0.9.10 is out: CFG recovery, MIPS & UI improvements
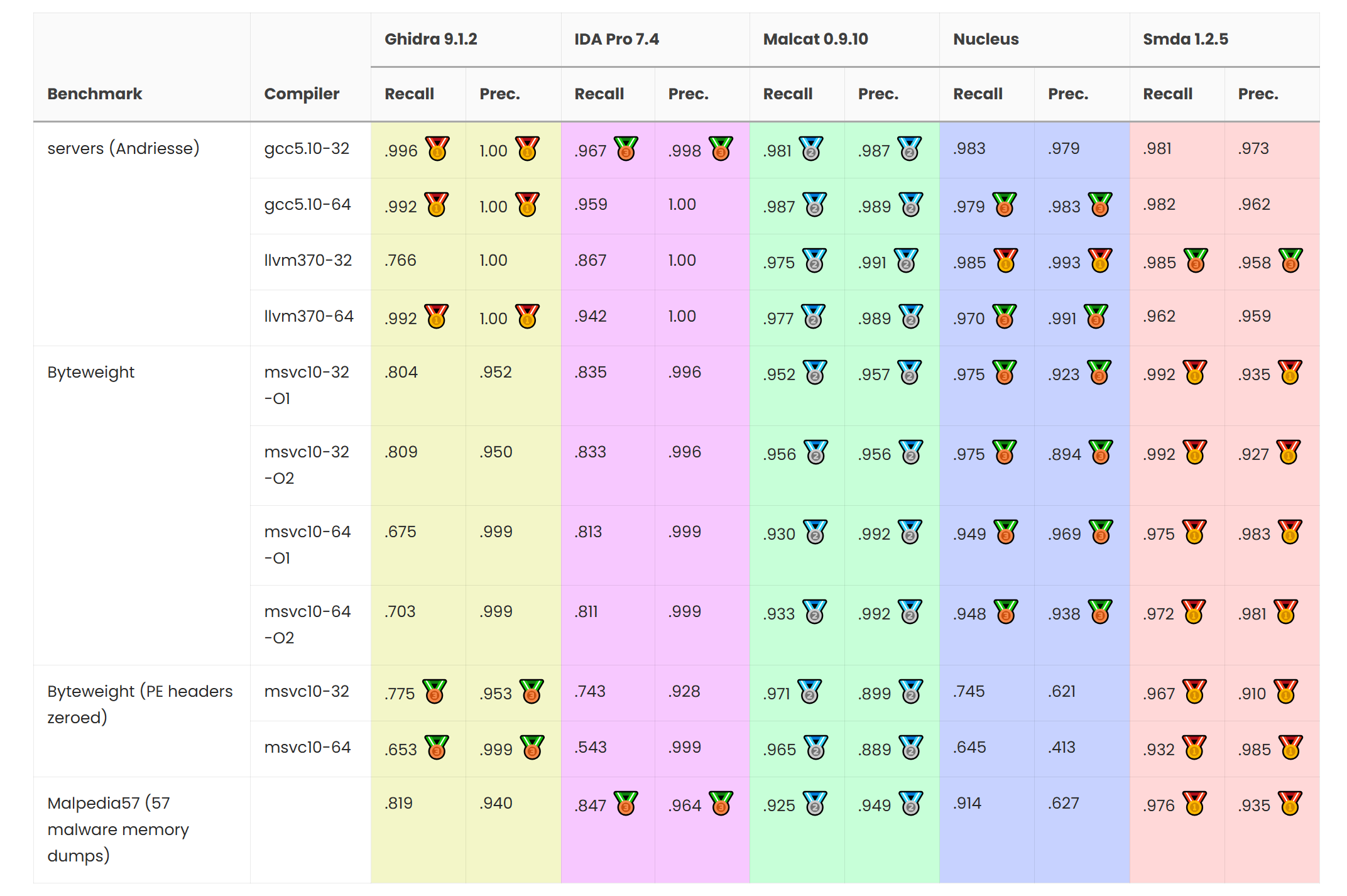
Malcat version 0.9.10 is out! In this release, we have improved Malcat's CFG recovery algorithm and compared its performances against other reversing software. A new CPU architecture (MIPS) has also been added and multiple improvements to the decompiler interface in Malcat were made. Last but not least, several QoL changes have been made, from a new preview popup in data and code views to new scripts/transform and an more extensive corpus search.
0.9.9 is out: Offline Kesakode, python 3.13 & UI
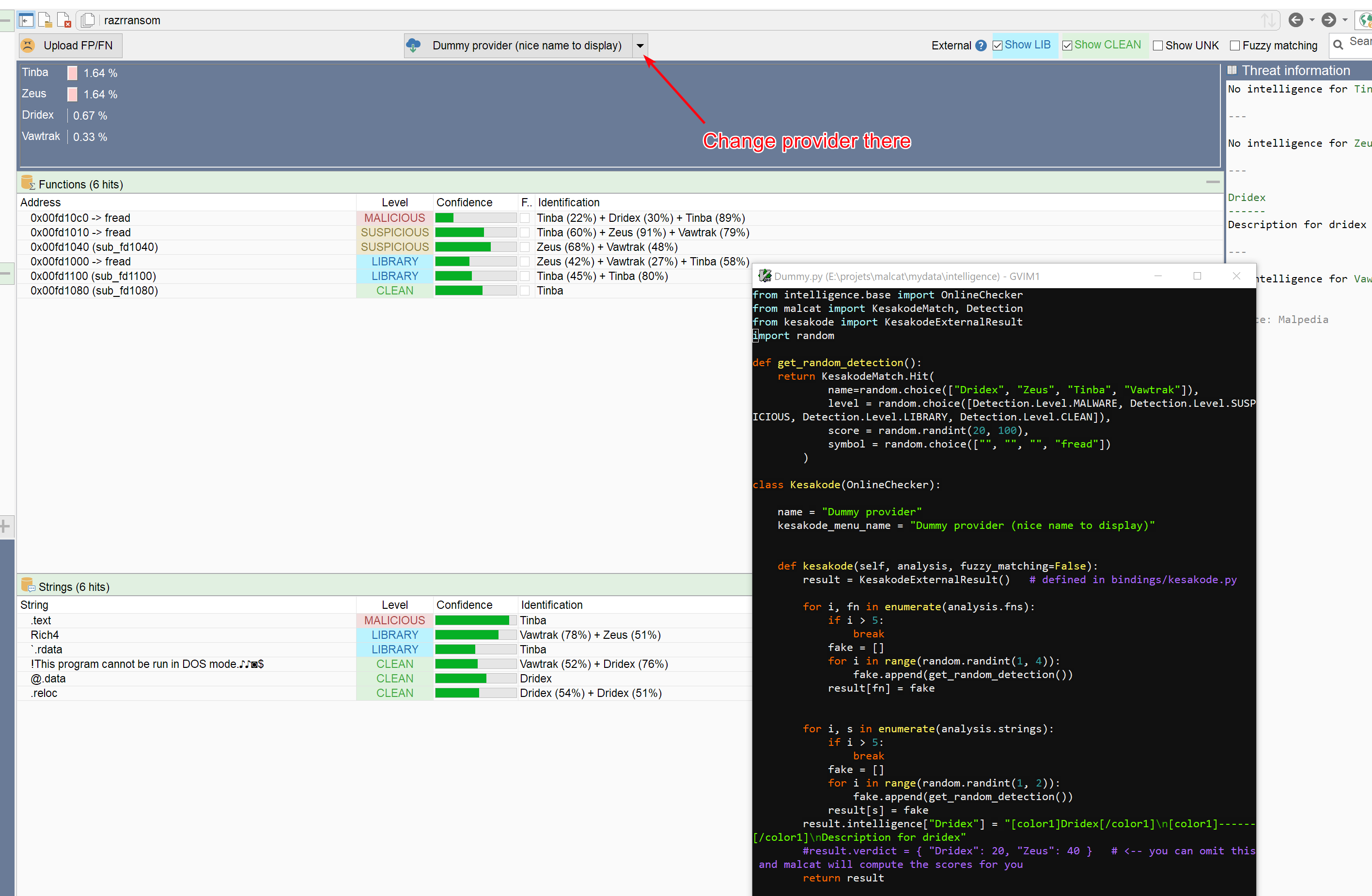
Malcat version 0.9.9 is out! Say hello to the offline version of Kesakode, which lets you identify malware even faster and without uploading any hash! You will see also several UI improvements, python 3.13 support and a couple of optimisations regarding file parsers. Last but not least, the threat intelligence features are now available in the lite edition!
