Today we are happy to announce the release of version 0.9.2. This release focuses on the global workflow and includes many quality-of-life improvements. And thanks to your feedback, a couple of rather cool features have been added:
- New data transform workflow, now including chained transforms!
- Better source code viewer
- CHM file format support (with in-app unpacking)
- .NET static arrays parsing
- You can now shift, insert and delete bytes in file
- Several user interface QoL improvements
- The usual: bug fixing, documentation and updates for the Yara and anomalies rules sets
Slowly but steadily Malcat is improving towards a feature-full binary analysis solution. Stay tuned for the next update!
New data-transform workflow
Malcat is first and foremost a static analysis tool aimed at inspecting malicious programs. Since malicious binaries usually come obfuscated, it is often needed to decrypt, decompress and manipulate data in the program in order to uncover the most interesting parts of the malware. Malcat embeds more than 60 algorithms than you can use inside the transform dialog in order to deobfuscate arbitrary data buffers in the analyzed data. And since these algorithms (aka transforms) are written in Python, it is very easy to write your own transform operators!
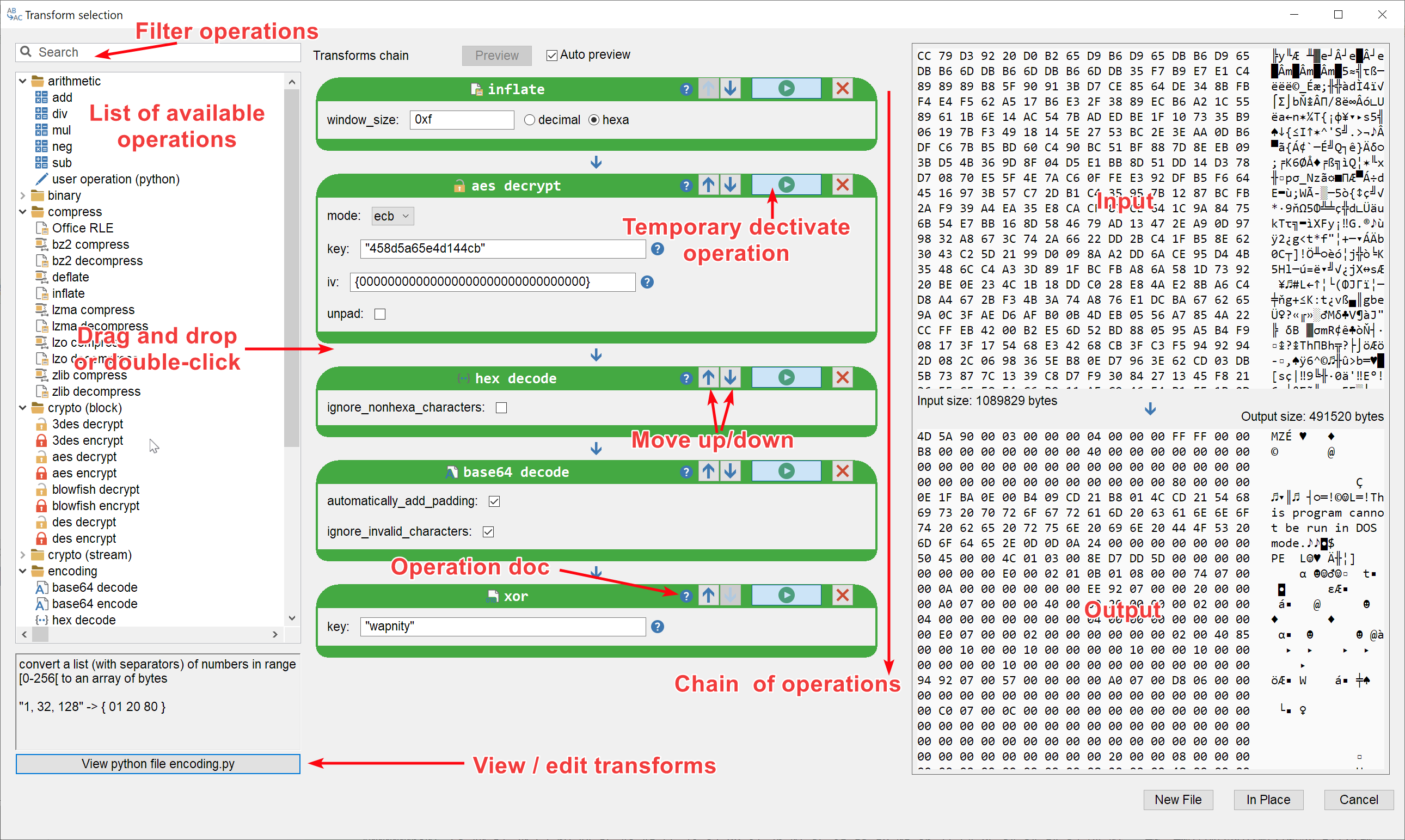
Until now, you could apply transforms one by one in Malcat using a somewhat crude dialog. Since some of you wished for a better user experience similar to the excellent CyberChef website, we did a complete overhaul of the transform dialog. Under the hood, the following points have been improved:
- You can now apply a chain of transforms in one go.
