Today we are happy to announce the release of version 0.9.0! Slowly but steadily Malcat is improving towards a feature-full binary analysis solution. This is the latest "big" release before Malcat's full 1.0 release and contains some major improvements:
- Open multiple projects in parallel and easily switch between them
- Scan binaries for FLIRT signatures (FLIRT version 6+ supported)
- Analyse OneNote (.one) files
- Quick bookmarks for easy navigation
Let us see what it is all about.
Open multiple projects in parallel
Files vs projects
Malcat makes the distinction between files and projects. A project is a root file present on the disk + any additional sub-files extracted from this root file. From within a project, multiple files can be opened, e.g. when double-clicking on carved files or opening resources. This is a depth-first navigation, meaning that only the last opened file is visible to the user at any given time. This could prove a bit problematic, in particular for droppers when say a resource needs to be decrypted using a key found in the program. This would involve starting two instances of Malcat: one opening the embedded resource to decrypt, and one displaying some the disassembled decryption function.
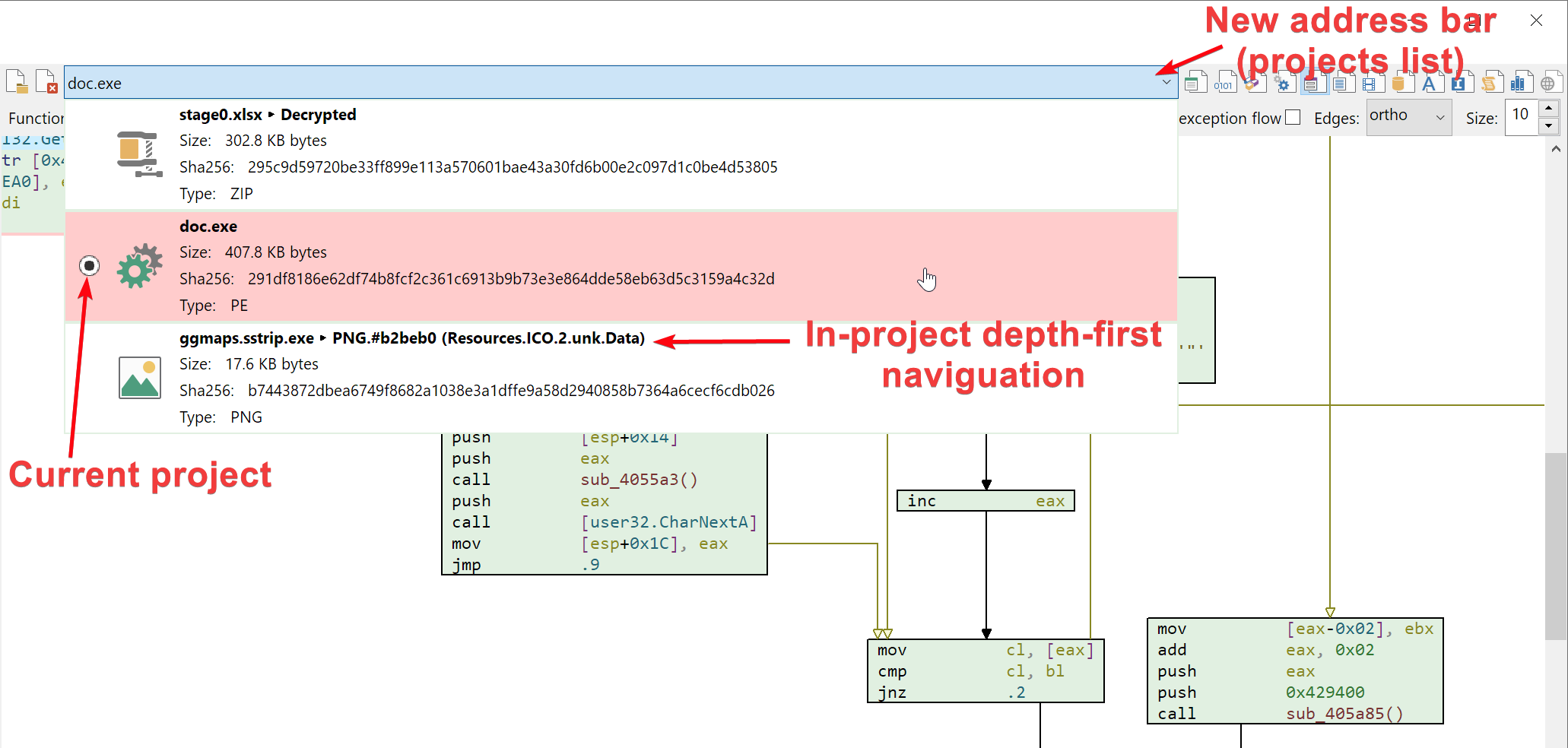
This is now a thing of the past! Malcat is now able to keep multiple projects open in parallel and can switch between them. We did try many different UX approach to enable multi-project navigation. From the standard tabs (which at the end eats to much virtual space) to a treeview display on the left (which was a bit confusing). Finally, the best solution in our opinion was to extend the filename bar that is already present. By clicking the address bar, you can now switch between the different opened projects. You also get some basic information about the file in case you somehow get lost. This cosmetic change made us refactor a non-negligible portion of the GUI code, so don't hesitate to tell us if you spot an error.