0.9.8 is out: Scripting & QoL improvements
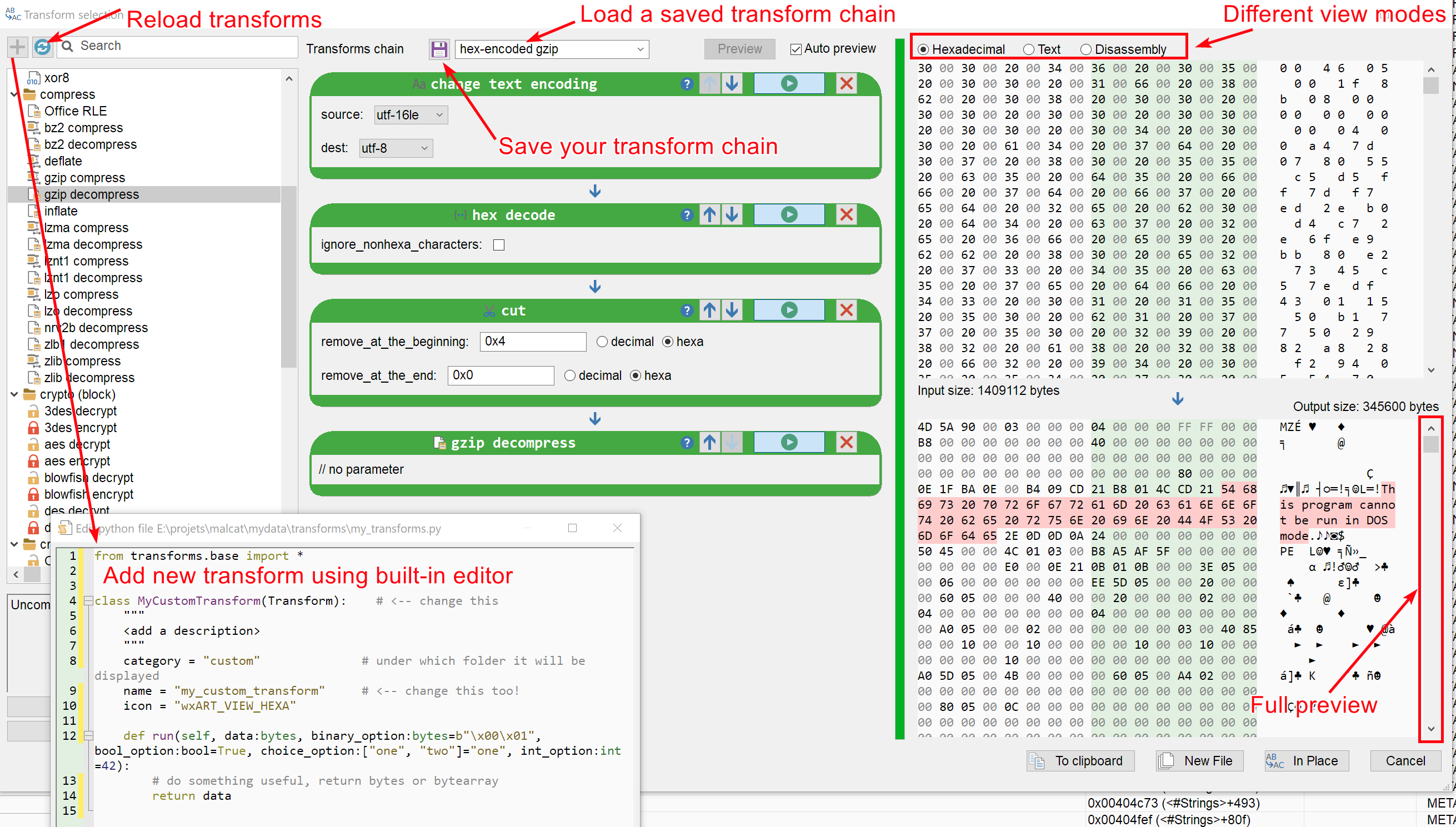
Malcat version 0.9.8 is out! You will find many quality-of-life improvements, such as an improved transform dialog, better scripting support, better data preview and many more.

Malcat tip: fast unpacking of RTF payloads
In this short tutorial, we will see how to extract binary payloads from RTF documents using Malcat. We will then proceed to emulate a shellcode for CVE-2017-11882 and extract the download link.
0.9.6 is out: Kesakode malware identification!
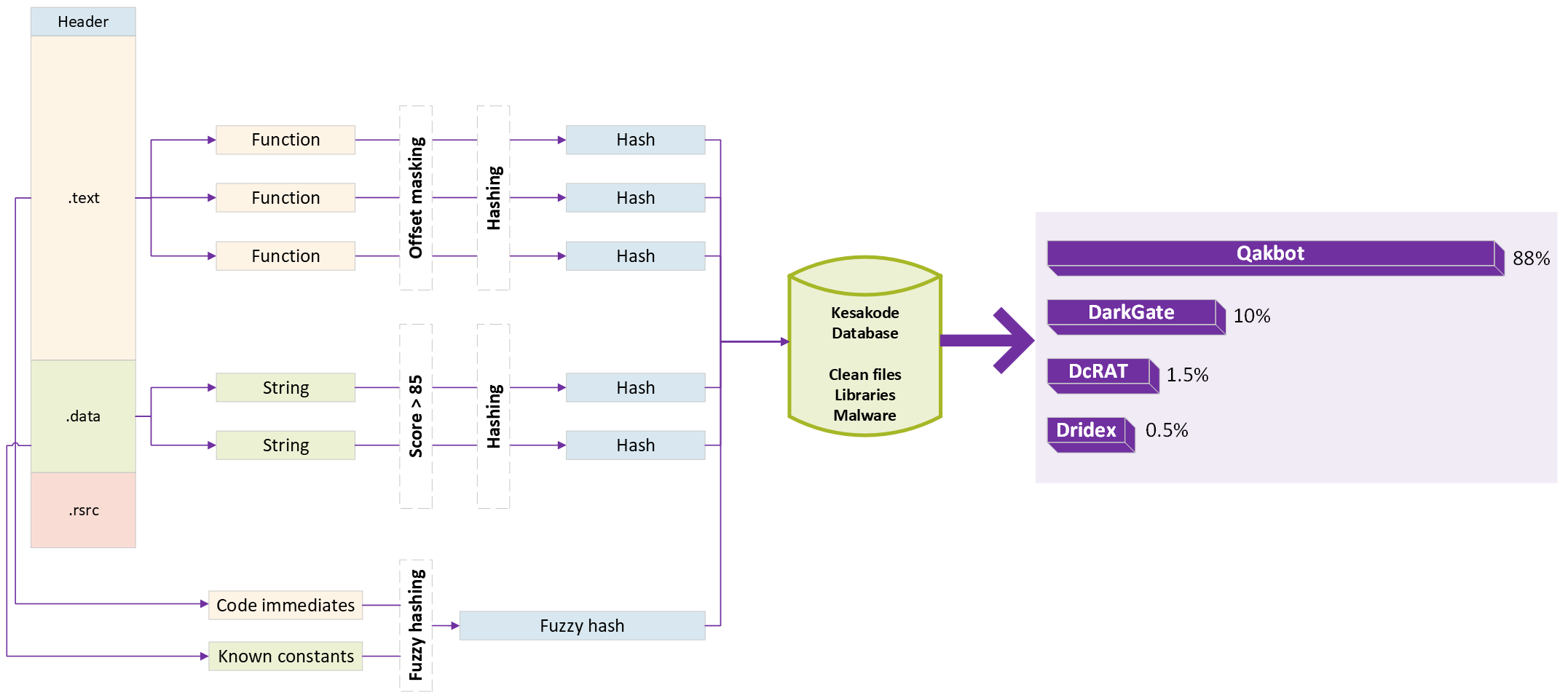
Malcat version 0.9.6 is out! We have launched our brand-new online hash lookup service: Kesakode. You'll be able to identify (unpacked) malware, see similarities between malware families, write better Yara rules and speed up your reverse engineering game!
