Today we are happy to announce the release of version 0.8.0. This release, in addition to bug fixes and minor adjustments, brings the following improvements to Malcat:
- New RTTI analysis for MSVC-compiled binaries
- Improved disassembly for golang (1.16+) and python (3.9+) binaries
- Virustotal's VTGrep integration
- Updated Capa to version 3.2.0
- Added advanced selection in Malcat
- Color themes now available to lite edition users!
RTTI analysis and symbol demangling for MSVC-compiled binaries
Most C++ binaries embed RunTime Type Information. These structures are used by the compiler for dynamic_casts, typeid or correct exception dispatching. From a reverse engineer point of view they offer valuable information, such as object names and pointers to their virtual table. Malcat can now parse these structures for MSVC-compiled executable and extract most information:
- Virtual methods will be labeled as
<C++ type name>.#<index of method in vtable> - TypeDescriptor and Vtable will be identified and highlighted in the data view
- C++ types will be listed in the symbol view
This should make reverse engineering of MSVC C++ malware a lot easier. Below is a screenshot of what you will see:
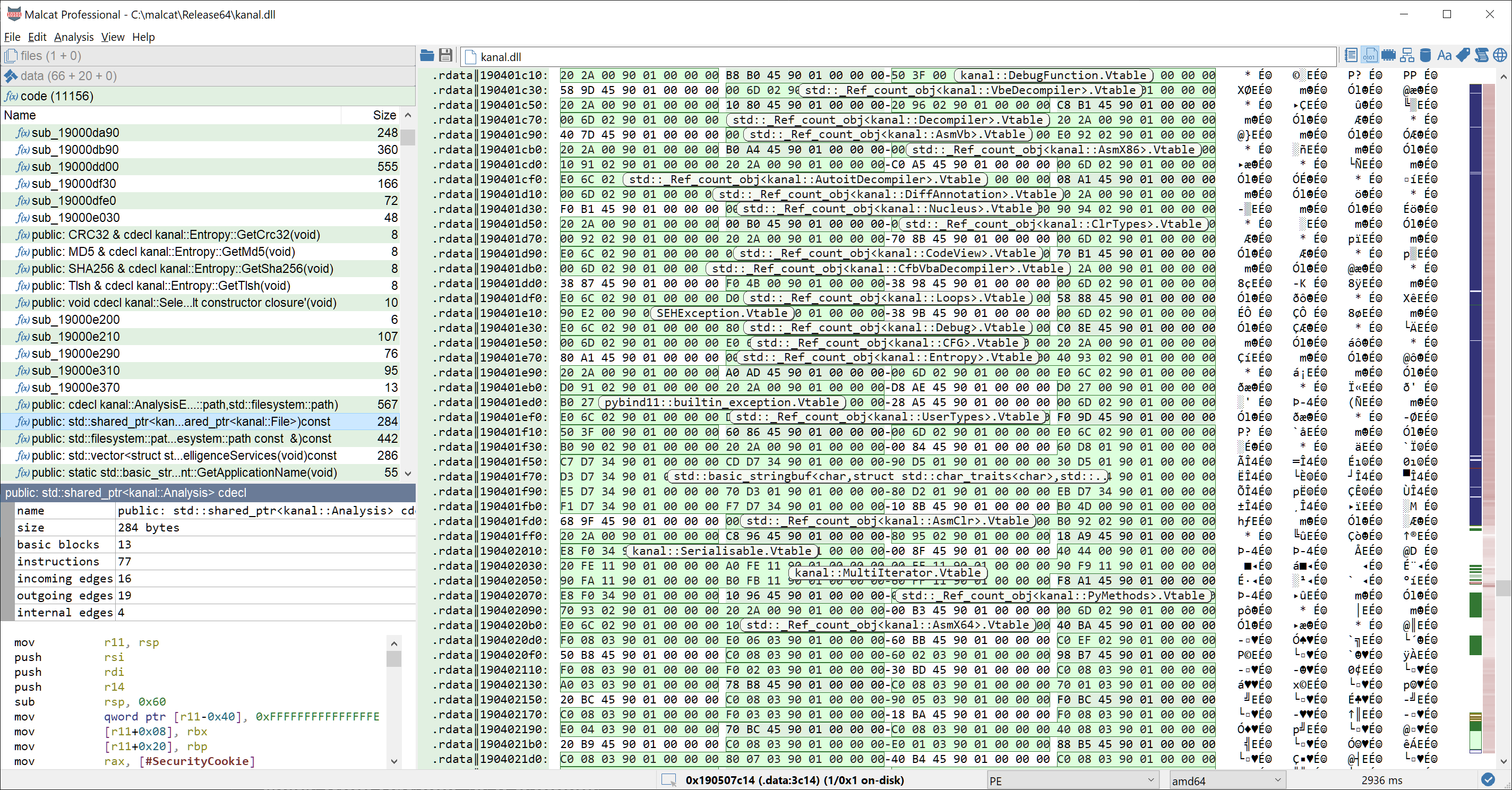
Since C++ type names are usually stored in their mangled form, we've also added a MSVC symbol demangler to Malcat. Virtual methods, as well as PE imports and exports names will be demangled for MSVC-compiled executables.
