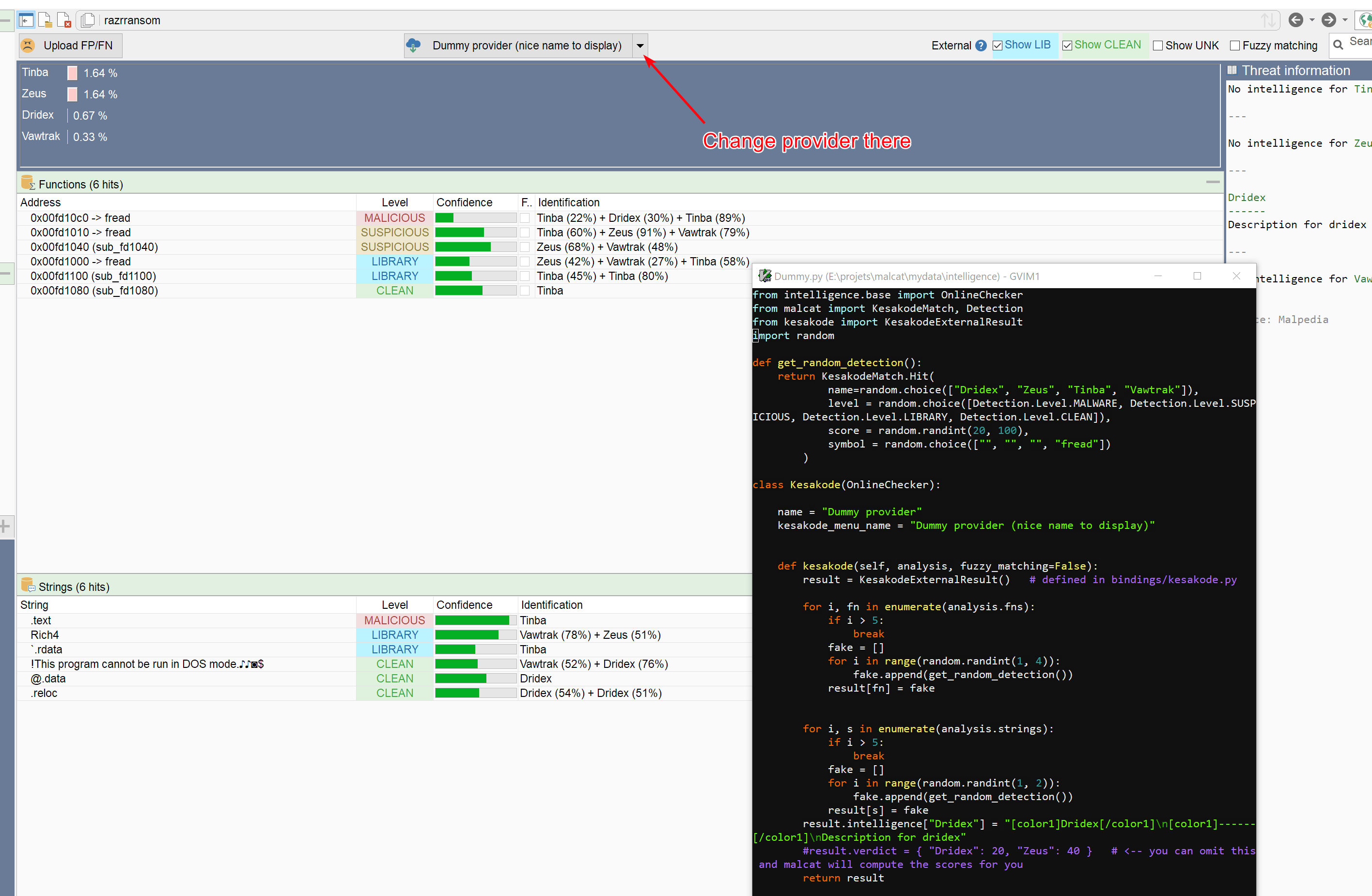
In order to allow you to do this, user-defined intelligence service can now implement their own kesakode method and act as an alternative provider. In the Kesakode view, you will be able to chose these providers by using the dropdown button. Currently, there are none, but I count on you to write your own plugins, that is rather easy to do now!