- The user interactions have been improved: drag-and-drop support, reordering and enabling/disabling of operations.
- You can now view/edit the python code of transform operators using the in-app python editor.
- The transform chain is now applied in a background thread for better UI responsiveness.
- The hexadecimal viewer used for preview is bigger
- The dialog is now modless: you can let it open and still use Malcat's interface. It is useful when copy/pasting keys from the different views.
- You can filter operators using a search box
We hope that you'll enjoy this new workflow. If you want more details about data transforms in Malcat, just have a look at the new chapter in the documentation.
Improved source code viewer
Malcat includes for some time several decompilers for x86/x64, AutoIT, Office macros, Excel macros and MSI databases. Decompiled source can be viewed within within Malcat's source code viewer (accessed via the F4 shortcut). This view got a slight upgrade in the 0.9.2 release that will be described below.
Changes to the interface
The script source viewer (i.e. the view shown for AutoIT, Office macros, Excel macros and MSI databases) got a revamp. The biggest change is that the view is now modifiable. You can also now change the syntax highlighting and save the decompiled code to a file. Folding of class/functions has also been added for the languages supporting it.
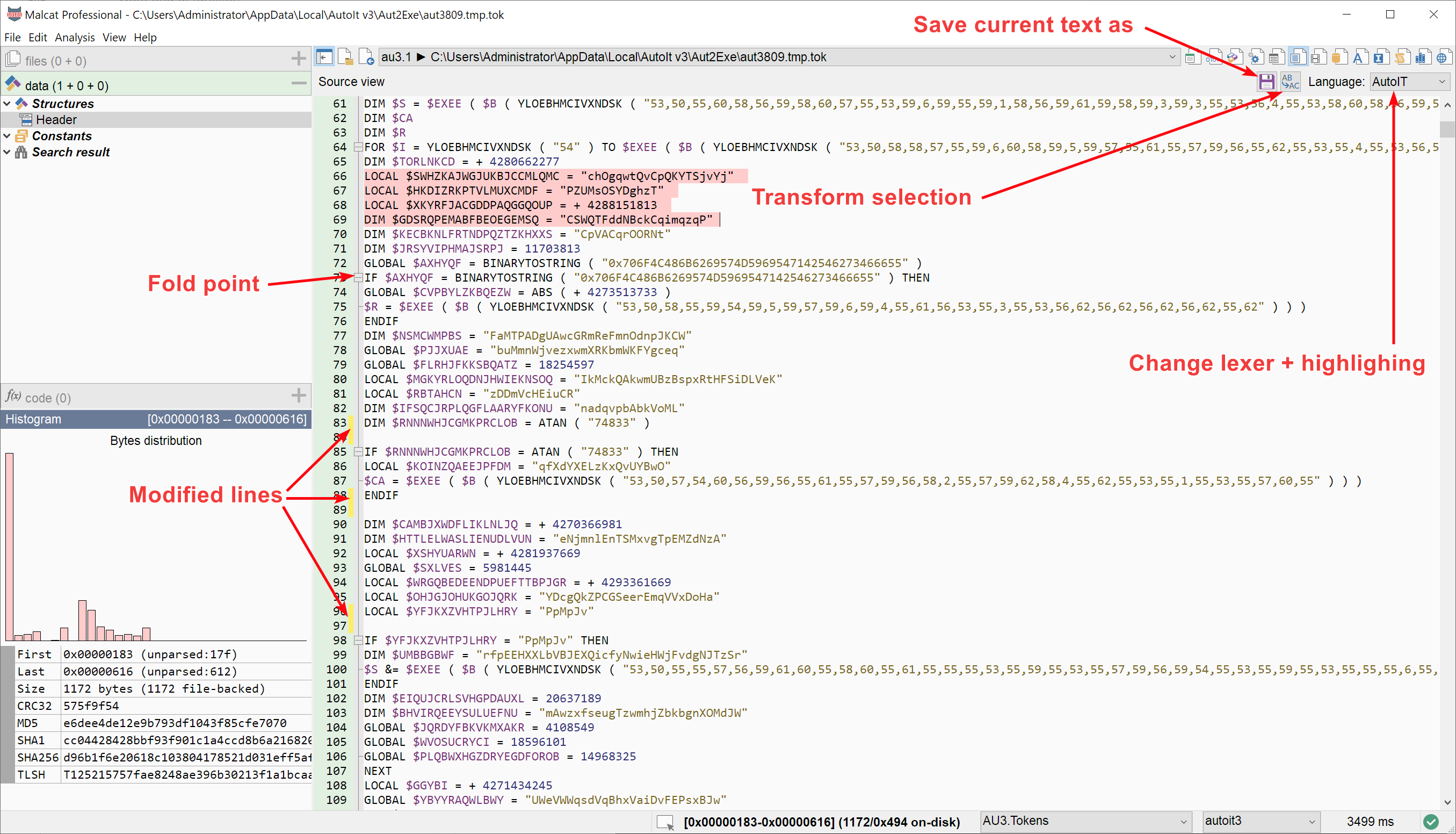
And last but not least, you can now use the new data transform dialog on decompiled source code! This give you access to Malcat's 60+ transform operators, which should come handy when facing obfuscated scripts.
Note: since the source code view contains text and not bytes, an additional UTF-8 conversion step is performed in the background: make sure that your transform chain understands and outputs UTF-8 encoded text.
Pure text files
Malcat is first and foremost an hexadecimal editor targeting binary files. Nonetheless, malware analysts need to have a look at the occasional script file in order to go to the next stage. While our goal is not to replace a full-fledged text editor, we have added the possibility in Malcat to open pure text files (for now it means files containing only utf-8 or utf16-le text) inside the source code view.