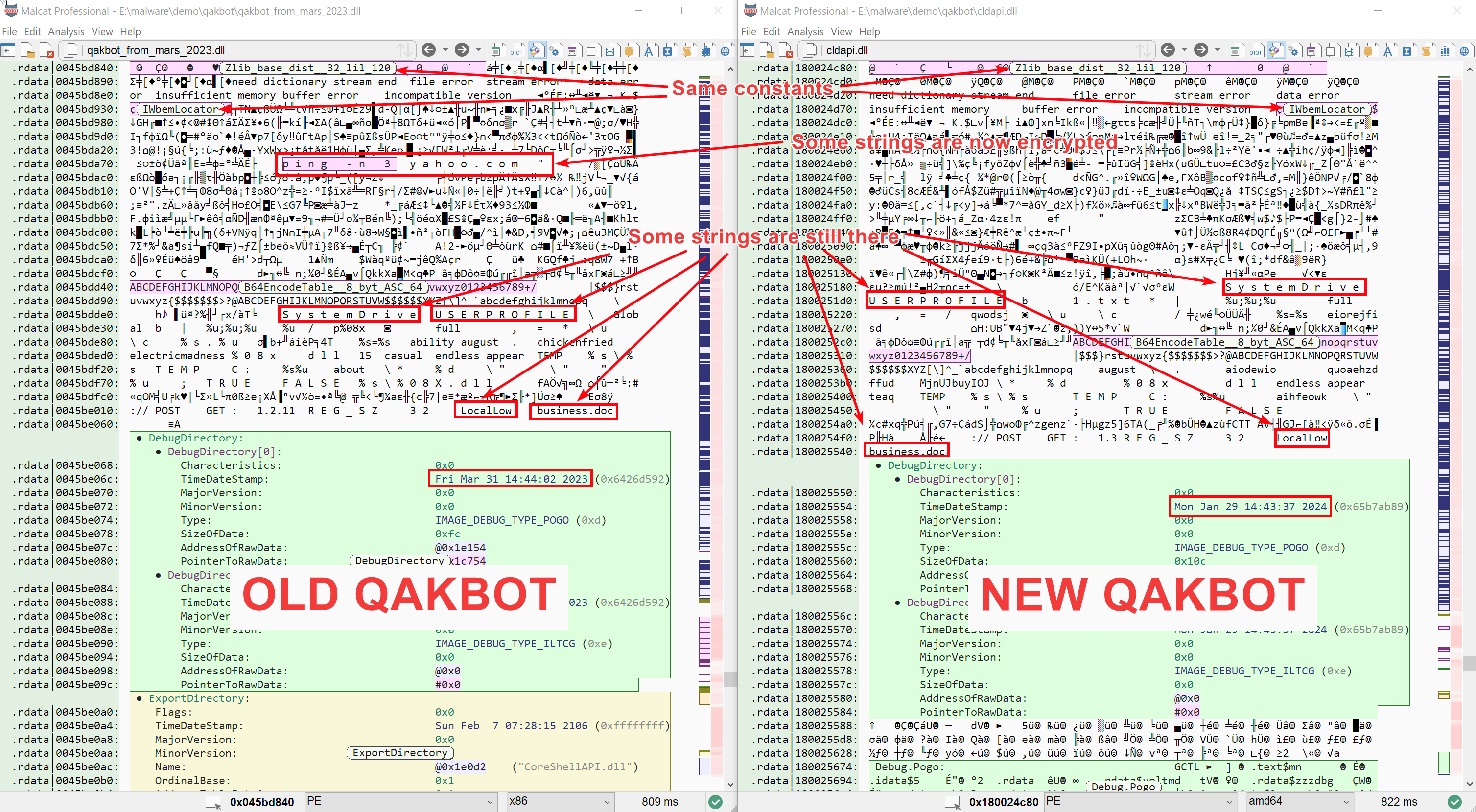
Writing a Qakbot 5.0 config extractor with Malcat
Starting from a (backdoored) MSI installer, we will unroll the infection to chain to get the final Qakbot sample. Sticking to pure static analysis, we will then decrypt Qakbot's configuration and finally write a script in Malcat to automate the process.
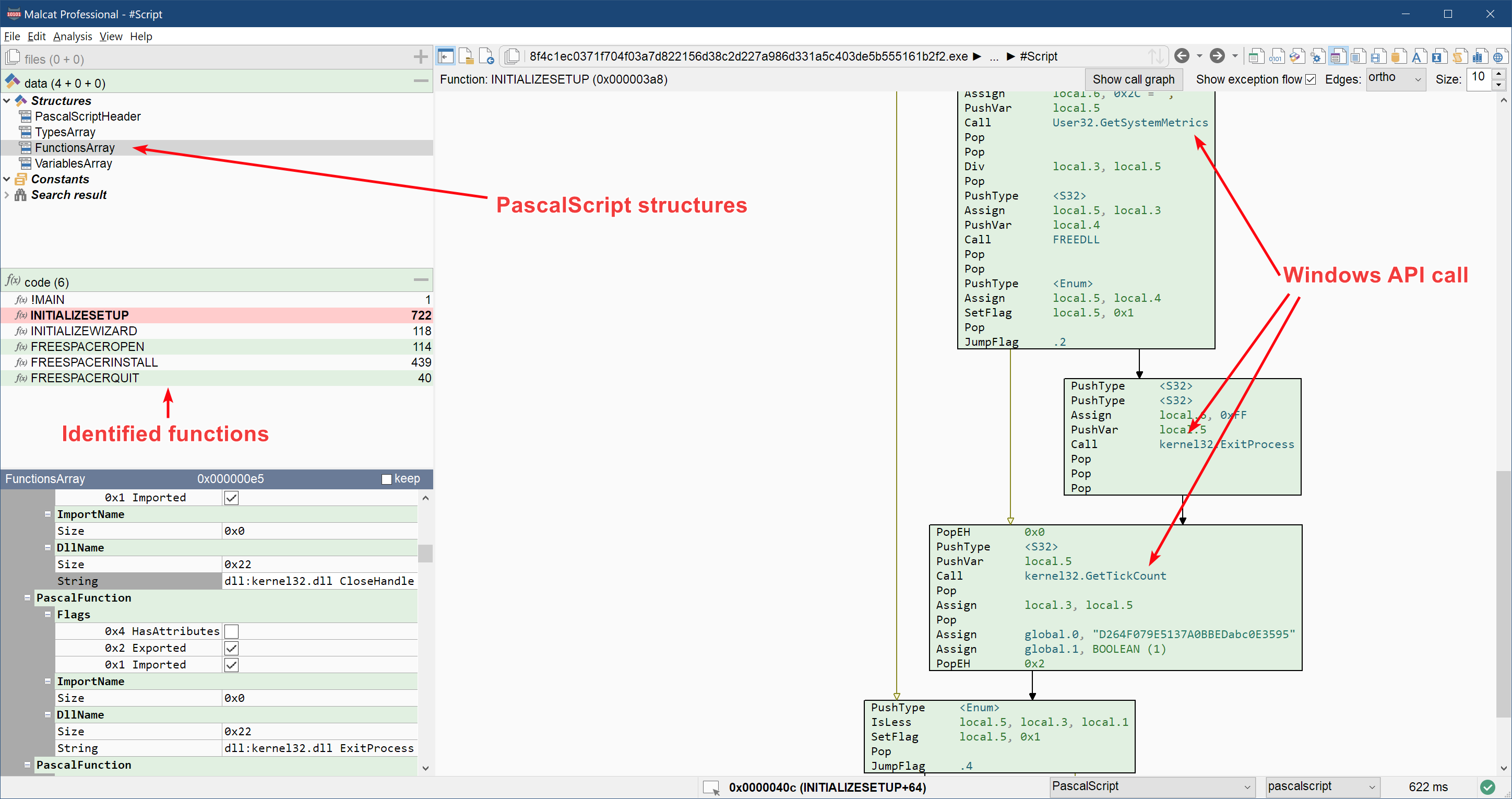
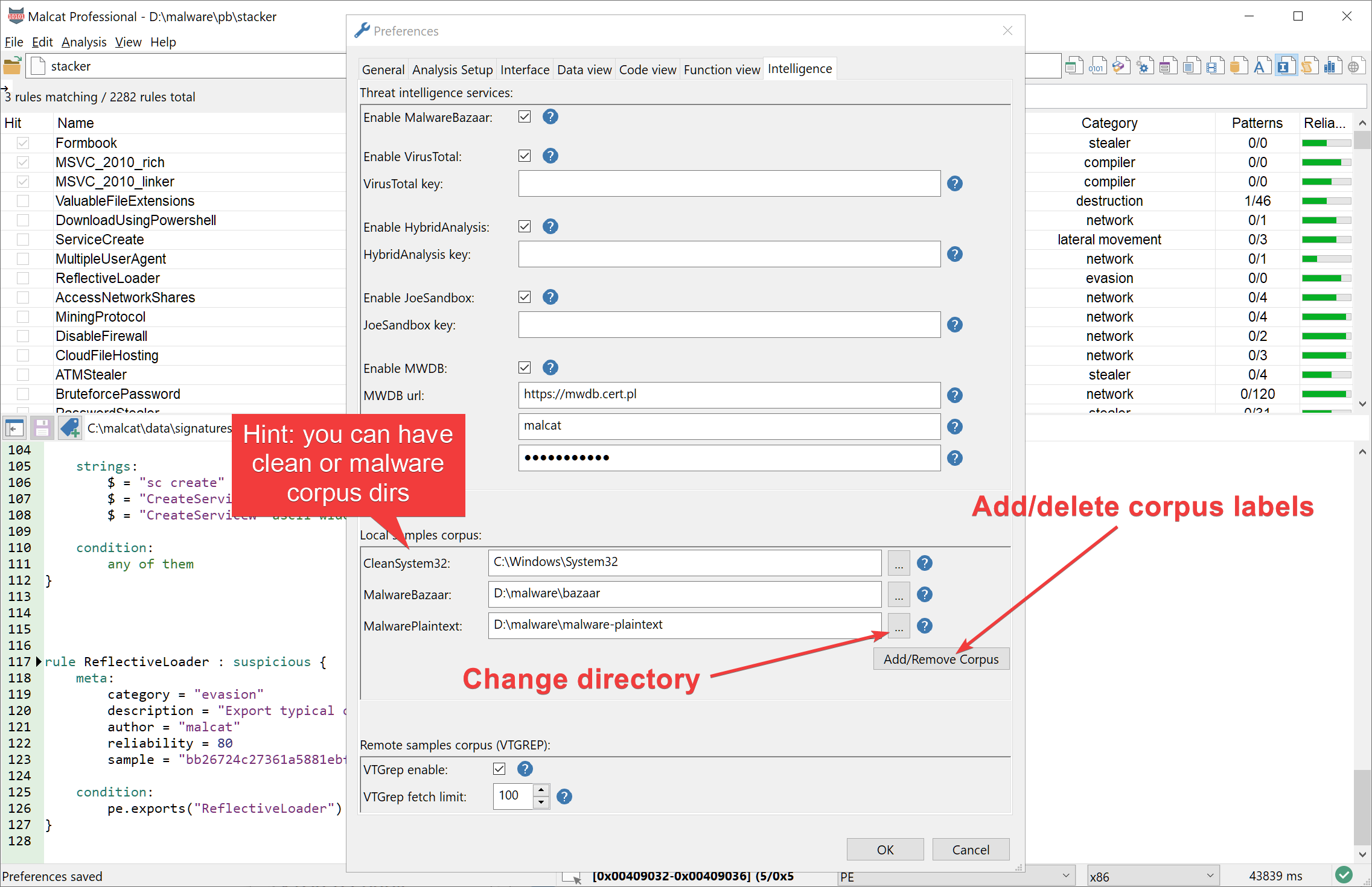
0.9.5 is out: InnoSetup, new GUI dialogs, threat intel and more
Malcat version 0.9.5 is out! We have added support for InnoSetup installers, added binaries for Debian 12 build, made several UI improvements and expanded the threat intelligence providers

Shrinking a PYC file to its minimum
In this tutorial, we will see how to use Malcat editing capabilities to reduce the size of a python bytecode file (.pyc) to its minimum. This article is the write-up for our Binary Golf Grand Prix 4 entry.