Disassembler improvements
Python 3.9 and 3.10 support
We have added support for python 3.9 and 3.10 disassembly. Malcat now officially supports disassembling python .pyc files for python 2.7, and 3.6 up to 3.10, which should cover most of python binaries nowadays.
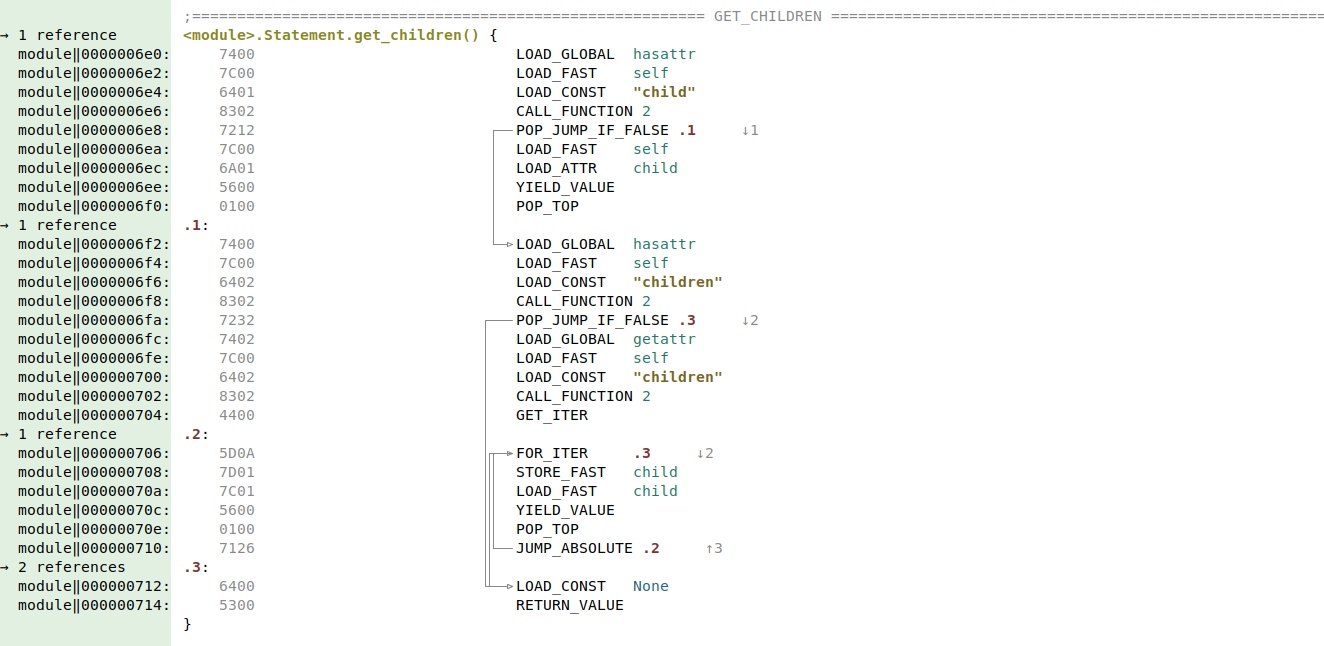
We have also updated the PyZ and PyInstaller file format parsers to add support for the new python versions. Exploring these file types in Malcat should be even easier: Malcat automatically reconstruct the Python magic header when extracting scripts extracted from those files.