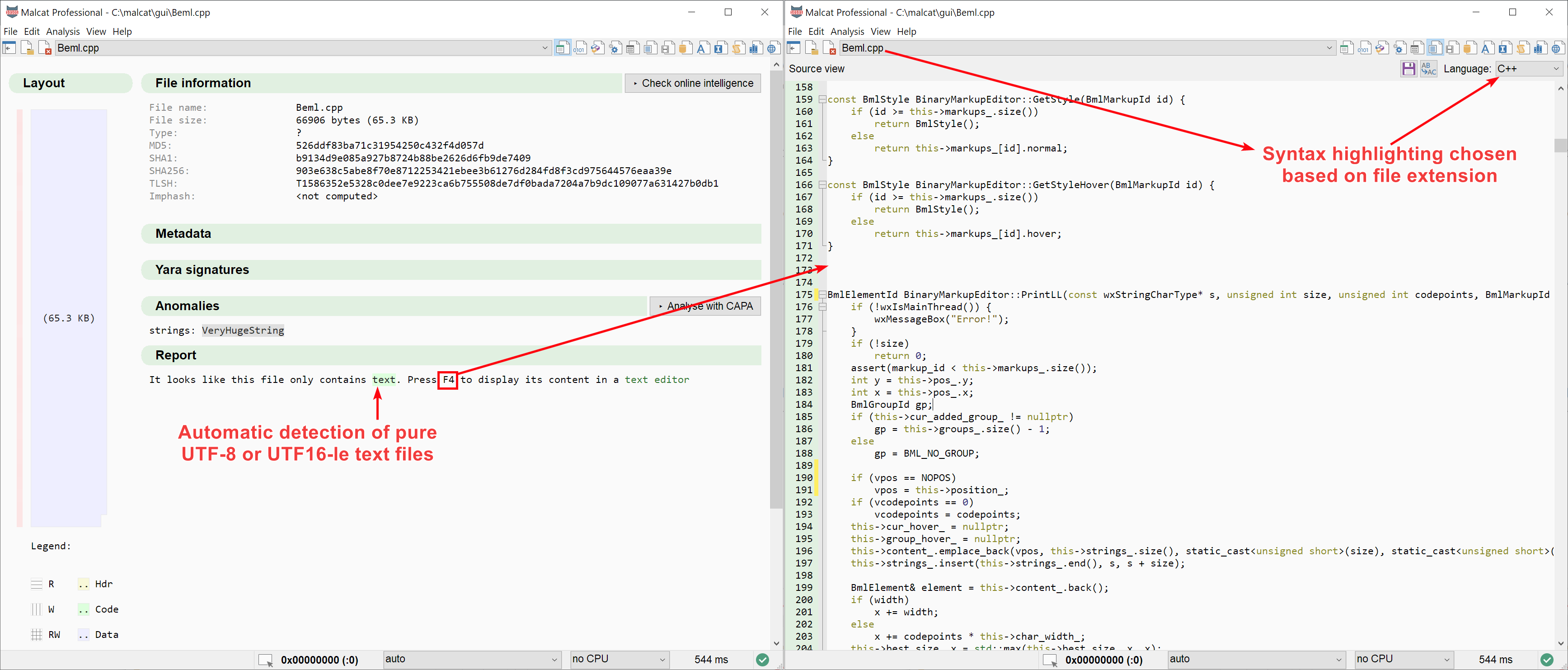
The summary view will now tell you when the file you are analysing only contains text. If you open such files in the source code viewer (accessed via the F4 shortcut), you will be able to view and edit them using a scintilla-based text editor. The best-suited code highlighting will be chosen based on the file extension. You will also be able to deobfuscate the text using Malcat's 60+ transform operators. We have also added a few specific transforms for pure text files, like a JSON beautifier or an HTML/XML beautifier. You can find them under the text category.
Again, don't expect a full-fledged text editor (although the scintilla text control by itself is pretty capable), it's merely there to analyse small scripts.
File parser improvements
CHM file format support
In release 0.9.1 we have added LZX support in CAB file. Our LZX decryptor allowed us to support another LZX-based file format in this release: the CHM file format. CHM files, or Compiled HtMl files, are Windows help files which were developed