0.9.4 is out: Ubuntu 23 support, python 3.11 and magic masking
Malcat version 0.9.4 is out! We have added support for Ubuntu 23, a python 3.11 disassembler, magic masking selection for more robust code signatures and many QOL improvements
0.9.3 is out: python, python, python (and firmwares)
Malcat version 0.9.3 is out! Enjoy headless python scripting, extended python bindings, improved rust support, 3 new firmwares parsers and many QOL improvements
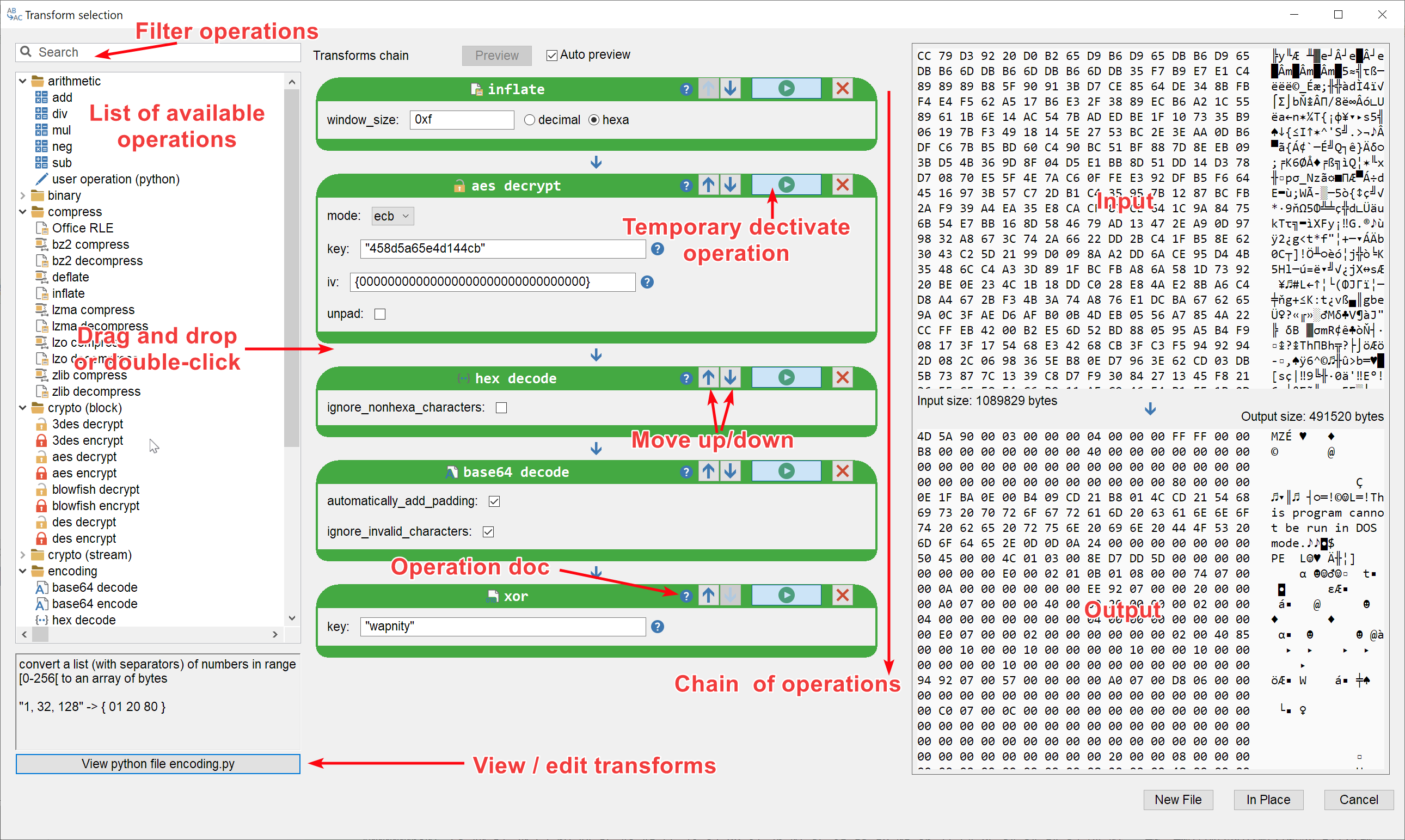
New release: 0.9.2
Malcat version 0.9.2 is out! You can now easily apply chained transformation on data, open and deobfuscate script files and analyse CHM files. The user interface also got improved with many quality of life improvements.
