Today we are happy to announce the release of version 0.8.4! In addition to the added support for Ubuntu 22.04 (or similar python 3.10-based distributions), you can expect the following improvements:
- Identify API hashes used in shellcodes and loaders using our constants database
- Added support for Cobalt Strike configuration files
- Additional parsing of some OLE streams
- Improved LNK parsing and anomalies
- The usual: bug fixing and updating of the Yara and anomalies rules sets
Ubuntu 22.04 support
It was time, but we now provide binaries for the recent Ubuntu 22.04 distribution! The binaries should also be compatible with other python 3.10-based linux distributions. If you own a purchased version of Malcat and want to test on ubuntu 22, just visit the download link you got in the email: the ubuntu 22.04 archive has been added to the bundle. For free user, it is available in the download page.
API hashes identifications
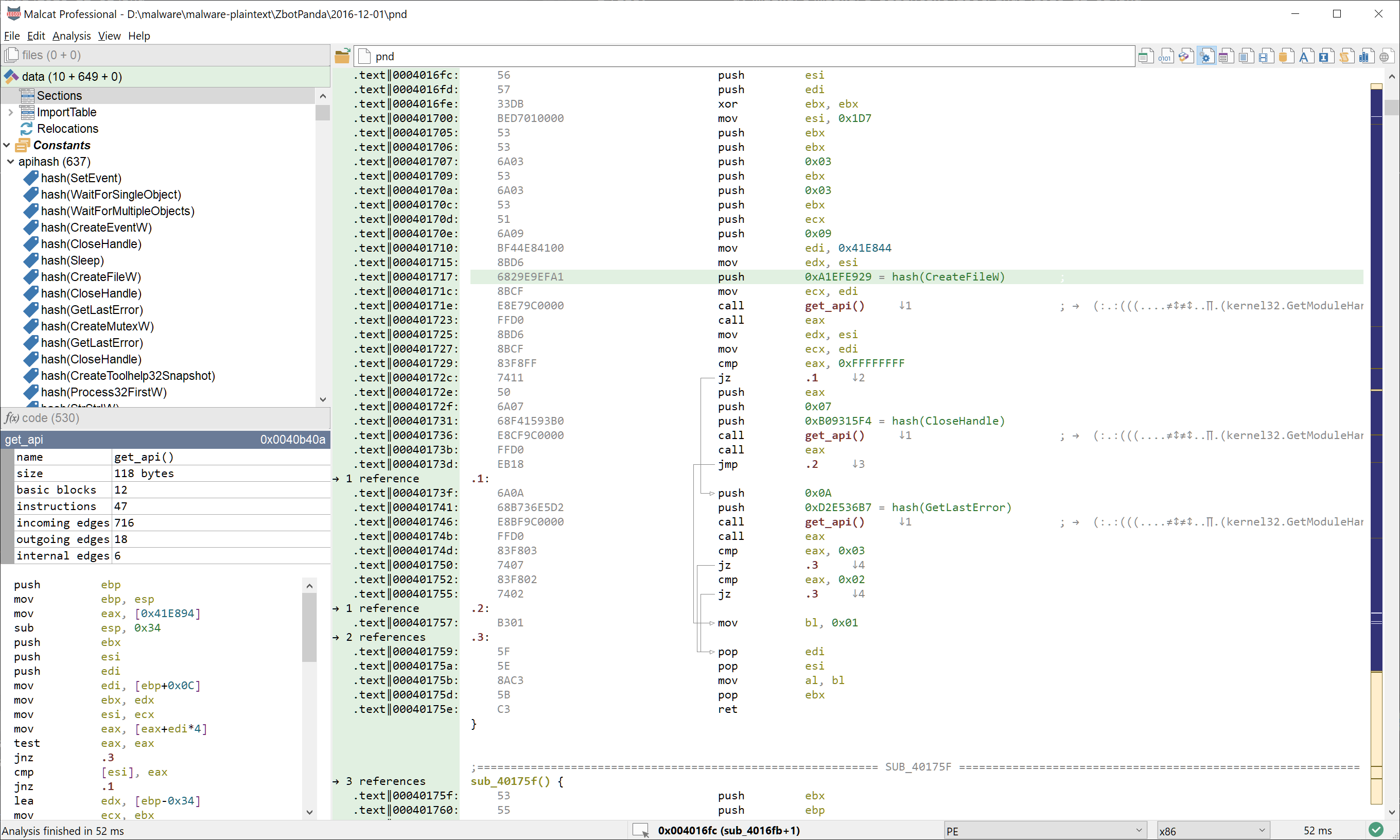
Shellcodes or malware loaders importing API by hashes can sometimes be a pain to analyse. So we've decided to make it a bit easier by adding more than 400000 API hashes to Malcat's constants database. These are API names from standard Windows DLLs hashed using the most common API hash algorithms found in the wild. Our work was inspired by Kaspersky's great IDA plugin. From now on, these hashes will be automatically detected by Malcat and a hint will be displayed alongside hash constants in both the disassembly and decompiler views.