as a successor of the old .hlp help files. They consist of a collection of HTML pages, an index and other navigation tools compressed and deployed in a binary format. And who says HTML says Javascript and links, two attack vectors often used by malicious actors. Qakbot made heavy use of CHM files in a recent campaign for instance.
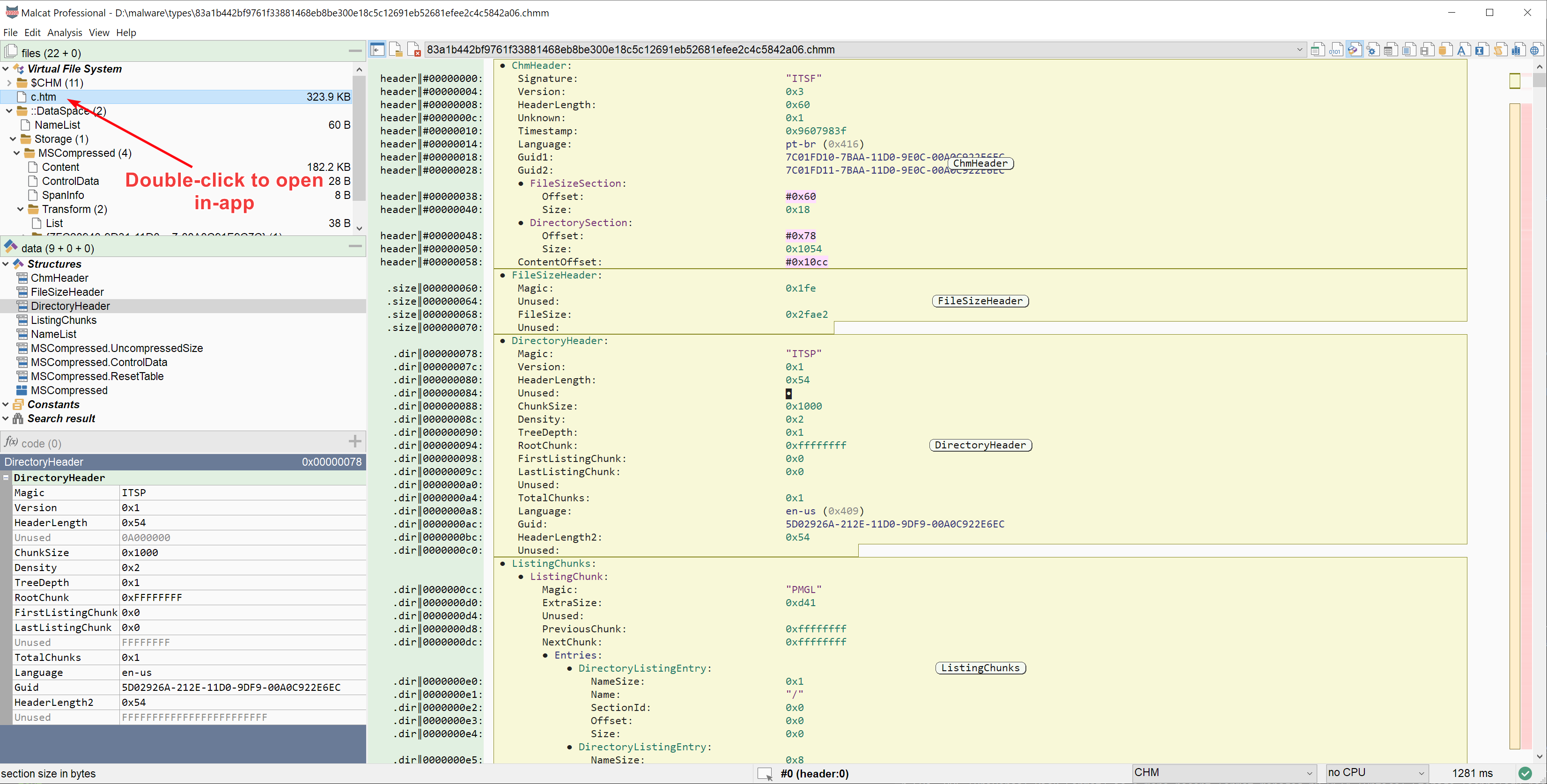
That's why we have added a CHM file parser able to dissect this kind of archive. The parser also allows unpacking of file in-app: just double-click on files in the Virtual File System tab to open them inside Malcat. Combined with our improved source code viewer, this makes investigating malicious CHM pretty easy.
.NET parser improvement
The .NET parser also saw some improvements. First, we've made it a bit more robust when facing obfuscated and encrypted methods. Indeed, a technique used by some obfuscators consists of encrypting part of the .text section, i.e method headers, footers and bodies, and decrypting them at run-time. Malcat should now better handle such hard cases, in particular better handle encrypted method headers.