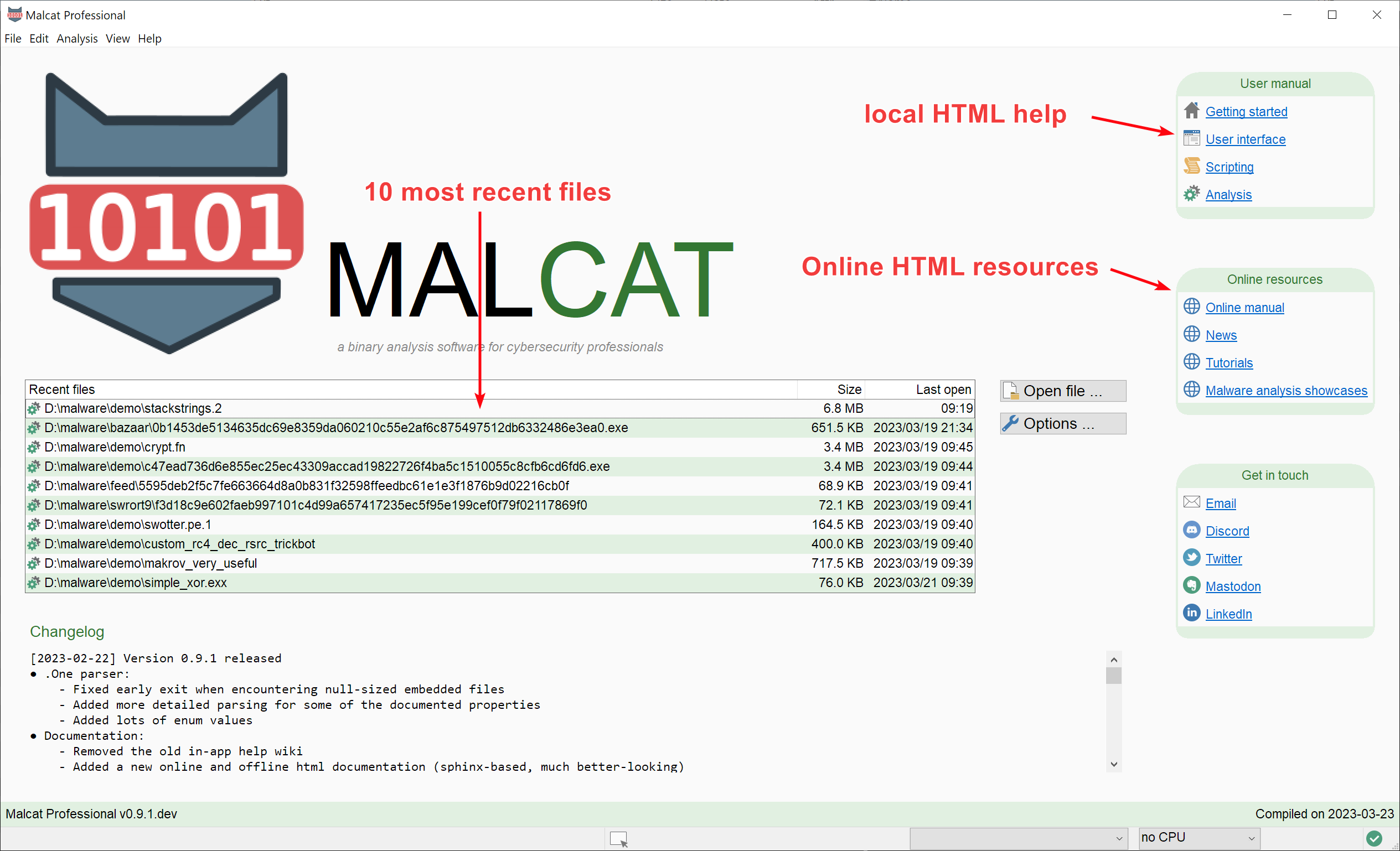
New release: 0.9.1
Malcat version 0.9.1 is out! Enjoy a new sphinx-based documentation, a proper startup screen, improved .one and .cab support and better O.S integration.
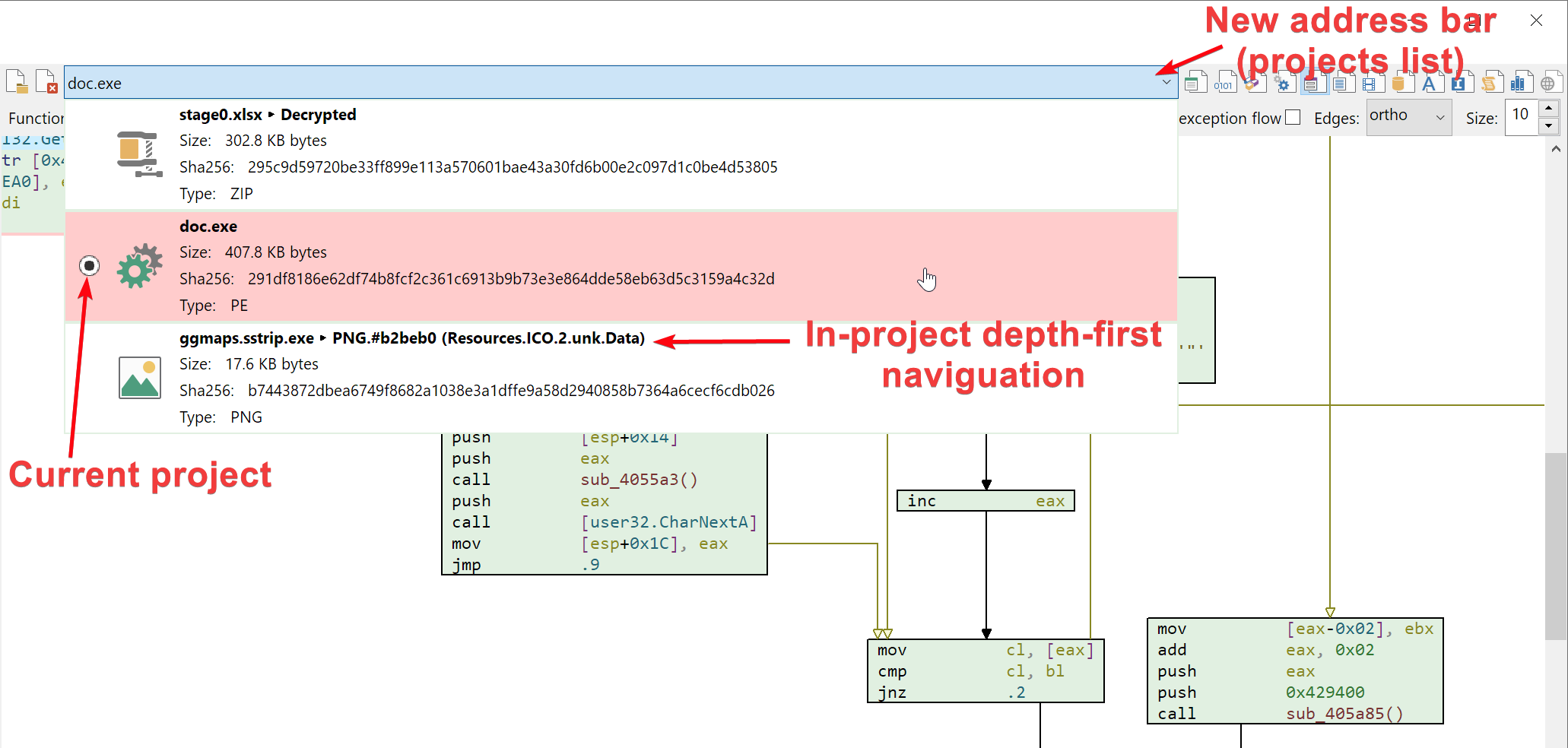
New release: 0.9.0
Malcat version 0.9.0 is out! You can now open multiple files in parallel, scan for FLIRT signatures, analyse onenote files and enjoy quick bookmarks handling, in addition to the usual bug fixing and various QOL improvements
New release: 0.8.5
New version 0.8.5 is out! Enjoy the new "big file" mode, an improved disassembly view, advanced Yara integration and VHD + FAT filesystem support, as well as many other improvements.