Golang 1.16+ support
In order to print useful stack traces, the Golang compiler stores in each binary a PcLn table which contains file name, method name and line number information for every Golang methods in the program. Malcat makes great use of this information and can label Golang methods and properly identify most Golang strings (using heuristics).
But starting from version 1.16, Golang slightly changed the format of the PcLn table, which made Malcat miss this useful information for recent Golang binaries. Well, this problem has now been fixed. If you had issues analyzing recent Golang binaries, try reanalyzing with Malcat 0.8.0.
VTGrep integration
For some time, Virustotal introduced a great feature named VTGrep. VTGrep allows premium users to perform fast content searches in Virustotal's malware corpus. This feature is now integrated inside Malcat's own corpus view, in addition to the already-existing local corpus search. After selecting a string, a function or any arbitrary data range in the file, you will be able to list all files containing this pattern in Virustotal:
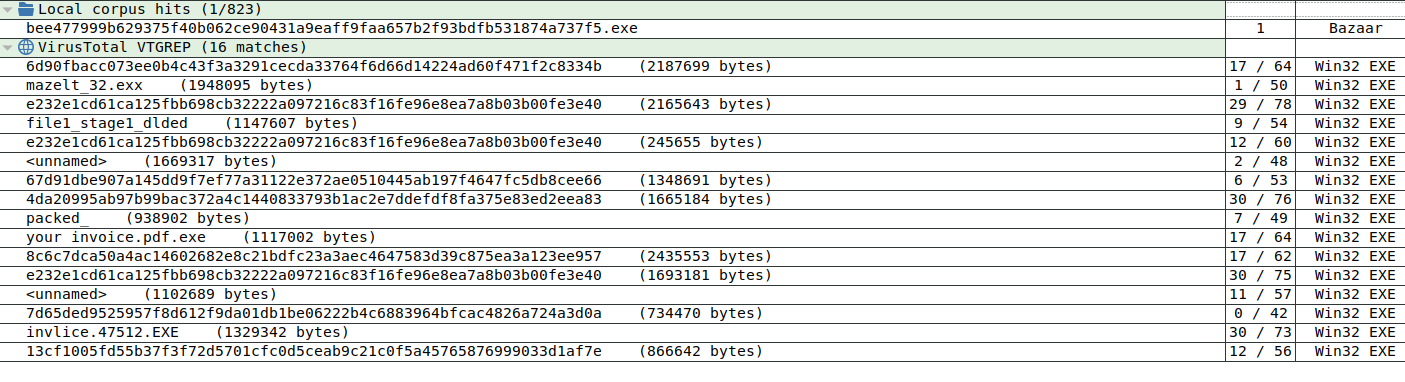
This features needs a premium VT key to work. If you don't, don't worry. You will still have access to Malcat's local corpus search: search any selected pattern against a set of local directories. It's a very useful feature to perform attribution, provided you have built a comprehensive malware set. You can also lower your false positive rate when creating Yara rules by scanning C:\Windows\system32 for instance.