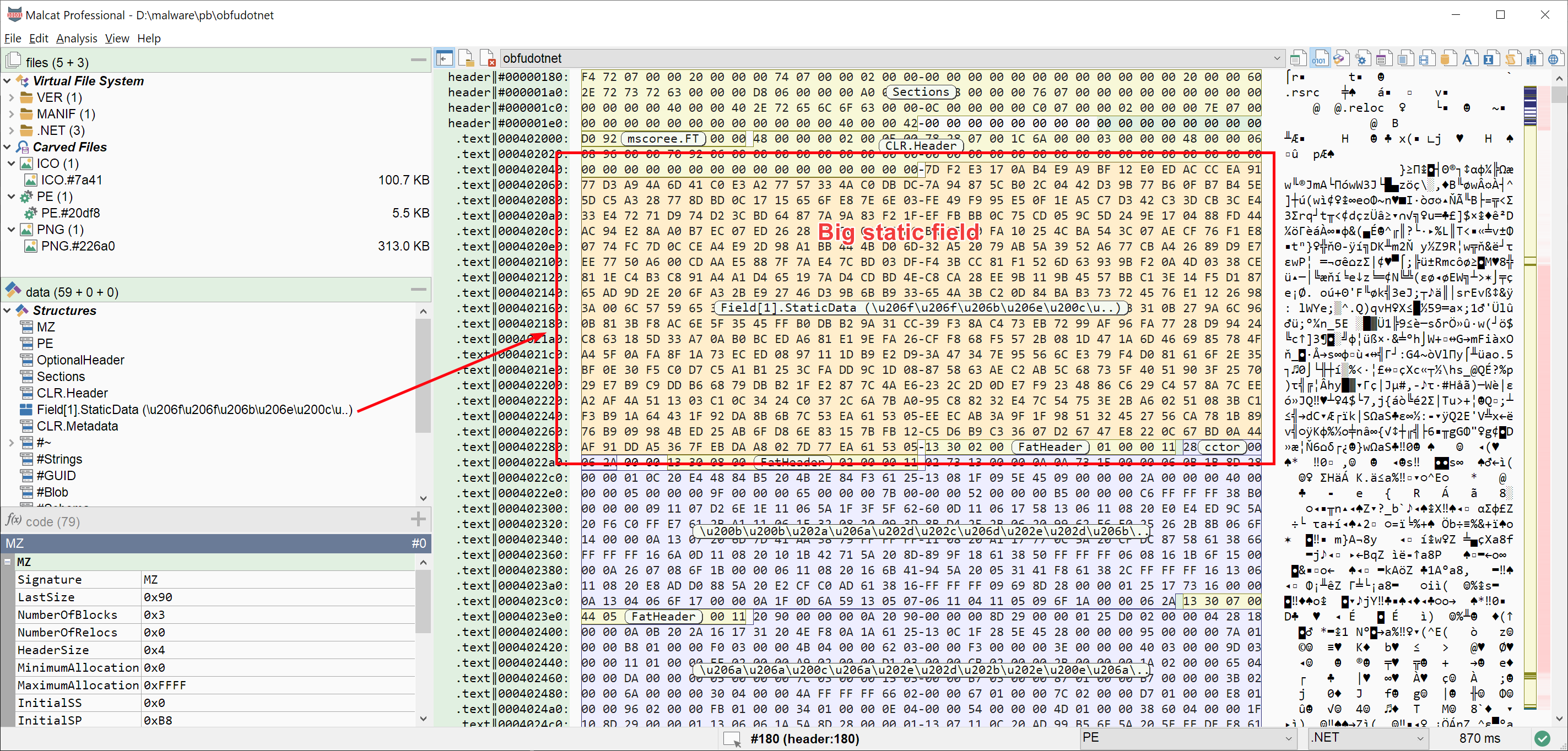
Malcat's .NET parser is also now able to identify and highlight the initialisation data of static fields. Indeed, some packers make heavy use of large static arrays in order to store their payload and/or encryption keys. Malcat should now correctly locate them. An anomaly has also been added to detect large .NET static arrays.
Note that identifying these arrays is not straightforward: while getting their RVA is easy (just parse the FieldRVA table), getting their size is another story. The .NET parser needs to:
- parse the
FieldRVAmetadata table - locate the corresponding field in the
Fieldmetadata table - deserialsize the field signature in order to get its class type
- get the class packed size by parsing the
ClassLayoutTablemetdata table
If you spot any error or missed array, don't hesitate to contact us on discord!
File editing
As a hexadecimal editor, Malcat did support file editing from the beginning: just double-click on a byte, hit Insert or hit Ctrl+V to modify the file in-place. But all these operations are overwriting: the file size never changes. The only way to grow or shrink the current file was to open an expanded/truncated copy of it using the Clone dialog.
Well, it was before. It is now possible to insert and remove bytes at the location of your choice in the current file! Note that since the file size will change and bytes will shift, a lot of the analysis needs to be redone. That's why by default, insert and remove operations will be followed by a full reanalysis of the file. You can change this behavior in the preferences though.
Insert bytes
If you want to make space for a shellcode, hook some function or just add content to an existing file, the ability to insert bytes in a file at a given location comes pretty handy. You can now do it easily by right-clicking a single byte in the hexadecimal, structure or disassembly view and choosing Insert bytes. A dialog will pop-up asking you how many bytes you want to insert.