User interface
New view switcher control
Since the beginning, Malcat has used a toolbar as UI control to switch between its different views. Some of you had a hard time distinguishing between the different icons. And even worse, under GTK a lot of padding is added around each button of the toolbar, which removes a lot of horizontal real estate in Linux:
So in this new version, we have switched to a dropdown control, with icon+text (and better-chosen icons). This should make things easier on the eye, give more horizontal space to the project switcher control and may even teach you passively the keyboard shortcuts to switch views:
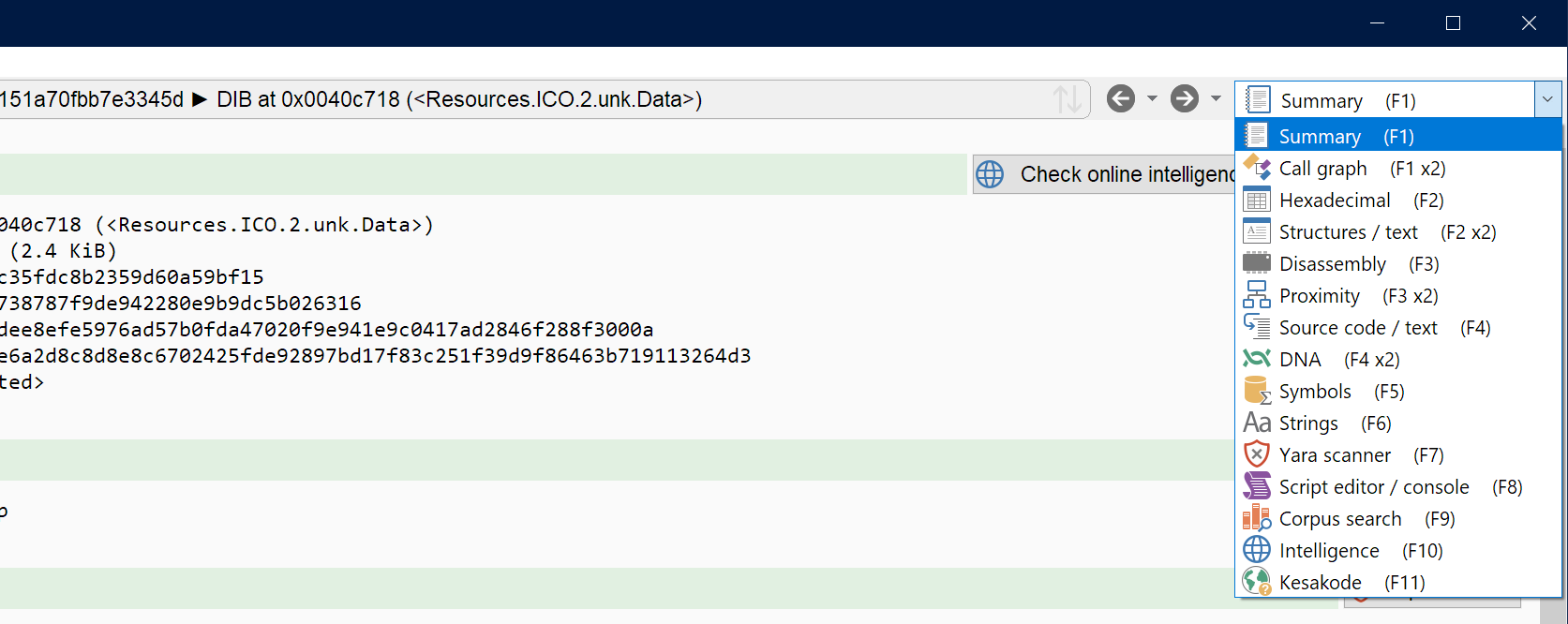
This is not fixed in stone, so if you don't like it don't hesitate to tell us!
View export
Many of you have requested to export Malcat's views to something usable in a report. Of course screenshots are always possible, but it's not always the most convenient way to show something. In Malcat 0.9.9, all views in Malcat can be exported using the menu View > Export to file. How the view will be exported depends on the view type:
- The summary, hexadecimal and text/structure view can be exported as HTML
- The disassembly view can be exported as HTML, SVG (if you want the arrows) or PNG/JPEG
- The graph-based views like the proximity view or the call graph can be exported as either SVG or PNG/JPEG
- Other views can be exported as CSV files
For instance, here is a SVG export of the proximity view for a given function. You can zoom-in, you won't see pixels:
We hope you'll find this useful!