LNK forensic and config extraction of a cobalt strike beacon
Windows shortcut files can contain valuable data. We will see how to extract the most information out of a .lnk downloader and will manually extract the configuration file of the final cobalt strike beacon using malcat
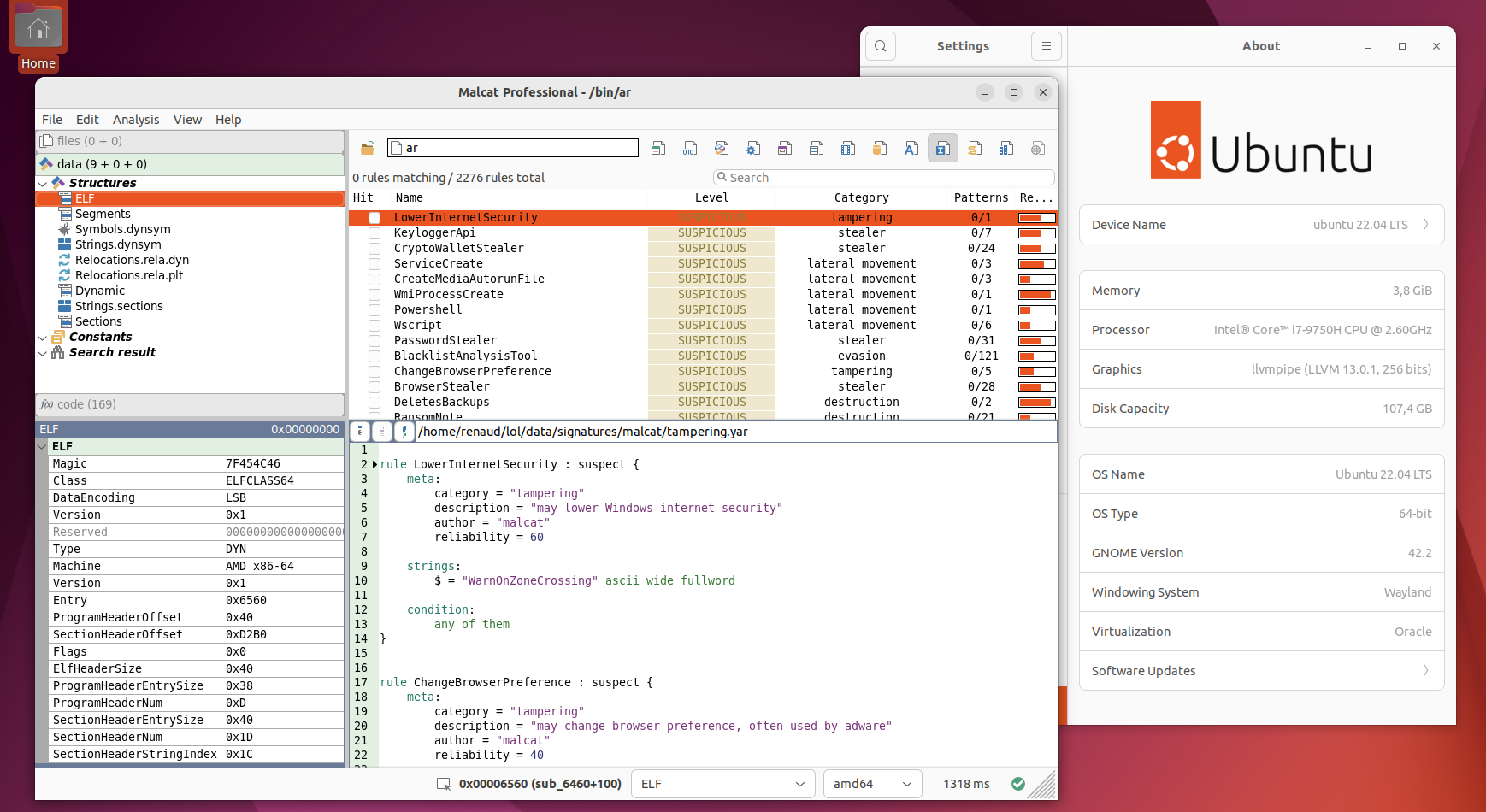
New release: 0.8.4
New version 0.8.4 is out! Enjoy support for ubuntu 22.04 / python 3.10! We've also improved the analysis of LNK and NSIS files, added more than 400000 API hashes in our constant database and malcat can now identify and parse Cobalt strike configuration files.
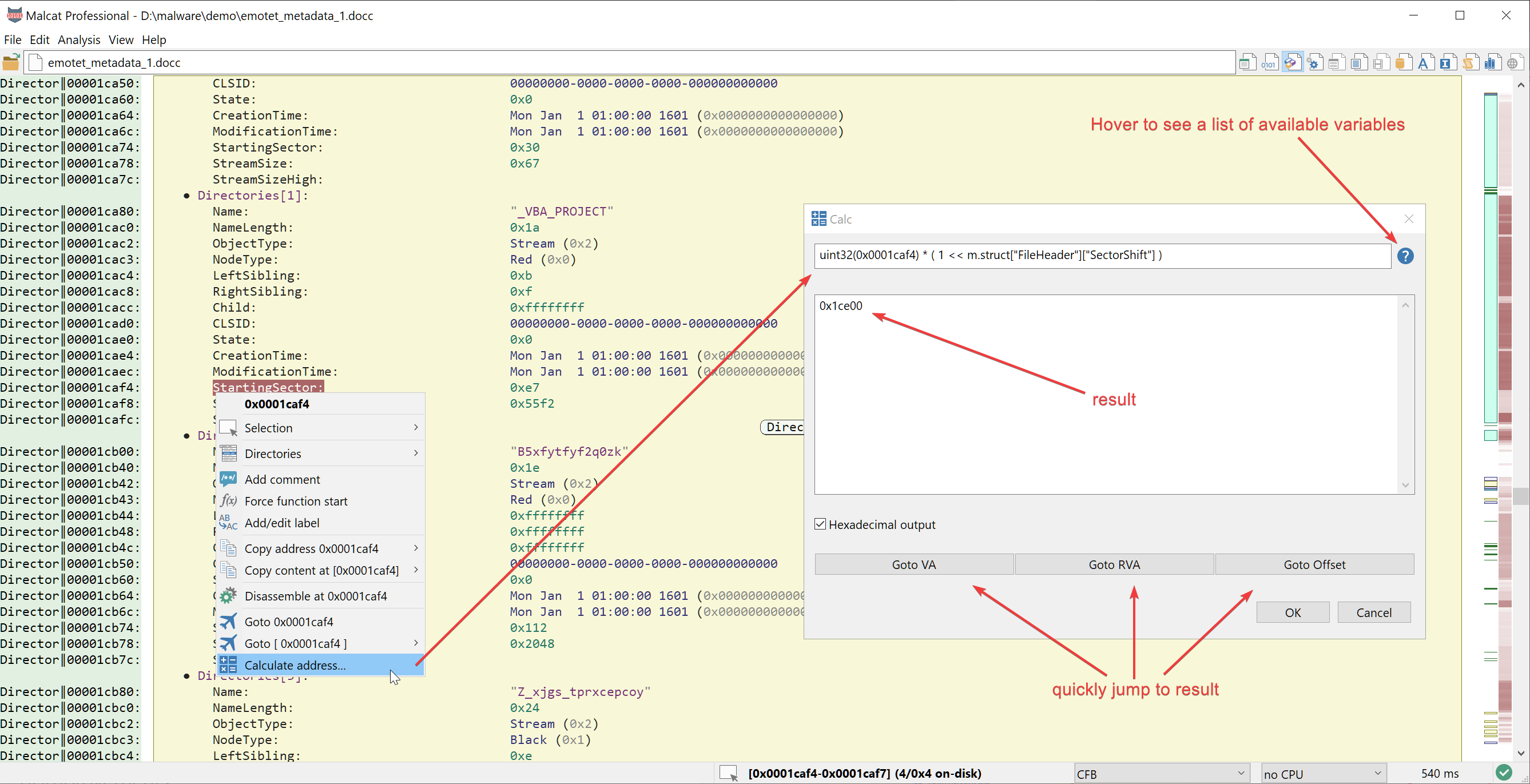
New release: 0.8.2
New version 0.8.2 is out! Enjoy blazing fast stack strings detection for x86/x64, CD/DVD file system browsing, Py2Exe scripts disassembly and lzma streams detection.
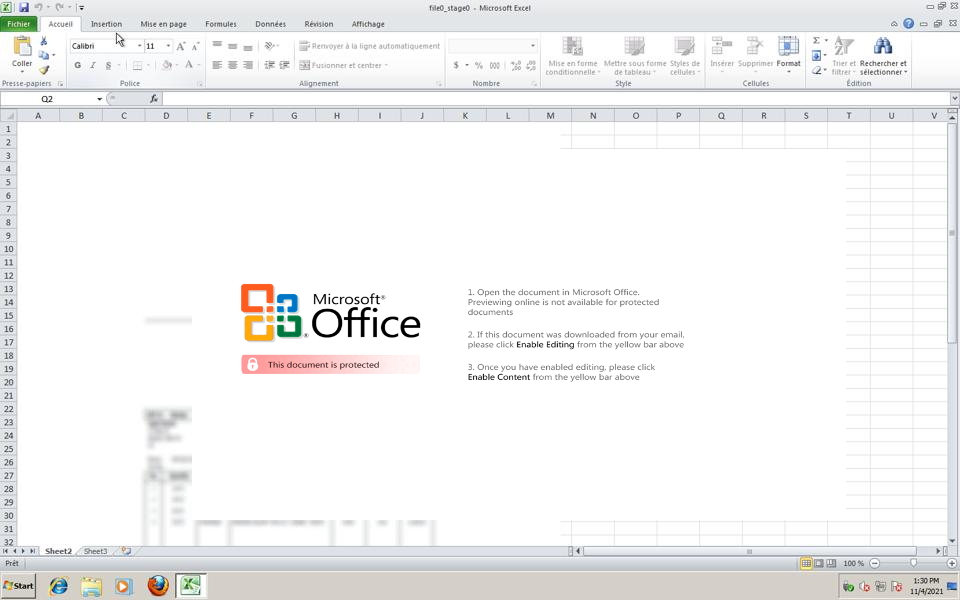
Reversing a NSIS dropper using quick and dirty shellcode emulation
We will statically unpack and emulate a malicious NSIS installer running multiple shellcodes, up to the final Lokibot password stealer and its configuration.