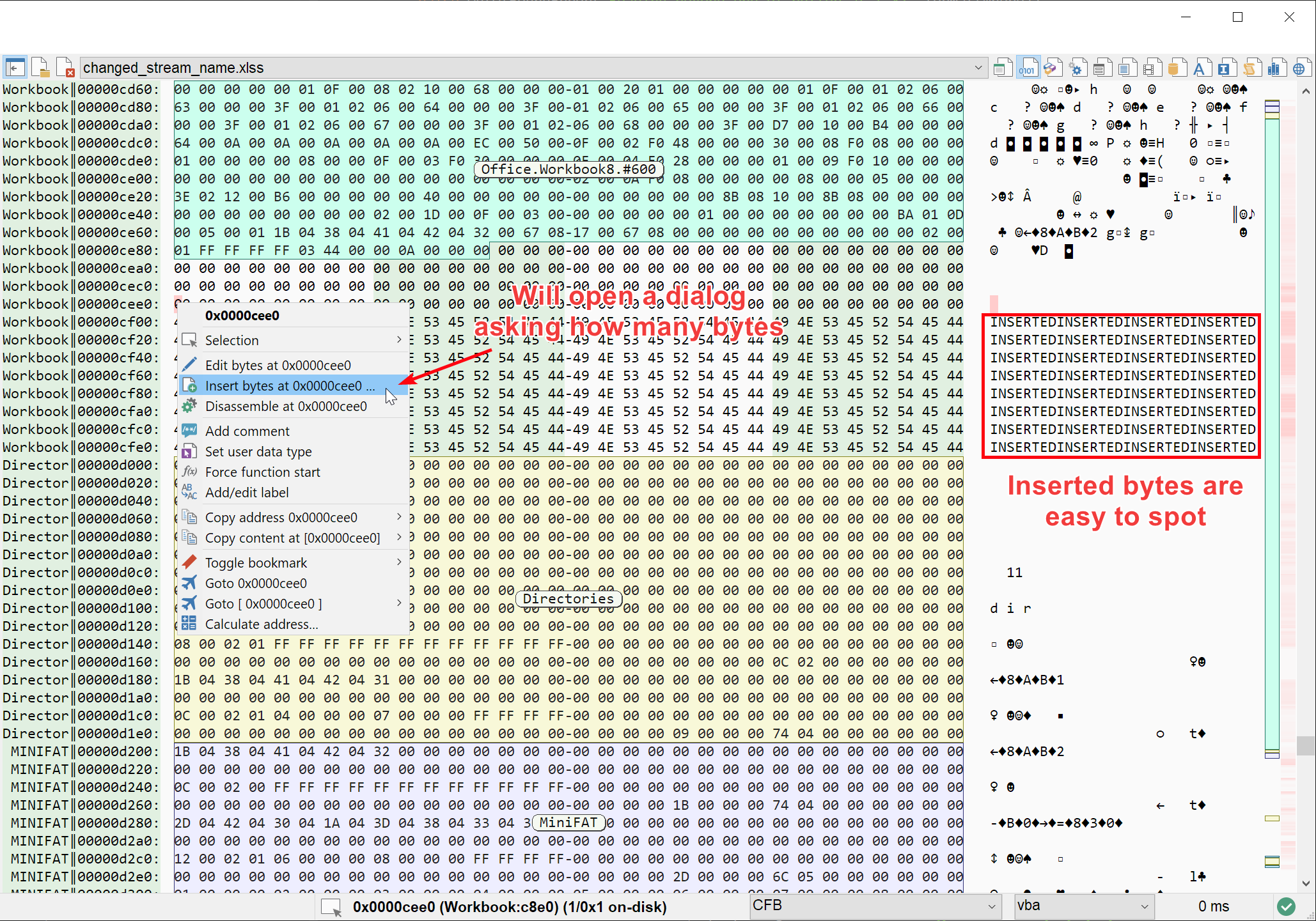
Extra space will be inserted before the selected bytes. The added bytes will be selected by default, and filled with the pattern INSERTED, repeated as needed.