How does it work
By default, double-clicking on a carved file or virtual file will still opens the file within the current project. But you can chose to open the file in a new project by choosing Open (new tab) in the context menu.
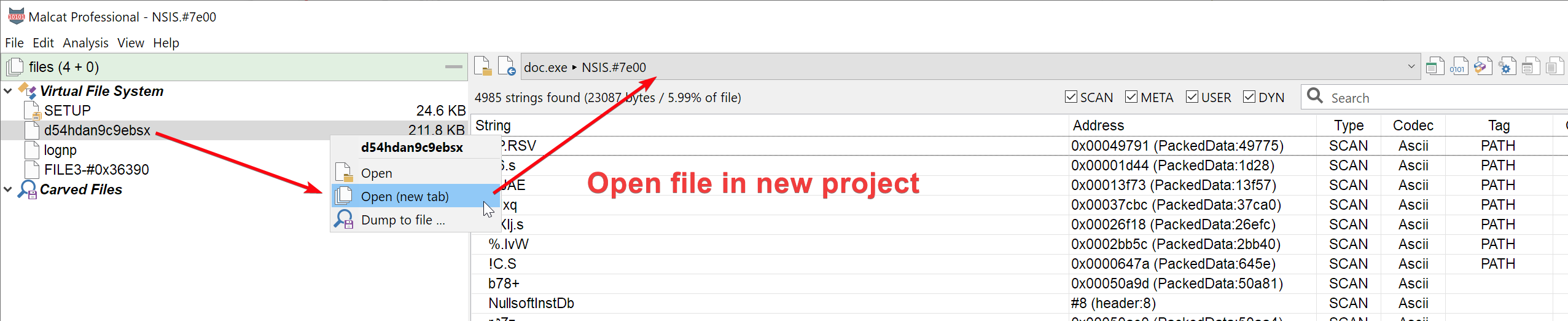
Additionally, if you open a new file in Malcat using Ctrl+O, it creates a new project instead of replacing the existing project. You can revert to the old behavior (replace currently open project) using the Options dialog: uncheck General > Open new files in new tab.
FLIRT signatures support
FLIRT signatures
FLIRT signatures have been developed by the team behind IDA in order to identify library functions statically linked inside a program. This is kind of a reverse-engineering industry standard nowadays and is very helpful when reverse engineering big applications lacking any kind of symbols.
Currently, Malcat embeds (MIT-licensed) FLIRT signatures for:
- Msvc runtime (x86 and x64)
- Delphi 6 and 7 runtime (x86)
- Libcurl (x86 and x64)
Note that adding your own FLIRT signatures is very easy: put any .sig file in <malcat install dir>\data\flirt or even better in <your user data dir>\flirt, hit Ctrl+R and you're good to go.
You will notice that in Malcat there is (currently) no option to manually apply a FLIRT signature to a file. By default, FLIRT signatures are automatically applied to every analyzed program. Why? First, because we want Malcat to be beginner-friendly, and beginners are often overwhelmed when asked to chose the right FLIRT signature to analyse their file.
Second, Malcat has been designed to be fast. Opening a file should be almost immediate. Manually choosing a signature file using a dialog goes somewhat against this philosophy. If you don't want your FLIRT signature to be applied to every new file, you can specify a precondition for your FLIRT signature instead.