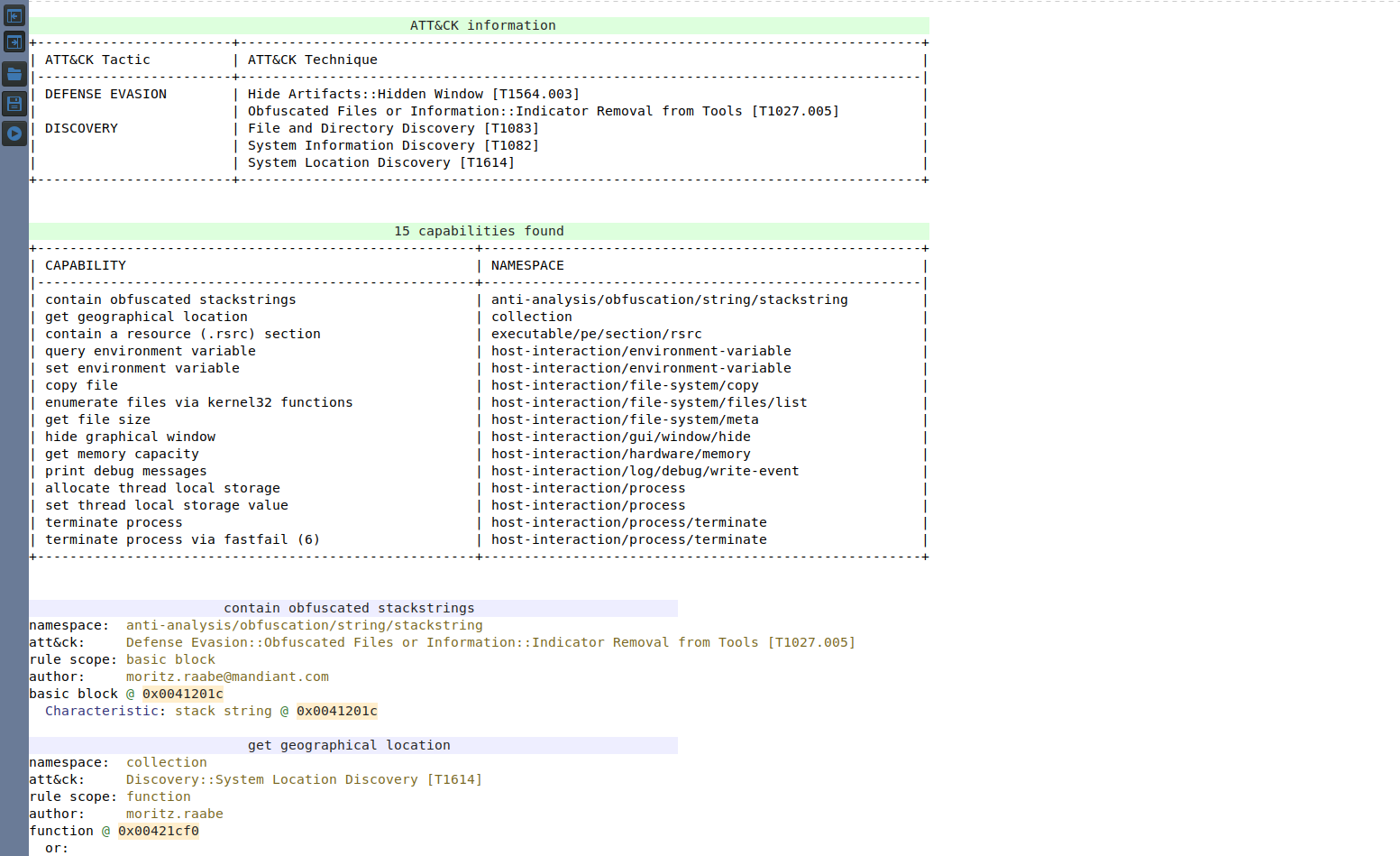
Capa updated to 3.2.0
We've updated Capa (and Malcat's bindings for Capa) from version 3.0 to the latest version: 3.2.0. Capa is a great tool to quickly assess a plain-text malware's capabilities. This new version includes additional rules, features and improved performance. To analyse a PE or ELF file with Capa in Malcat, just hit Ctrl+K or press the ► Run Capa button in the Summary view.
Advanced selection
Malcat now supports masks in selection. By using Ctrl+LeftClick or Ctrl+Shift+LeftClick on a selected bytes range, you can mask out part of the selection (full bytes, or even just nibbles). The mask will be used when performing the following actions:
- Masked out nibbles are replaced by
?when copying as hexadecimal to clipboard - Masked out nibbles are replaced by
?when adding hex bytes to the current Yara rule - Masked out nibbles are correctly ignored when searching in local and/or Virustotal's corpus
This feature is particularly useful when creating code signatures in Yara: you can mask-out absolute addresses, the mod/rm byte or stack offsets to make your signature more resilient to changes.