Note that if hash constants are obuscated (for instance if they are computed dynamically using multiple arithmetic operations), they may still be identified in the decompiler view, provided the decompiler could perform proper constant propagation.
Adding so many 4-bytes constants to the constants database can add some unwanted noise to the analysis though, as sometimes constants are just constants and not hashes. So in order to lower the number of false identifications, we have implemented the following restrictions:
-
Only APIs of the following DLLs are considered:
- kernel32.dl
- advapi32.dll'
- msvcrt.dll
- netapi32.dll
- ntdll.dll
- psapi.dll
- shell32.dll
- shlwapi.dll
- urlmon.dll
- user32.dll
- winhttp.dll
- wininet.dll
- ws2_32.dll
- advpack.dll
-
Hashes are only identifed when part of a mov / add /sub / push or cmp operation
- Hashes having more than 1 byte set to zero are ignored (they lead to the most false positives)
- Hashes which are also valid virtual addresses for the analyzed program are ignored
These rules may seem a bit strict (and they are, a few hashes won't be identifed), but we've found that they've drastically decreased the number of false hash identifcations in our test set, to the point where it's not a bother anymore. Most of the time, shellcode include several API hashes. Even if we miss one, the most important thing is to point the user to the right direction. Missing hashes can always be googled. Wrong matches on the other hand are always annoying.
Cobalt Strike configuration files