FLIRT preconditions
FLIRT scanning comes at a (small) cost: for the big MSVC FLIRT signatures for instance (that is two .sig files of about 5 MB zipped), it takes 500ms to scan a moderate-sized PE program. If Malcat would blindly apply these FLIRT signatures every time to all newly analyzed files, we fear that users would run into two issues:
- Analysis times would become somewhat noticeable, in particular if you add a lot of FLIRT signatures to Malcat
- You will see false positives, i.e. wrongly-identified methods, since FLIRT signatures are far from fool-proof
In order to tackle these issues, every FLIRT signature myflirt.sig may be accompanied by a precondition file with the .precond extension, e.g. myflirt.precond. This file should contain a single python lambda expression that will be evaluated by Malcat at runtime. If this expression returns true, then the FLIRT signature will be applied to the file, otherwise the signature files will be ignored.
The python precondition has access to some of the Malcat's python bindings. Since FLIRT scanning is performed pretty early in the analysis pipeline, the python code will have only access to:
- The raw file, i.e. the
malcat.fileobject - The file structures, i.e. the
malcat.structobject - The file mapping, i.e. the
malcat.mapobject - The CFG, ie the
malcat.cfgobject
These bindings are described and illustrated inside Malcat's help files (hint: hit Ctrl+H and look for Scripting). For instance, here is the precondition for the MSVC flirt file:
1 | |
Any PE file having a Rich header will apply the MSVC flirt signature. But you can have more complicated preconditions. Here is the one for libcurl_x86.sig for instance:
1 2 3 4 5 6 | |
Using python as a language for preconditions should give you, the users, enough control over your FLIRT signatures.
Microsoft OneNote analyzer
Users and security solutions are getting every day better and better at detecting the usual wave of malicious documents in their inbox. Some threat actors, in an attempt to evase detection, are now moving to Microsoft OneNote for their malicious downloaders. While Microsoft OneNote lacks any kind of macro, it can embed arbitrary files. And by using some clever overlay positioning, threat actors may trick users into double-clicking these embedded files, thus running the payload.
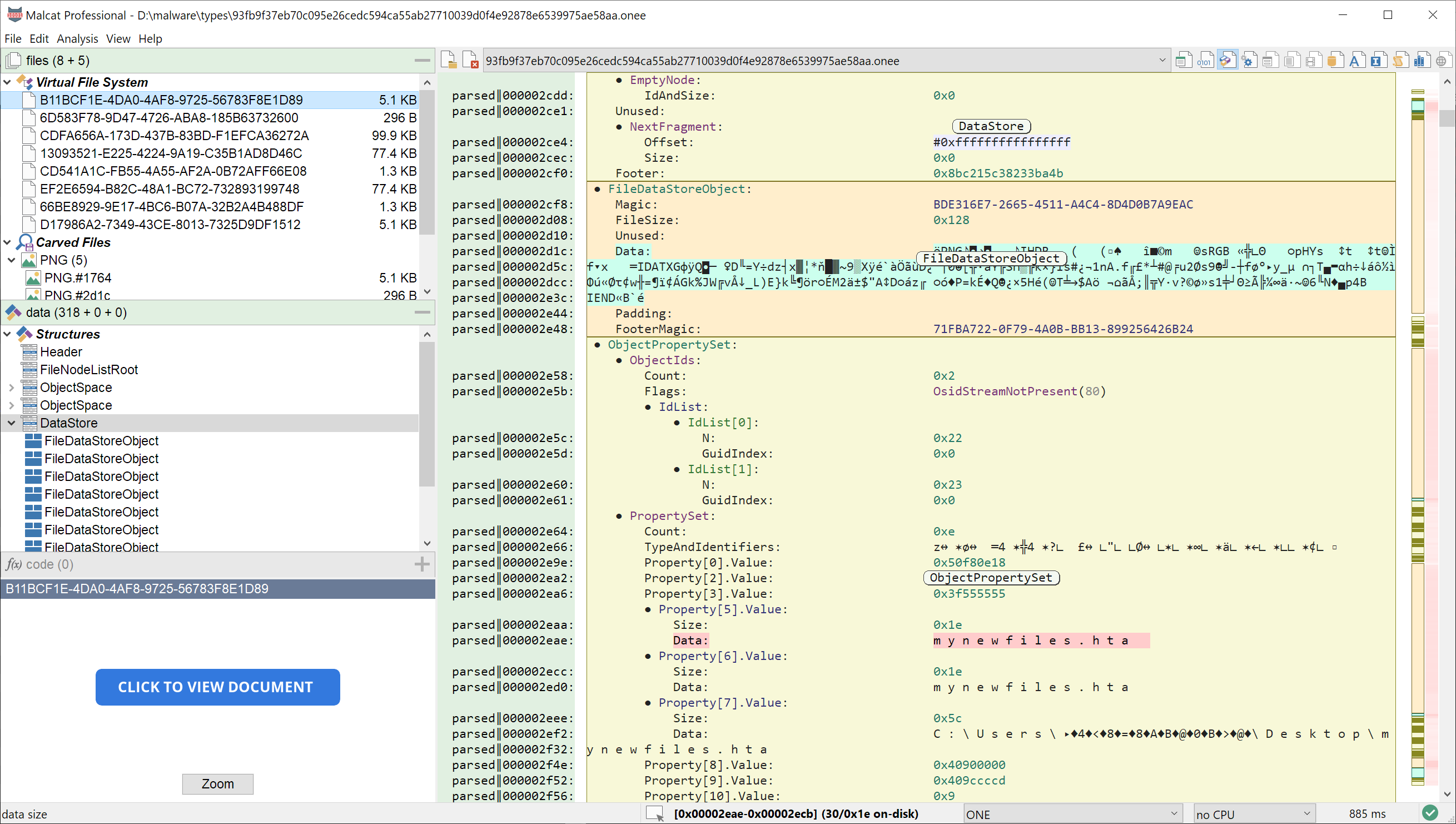
By chance, the OneNote file format is well documented and it was relatively easy to add a file parser for this file type to Malcat. You can now inspect most of the structures of any .one document and even naviguate over the embedded files. OneNote becomes officially the 46th file format supported by malcat.