User annotation visible in the disassembly view
In Malcat, you can use so-called user annotations to highlight important regions in your sample. These annotations are good to take quick notes or to prepare for screenshots: they appear in the symbol view and you can navigate through them using the keyboard shortcuts h and H. User annotations can also bee added programmatically via Malcat's python bindings.
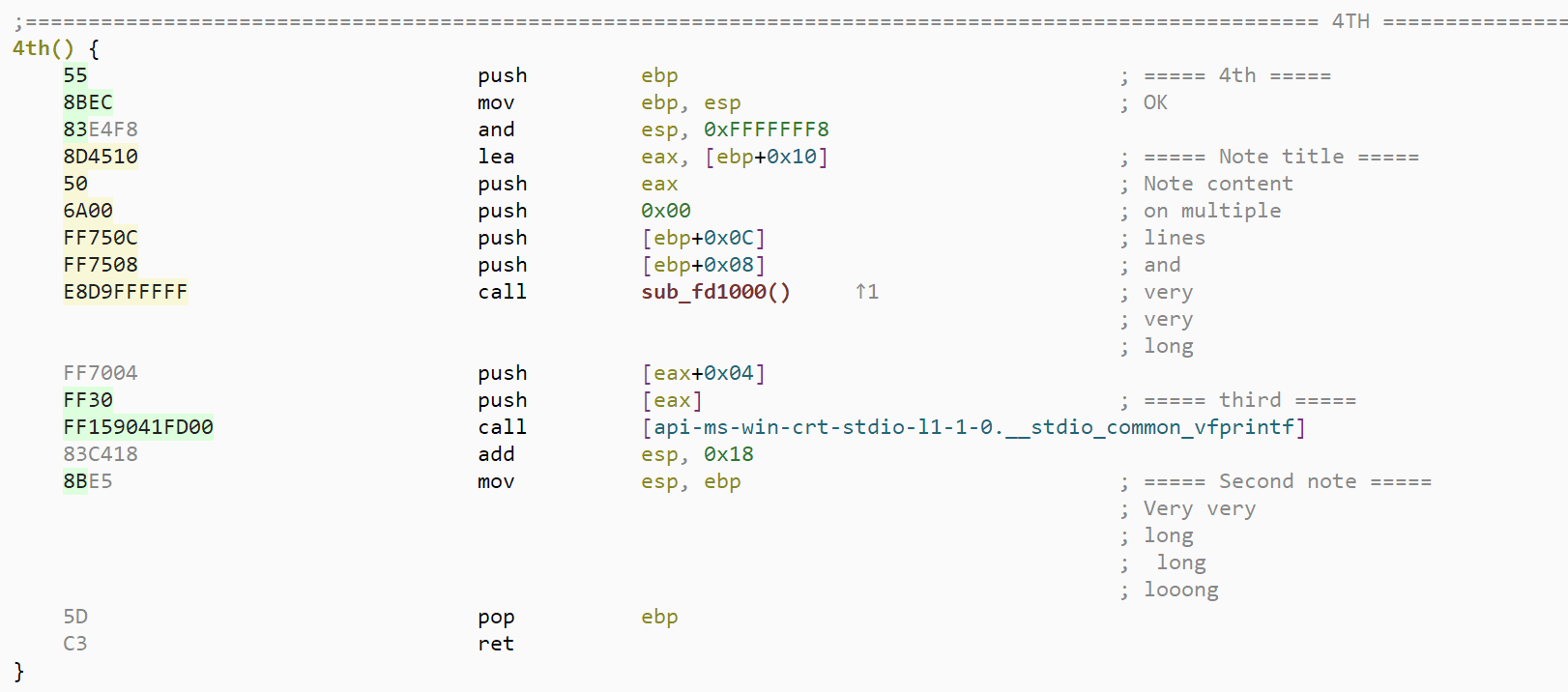
These annotations were only visible in the hexadecimal and structure views until now. But in the version 0.9.9, we have made them also visible in the disassembly view. So if you have a script that automatically annotates code regions (like the user at the origin of this feature request), you'll now be able to see the result there too!