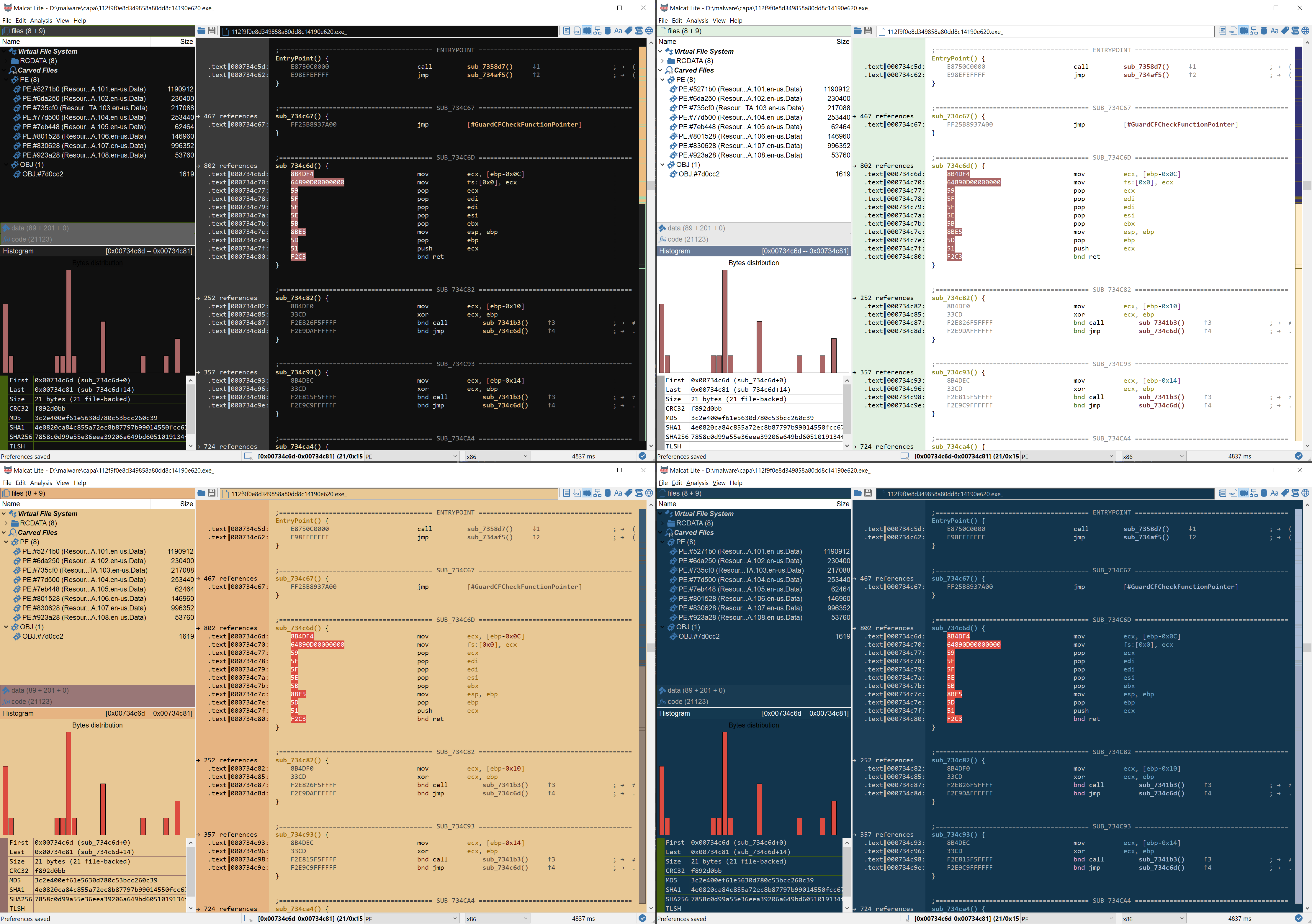
New release: 0.8.0
New version 0.8.0 is out! New RTTI analysis, VTGrep integration, improved python + Golang disassembly, color themes and advanced selection.
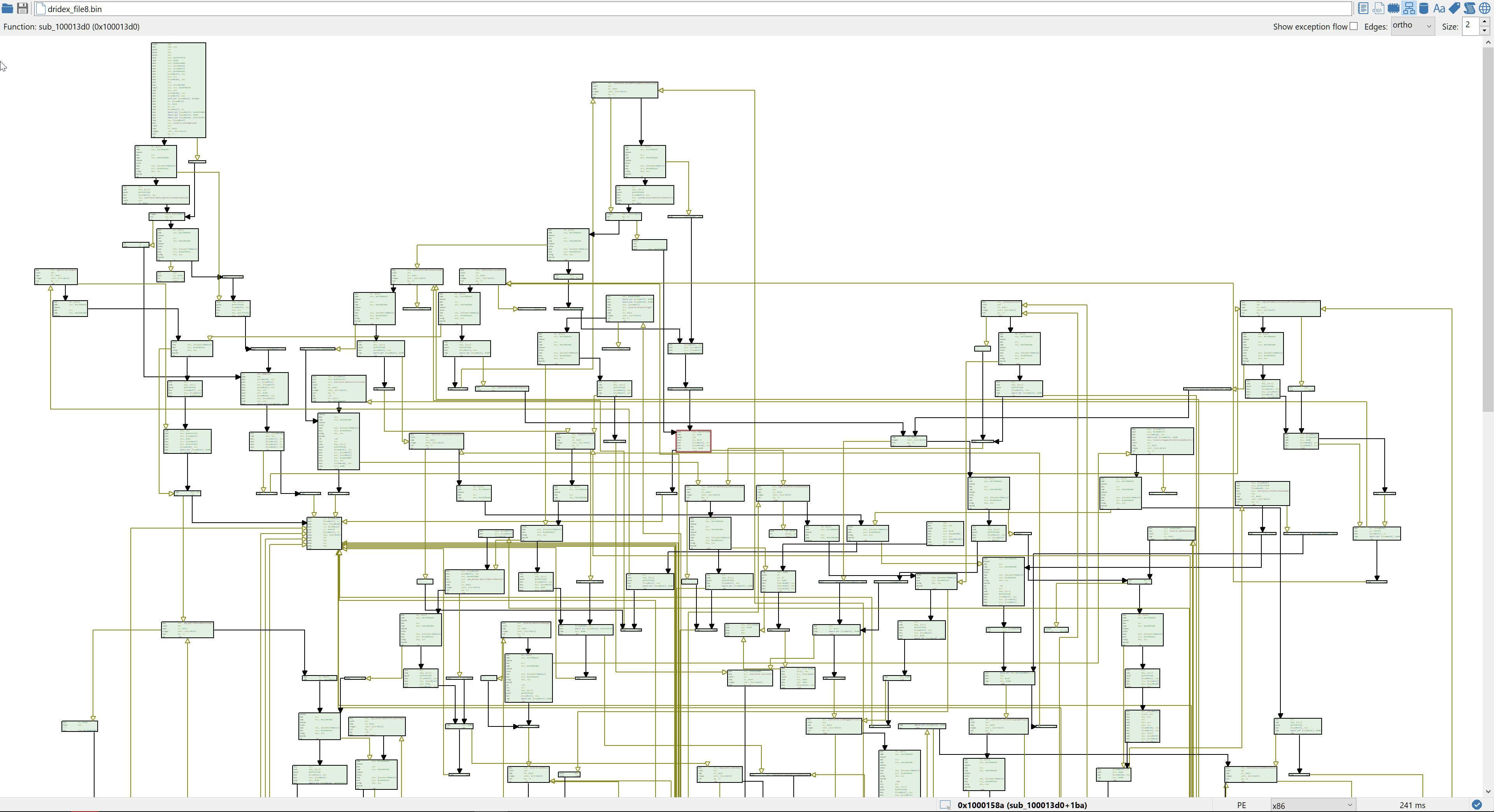
Cutting corners against a Dridex downloader
When one faces obfuscated code, it is sometimes more efficient to focus on the data instead. By using Malcat's different views and analyses (and a bit of guessing as well), we will show how to statically unpack an excel downloader and the following obfuscated native dropper without (much) reverse engineering.