Cobalt Strike is propably the most wide spread remote access tool to date, and is used by a large number of different threat actors. The first program landing on a victim's computer in charge of the initial infection is called a beacon. This program always embeds a binary configuration blob in its data section which holds valuable information, such as the url of the command and control server and how the beacon should communicate with it.
The format of this structure has already been reverse engineered in details. We have thus added a file parser for Cobalt Strike configuration files into Malcat as well. The parser will automatically identify and parse plain text configurations, such as the ones found in memory dumps.
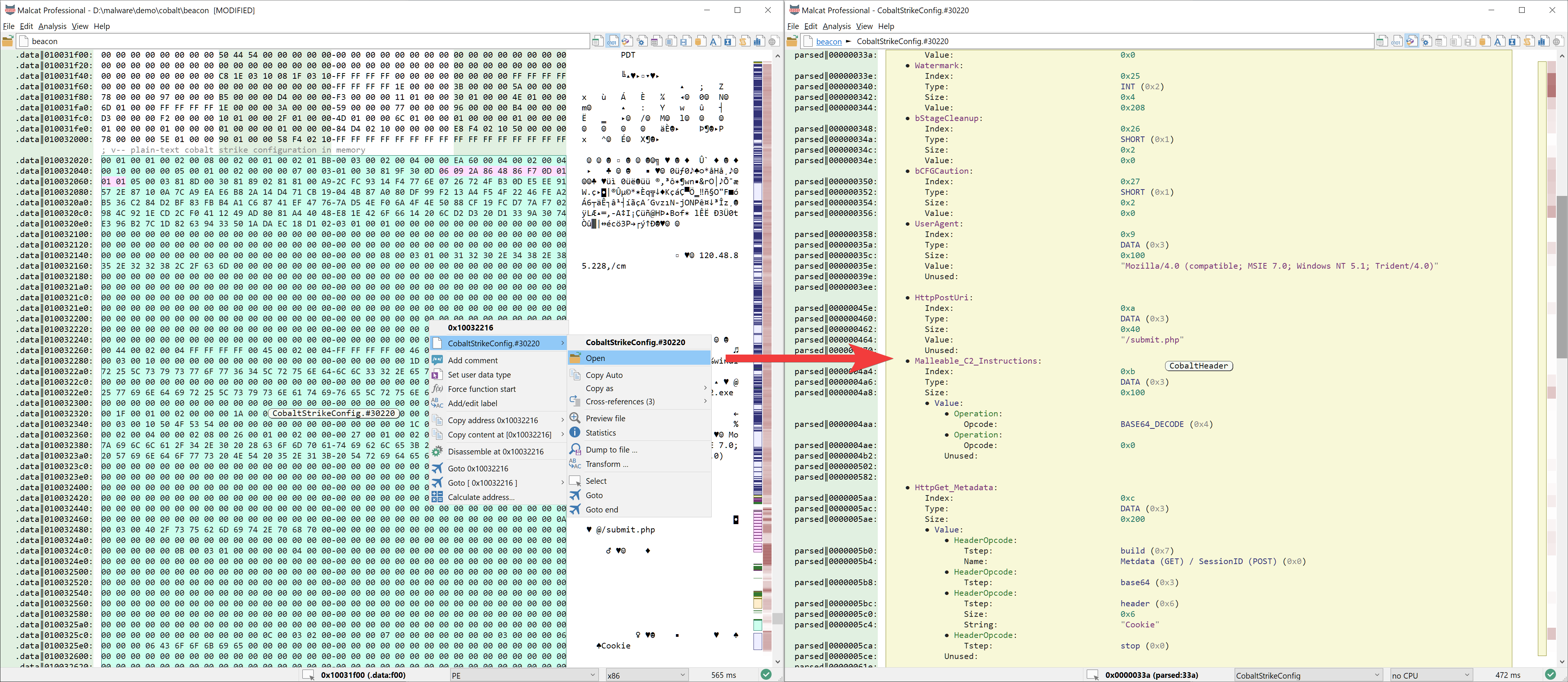
If you are analysing the original beacon file as found on disk, the configuration is stored encrypted using a single one-byte XOR key in the .data section. Decode it using Malcat's transform, reanalyse the file (Ctrl+R) and voila, you can read the beacon configuration.
Additional OLE stream parsing (CVE-2022-30190)
OLE files (also know as CFB files) are used by Office in a number of different ways. Recently, a number of RTF documents exploiting CVE-2022-30190 (Follina) were found including hyperlinks in the form of OLE objects. While Malcat can analyse OLE objects with ease, the hyperlink information is stored inside a stream named Ole whose binary structure is not parsed.
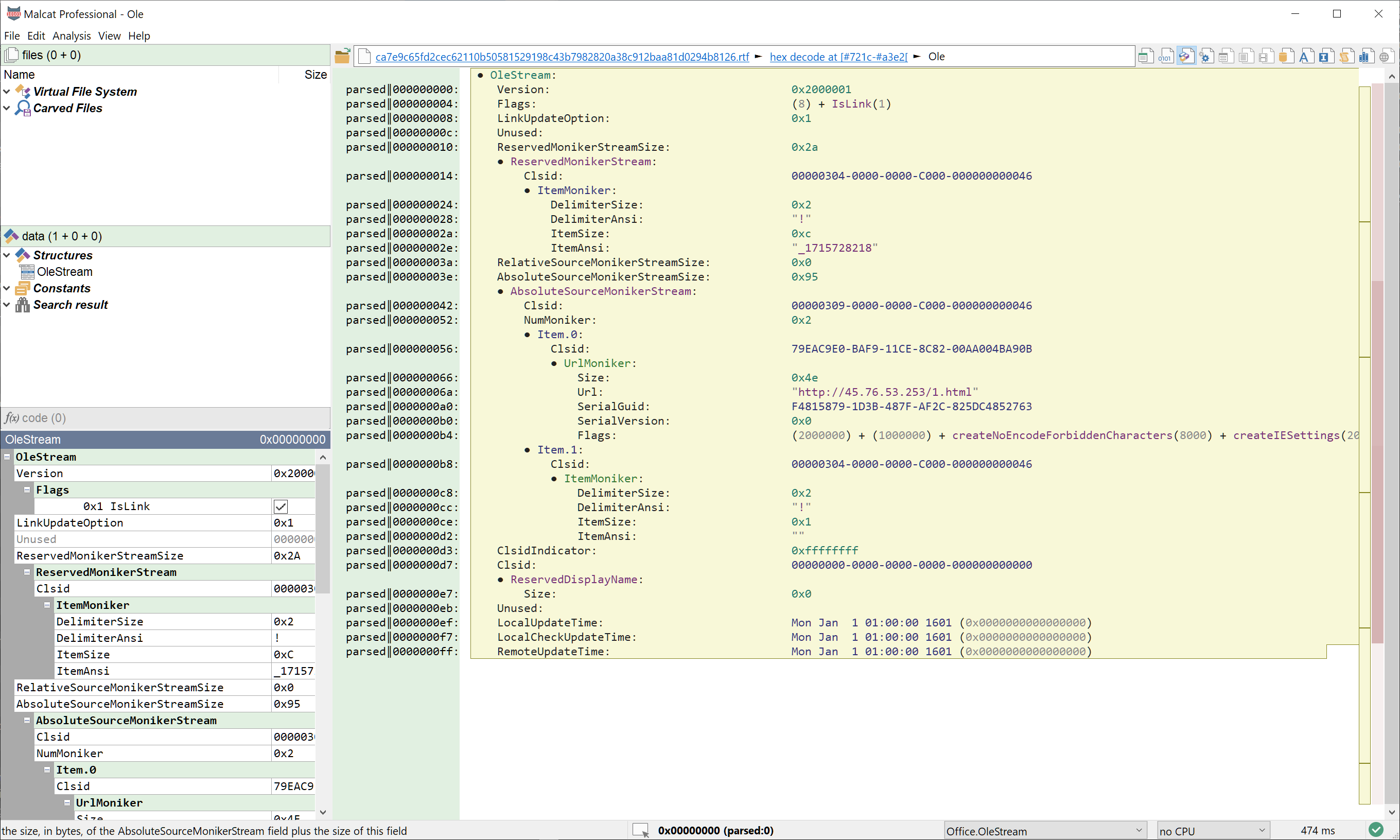
Starting form now, Malcat can analyse the following OLE streams (in addition to the already supported ones like /Word or /SummaryInformation):
- \x01Ole stream
- \x01CompObj stream
- \x01Ole10Nativestream
- \x03ObjInfo
This should cover most of the streams used by Office when embedding OLE documents.
Full changelog