File parsers
Python 3.13 support
Python 3.13 has been release for 5 month now, so it was more than time that we add proper support for it in Malcat. We have thus made the following additions to Malcat:
- Fixed the .PYC file parser and add support for python 3.13 .PYC files
- Fixed the .PYINST file parser and add support for python 3.13 pyinst archives
- Added support for python 3.13 opcodes in our python disassembler
- Added a Linux port of Malcat linked against python 3.13 (currently built on Ubuntu 24.04)
- The Windows version now comes with python 3.13 embedded
We have also removed support for outdated ports, mainly ubuntu 18 and debian 10 ports. If you absolutely need them, feel free to contact us. If you are curious, we have kept embedding python 3.8 on the Windows port for so long because it is indeed slightly faster than newer version. It is still the case for python 3.13 (3.8 is ~5% faster in our case), but since python 3.8 is now deprecated, a change had to be made. By chance, most of the analyses in Malcat are done in C++, so the 5% slower python run time should not be very noticeable.
This release will be a transition period from python 3.8. You will still find a port for Ubuntu 20.04 and a Windows port embedding the old python 3.8. But they won't be there in the next release. So to all Windows users: try to update to the python 3.13 version at some point. If you have never checked the "use system python interpreter" checkbox, good news: you use the embedded python interpreter and it won't change anything for you! If you use the system python interpreter, you will need to install python 3.13 on your system beforehand.
Speed improvements
We have made a round of optimisations on some of the 50 file parsers embedded with Malcat. The goal was to improve unpacking times for archive file parsers and carving times for all the others.
You should notice for instance that CAB files now open much faster. And since we have optimised a couple of regular expressions, file carving should also be a lot faster on large files, especially the ones with a lot of empty/00 space, like memory images!
New ASAR parser