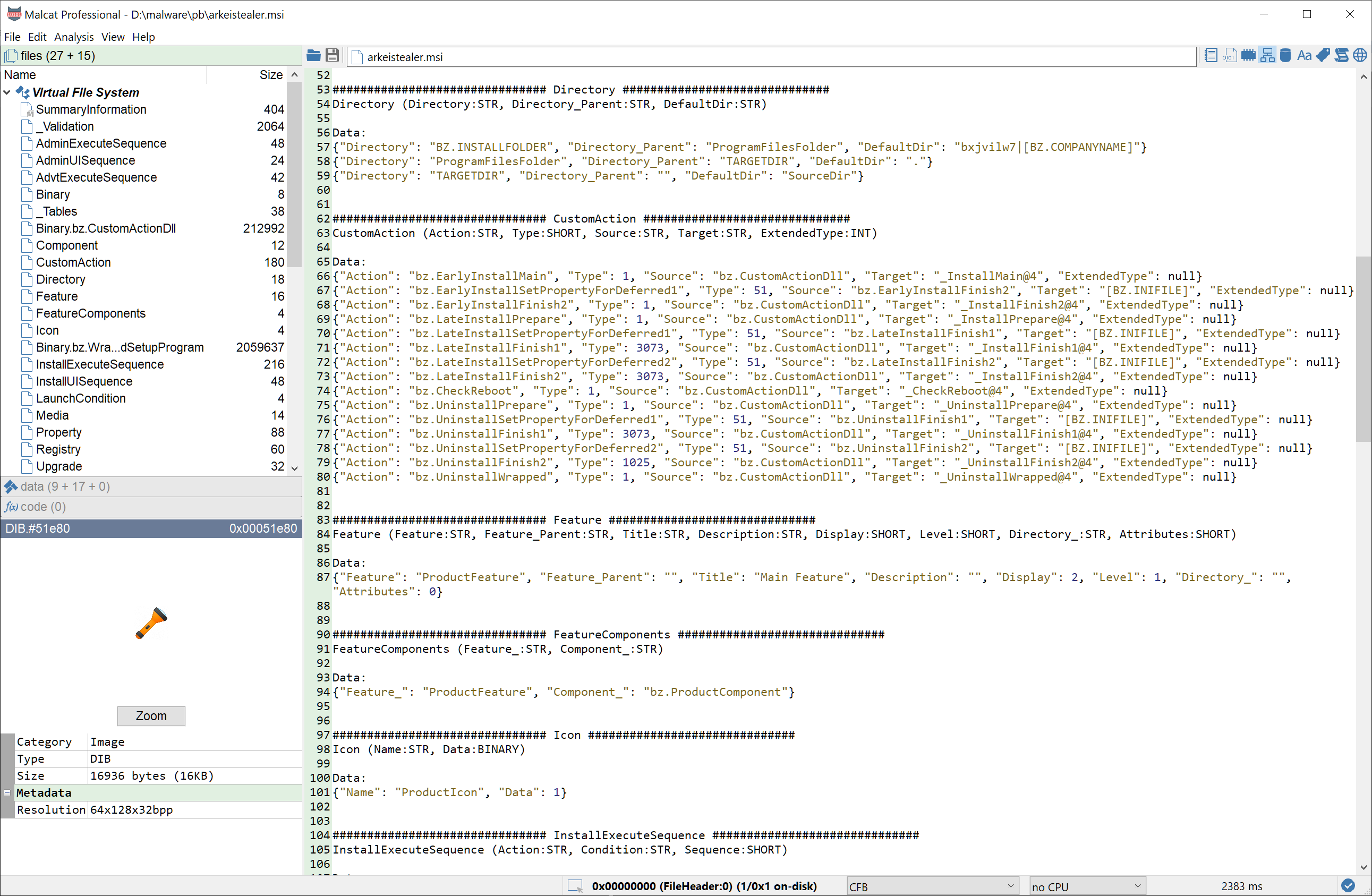
New release: 0.7.88
New version 0.7.88 is out! Added MSI installer decompiler, improved scripting documentation and added Joe Sandbox threat intelligence lookup.
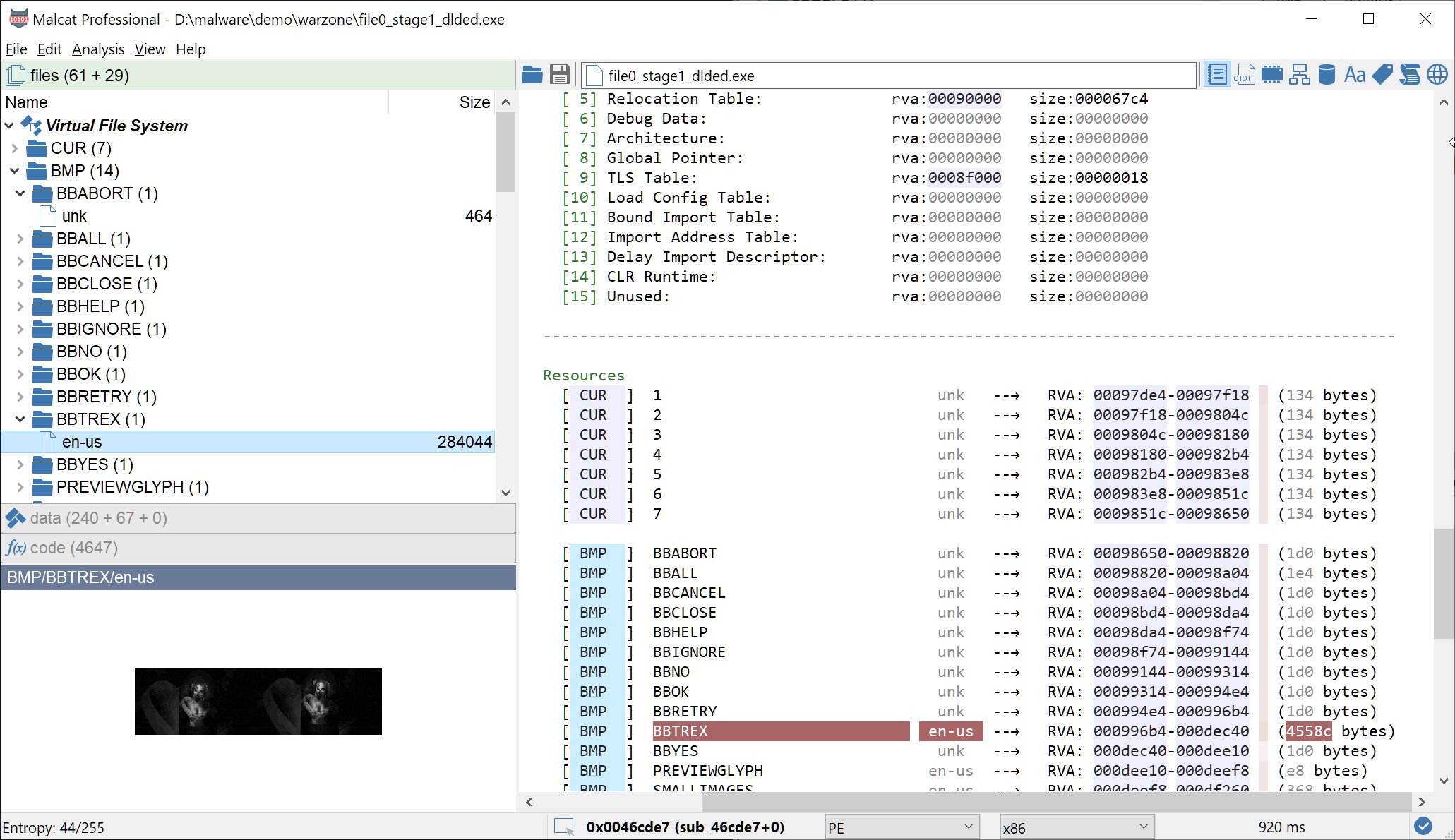
Exploit, steganography and Delphi: unpacking DBatLoader
We will unroll a maldoc spam exploiting CVE-2018-0798 leading to a multi-staged Delphi dropper abusing steganography and cloud services to conceal its payload
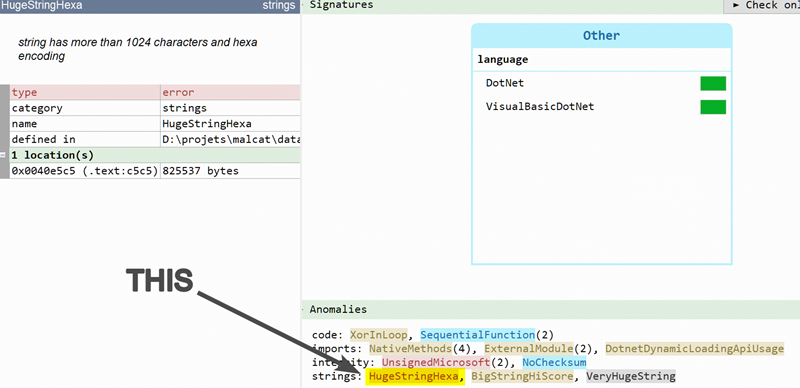
Statically unpacking a simple .NET dropper
Our target is a 2-layers .NET dropper using multiple cipher passes (XOR, AES ECB and AES CBC + PBKDF2) to finally drop a Loki sample. Without even starting a debugger, we will show how to unpack it 100% statically using Malcat's builtin transformations and the python scripting engine.