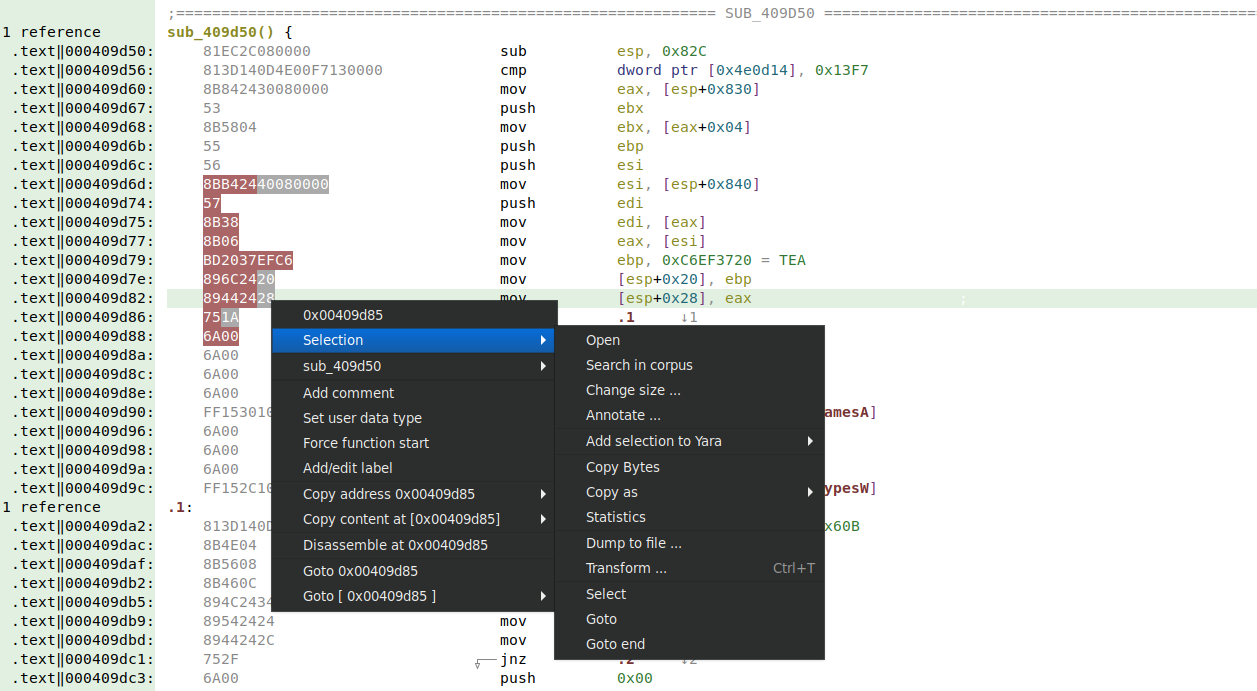
In the future, we plan to add a magic-select action to Malcat for code: partial or full function bodies will be intelligently selected depending on user preferences.
Color themes make it to lite edition
If you are a free user, you will notice that you now have access to color themes in Malcat. Since the first release, we got some complaints about the default lite theme lacking contrast. So you will now be able to chose the theme that fits your eyes the best. In addition, the new default theme is now "vs", which is brighter and has more contrast. If you are unhappy with it, the old default theme "lite" is also available.
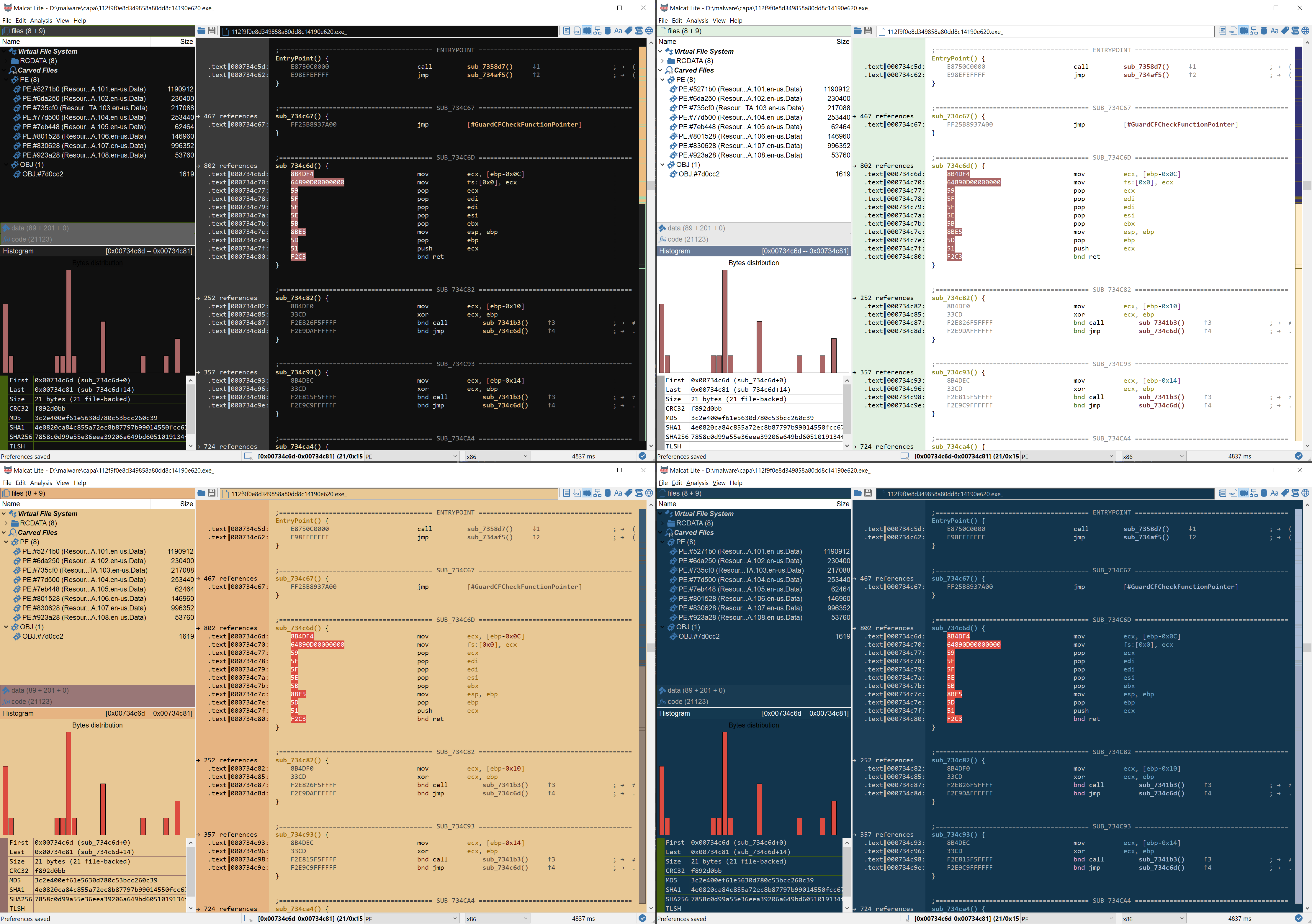
If you are still unhappy about the color schemes, we will soon publish a guide on how to create your own. You can also start playing with/adding ini files in data/themes to design your own custom theme.
Full changelog
Here is the complete changelog of this release:
● Lite edition now has access to visual themes!
● Improved analysis of MSVC-compiled binaries:
- Added RTTI parsing (label virtual functions and identify RTTI structures)
- Added symbol demangler (for RTTI and exports/imports)
● Updated Capa to version 3.2.0:
- added missing features to malcat's Capa bindings
- fixed multiple issues in Malcat's capa bindings
● Python:
- Added support for python 3.9 and 3.10 disassembly (so we support 2.7 and 3.6-3.10 now)
- Fixed minor issues in PYINST and PYZ file parsers
● Improved Golang symbols and strings identification for go 1.16 and newer
● Added support for VTGrep (needs a VT premium API):
- "Search in corpus" now searches selected pattern in virustotal in addition to the local corpus
- Added VTGrep-related options in Options dialog
● Advanced selection: masked-out nibbles in selection (Shift+Click) are now supported
- masked out nibbles are replaced by '?' when copying as hexadecimal to the clipboard
- masked out nibbles are replaced by '?' when adding hex bytes to current Yara rules
- masked out nibbles are correctly ignored when searching in corpus
● Misc:
- Disassembler now displays strings using user's selected charset
- Disassembler now displays numbers and addresses using user's selected base (Ctrl+D)
- ELF: parse .comments sections for metadata
- PDF: added a few anomalies
- Options dialog now warns you with a message box if an option change requires a restart
● Bug fixes:
- Xref analysis would hide data xrefs if options "CFG: don't follow data refs" was checked
- GUI would sometimes hang on ubuntu18 when running a python script