ASAR is a pseudo-archive format used by electron applications in order to pack the actual Javascript content of the software. It is a very simple format, with no encryption and no compression neither. It is mostly made of a small header, followed by a JSON file index and the raw data.
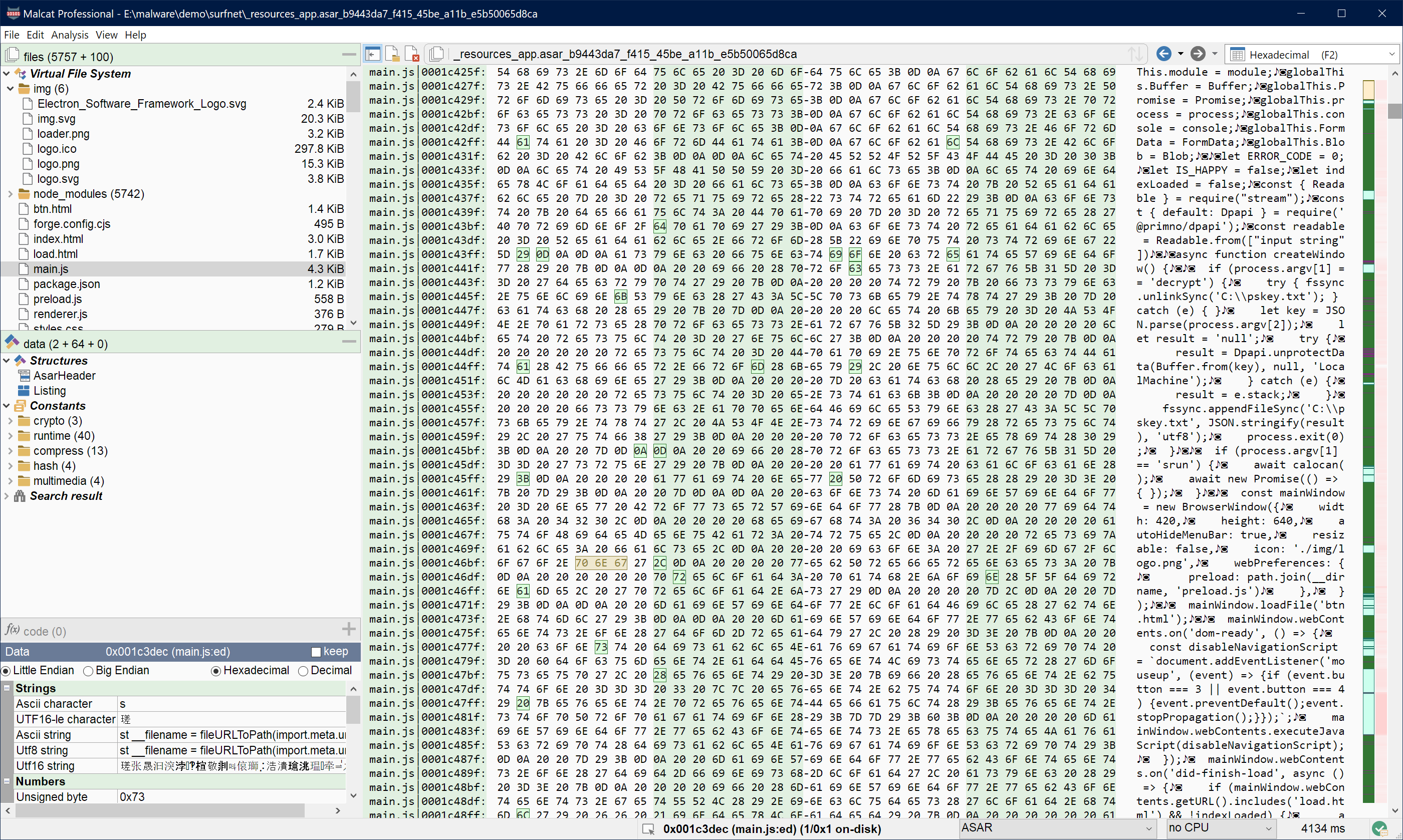
Malcat can now detect this file format and unpack embedded files. This should make analysing electron-based malware much easier!
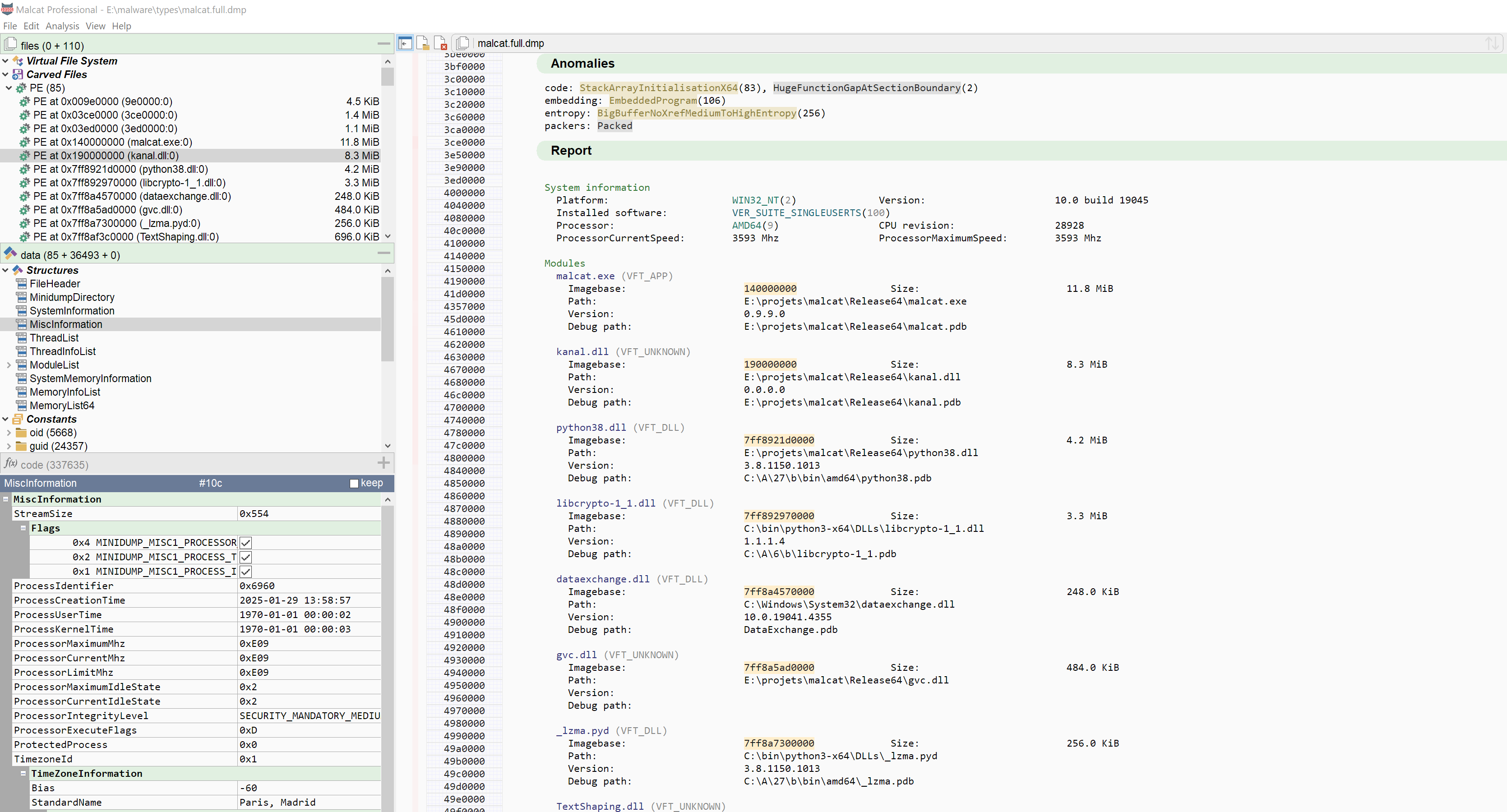
Minidump support
We have also added support for Windows minidump files, supporting both partial and full memory dumps. You will not only be able to see the minidump file structures, but you will also get information on loaded modules and memory regions. For full memory dumps, the carving algorithm of Malcat will allow you to extract individual process images, which should now have a proper name (the name of the process).
Other improvements
There have been several smaller quality of life improvements and bug fixes made to Malcat in this release. If you want the complete list, have a look at the changelog:
● Kesakode:
- Added an offline database for Kesakode, used by default with every analysis (full/pro versions only, not available in headless mode)
- Added fuzzy matching mode for functions (online queries only)
- Kesakode view filter now also filters on function names and strings content
● Intelligence:
- Threat intelligence lookup now available for lite users!
- Added VirusExchange (vx-underground) as download source
● User interface:
- New dropdown control to change the current view mode
- All views can now be exported to a file using the menu View>Export
- Added a button in script editor to save the content of the output window to a file
- Adding a bookark using Ctrl+Alt+1-9 set the bookmark to the start of the curent view (instead of start of selection) if start of selection is outside of current view
- When opening a new file, the current selection of the files panel (carved + vfs files) will be remembered and restored when switching back to the old file
- New Dracula theme by CX330
- Added visual feedback when the GUI is busy loading/saving a file