Here is the complete changelog of this release:
● Ubuntu 22.04 package!
● Constant analysis:
- Optimized constant search a bit
- Added ~413000 common Windows API hashes (using different hash algorithms found in malware) to api.csig
● Cobalt strike:
- Added a file parser for CS plain-text configurations (useful when analysing memory dumps of beacons)
- Added summary template
- Malleable opcodes disassembly
● NSIS:
- Improved support for unicode scripts, fixed section unicode bug
- Improved summary template
- Added FileWriteW and FileReadW opcode support to the disassembler
● LNK:
- Greatly improved the summary template
- Added some enums for better readability
- Added and improved existing anomalies
● CFB/Ole:
- Parsing for the "\x01Ole" stream object
- Parsing for the "\x01CompObj" stream object
- Parsing for the "\x01Ole10Native" stream object
- Parsing for the "\x03ObjInfo" stream object
● Scripting:
- Script output window has now horizontal scrollbars and do not wrap (revert to old behavior)
- Improved PE/speakeasy_pe_unpack.py script: better dump choice
- malcat.struct: You can now iterates through arrays, structures and bitvectors using python slices
● User interface:
- When editing bytes in data view, invalid character input is now notified in statusbar and not via a messagebox (which would cause editing session to end)
● Bug fixing:
- Fixed file differences sometimes needing a refresh to be displayed
- Fixed in diff mode, secondary analysis would be hidden after help display
- Fixed saving sub-files using save dialog: only the .malcat project would be saved
- Fixed undo-redo of file operations: file would sometimes not be seen as modified