User bookmarks
User bookmarks are a feature that many of you wanted, and will allow users to quickly jump back and forth within the analyzed binary. The idea is simple: when inside the hexadecimal, structure or disassembly view (basically anything with an address row), hit Ctrl+Alt+0 .. Ctrl+Alt+9 to set the bookmark number 1 .. 9 at:
- the selected byte address, if a single byte is selected in the view
- the first address displayed in the view otherwise
When a bookmark is set at a given address, its number will be displayed in the address row of the view, as you can see in the picture below. If you don't like using your keyboard, there is also a new Toggle bookmark sub-menu in the context menu, that will set / unset a bookmark at the address when you just right-clicked.
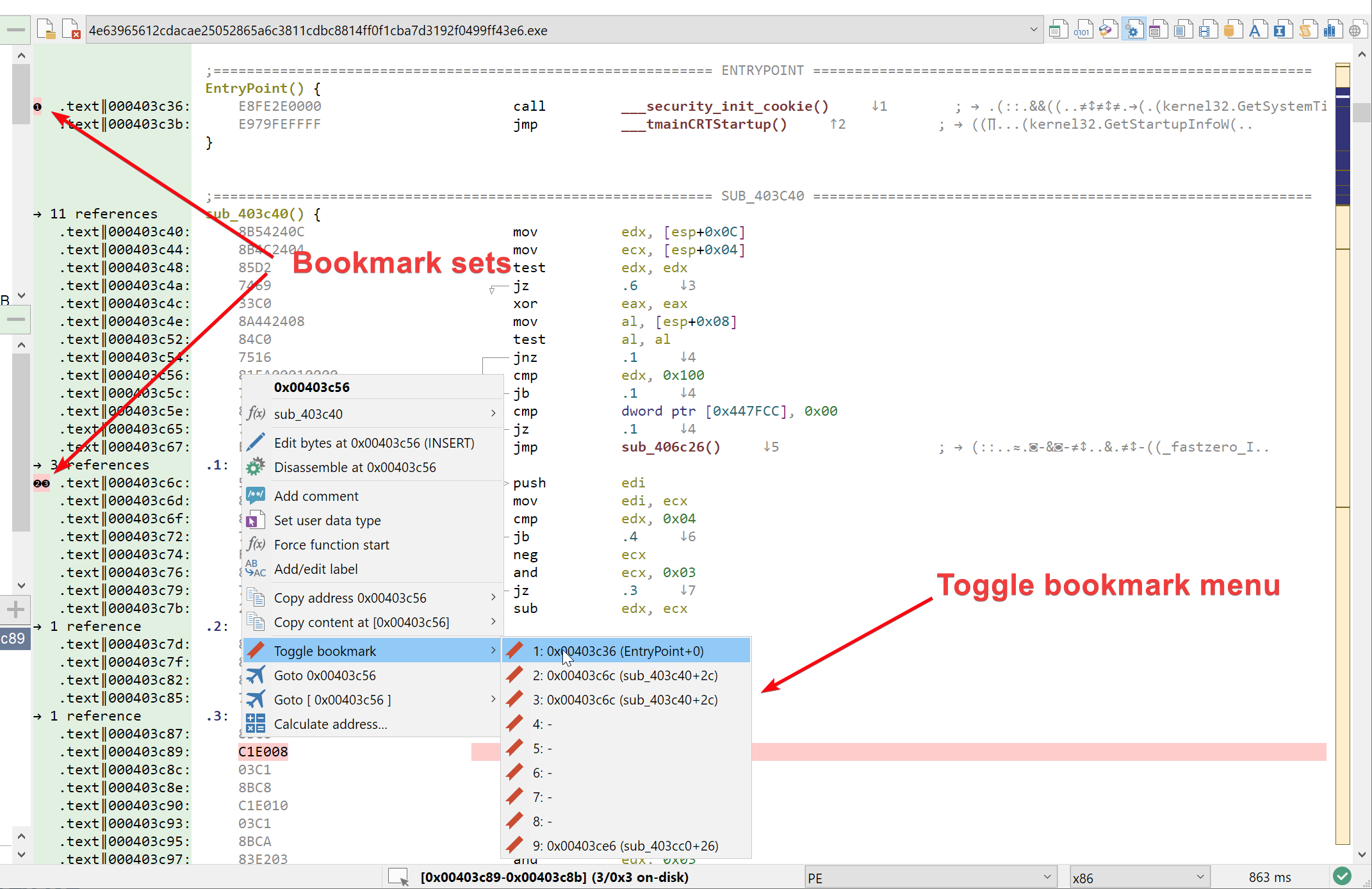
To quickly jump to a specific book, you can either hit Alt+0 .. Alt+9 on your keyboard or use the menu View > Goto bookmark. Note that jumping to a user bookmark is registered into the Malcat's "last-jump" list, meaning you can always go back to you where using Backspace, like for any other jump.
FileScanIO integration
FileScanIO has been added to the list of threat intelligence providers. Results from the platform are now included when you query threat intelligence results.
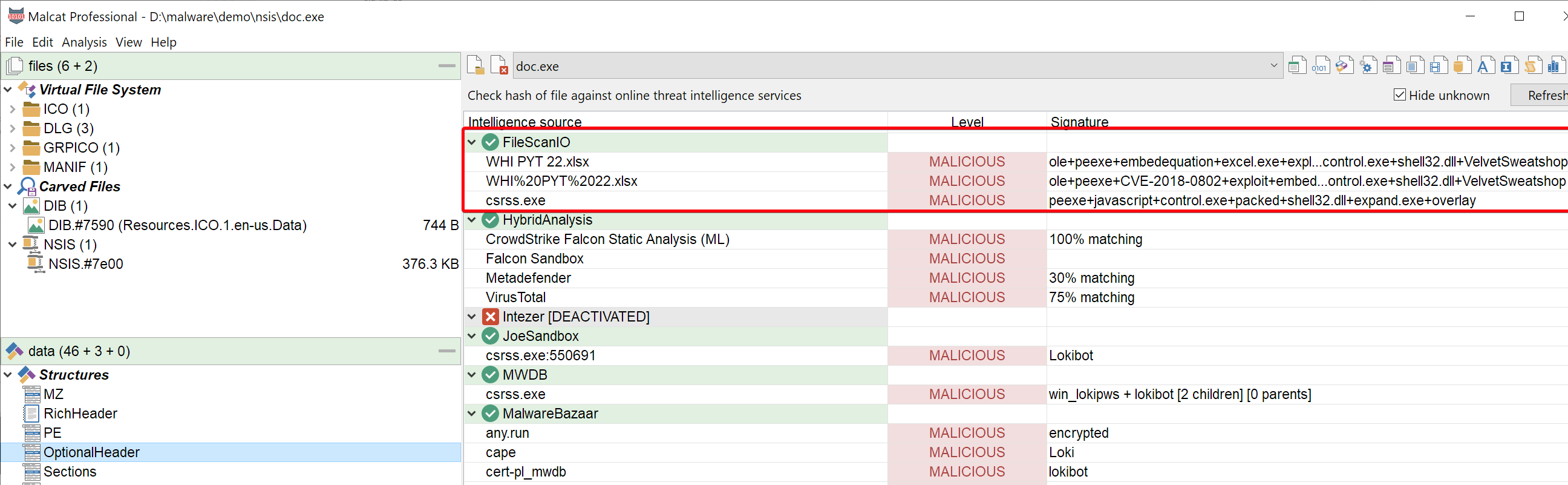
Please note that FileScanIO requires an API key to work, but you can query one for free on their website.