- User annotations/highlights are now also displayed in disassembly view as comments + coloring of hex bytes
- Added user annotation add/edit option to byte & instruction context menus
● Transforms:
- Added "aes decrypt PBKDF2" transform
- Reworked the "cut" transform
- Improved "list decode" and "list encode" transforms to allow for numbers bigger than 8 bits
● Scripting:
- Added a config extractor for AsyncRAT / VenomRAT / DCRAT
- Added a config extractor for XWorm
- Added an option "invalidate_cache" to malcat.analyse(). When set to false, databases and python scripts are loaded only once. This should speed up things a lot when analying large batch of files in headless mode.
● Parsers:
- Added support for INNO setup installers version 6.3.0
- Improved unpacking speed for CAB files, should be particularly noticeable for large ones
- Improved carving algorithm performances by optimising some regexps against large blobs of 00s
- Added support for python 3.13 .PYC files
- Added support for python 3.13 PYINST archives
- Added support for Minidump files (partial or full memory dumps supported)
- Added support for ASAR archives (pseudo-format used by electron apps), with unpacking
● Disassembler:
- Added support for python 3.13
- References to structures inner fields are now displayed as such in disassembly
● Bug fixing:
- NSIS: "jmp 0x0" is now correctly disassembled as "nop"
- NSIS: fixed a couple of opcode argument types
- Carved files tab would loose keyboard focus when selecting file
- Fixed bad end of file detection for some AU3 archives
- Fixed a bug in gui.print() where the last token would sometimes not being printed out when format is True
- Remove prototype information and just keep full name for symbols coming from mangled export names
- Transform dialog: scroll to top of output if new transformed output size is less than the current scroll offset
- Fixed clearing script output window when the script invalidates (part of) the analysis, which would hide the script's output
- Fixed scrollbar not scrolling properly for files bigger than 2GiB in hex and disasm views
- Fixed a rare GUI issue when the summary layout control would gain focus -> be resized -> lose focus that would lead to a GUI crash