Delete selection
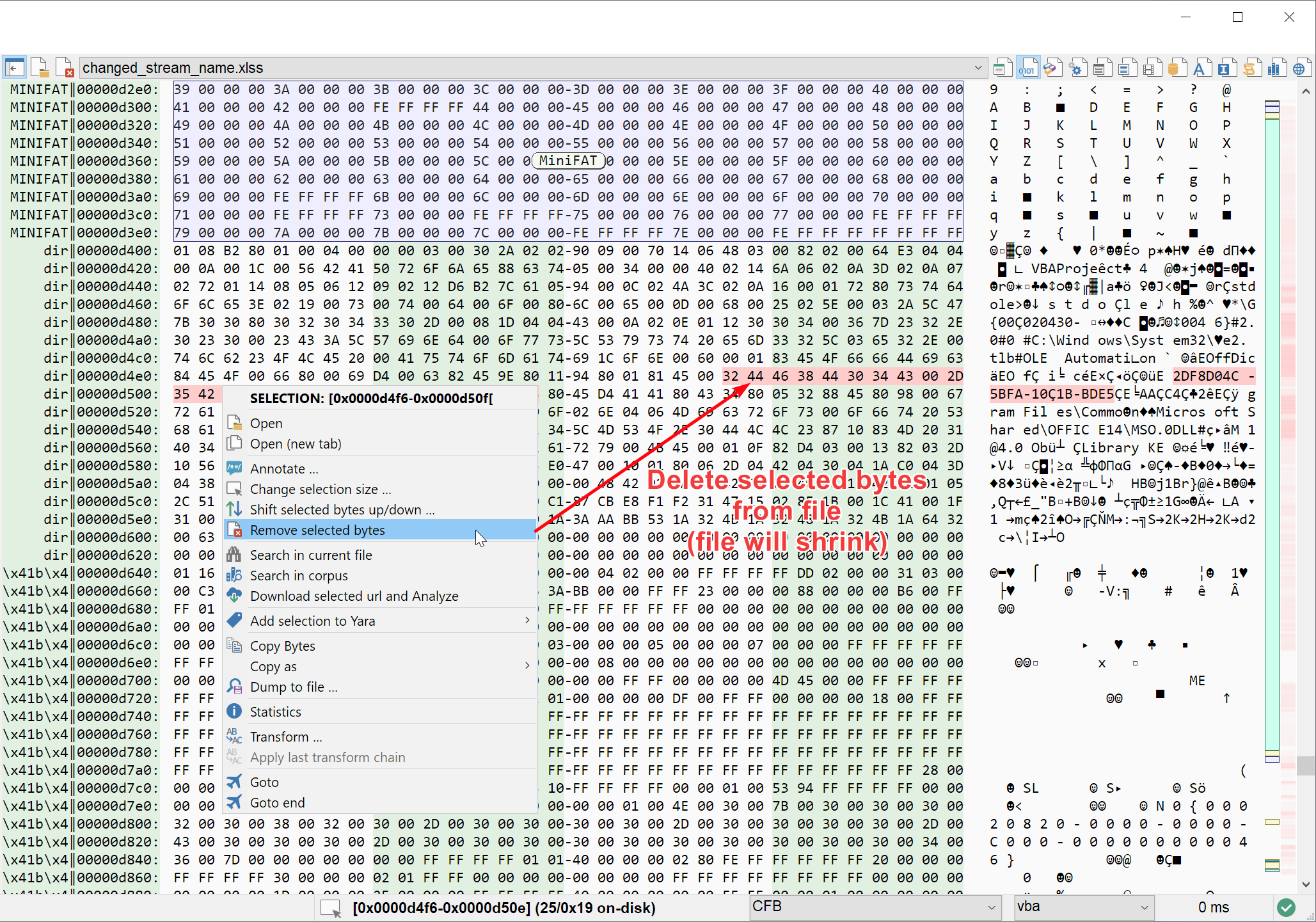
Removing bytes also comes handy from time to time, especially when you are facing bloated malware. You can now delete selected bytes using the Remove selected bytes option in the selection context menu. As for bytes insertion, this will trigger a reanalysis of the current file by default. You can deactivate this behavior, but consider it experimental.
Shift bytes up and down
A few days ago, I needed to manually fix a small shellcode by reordering instructions. While it is possible to do this in Malcat, it was a bit tedious. It did require to find some free space to store temporary content and perform multiple copy/paste operations. While this use case does not come often, I've decided to add a Shift bytes action to the selection context menu:
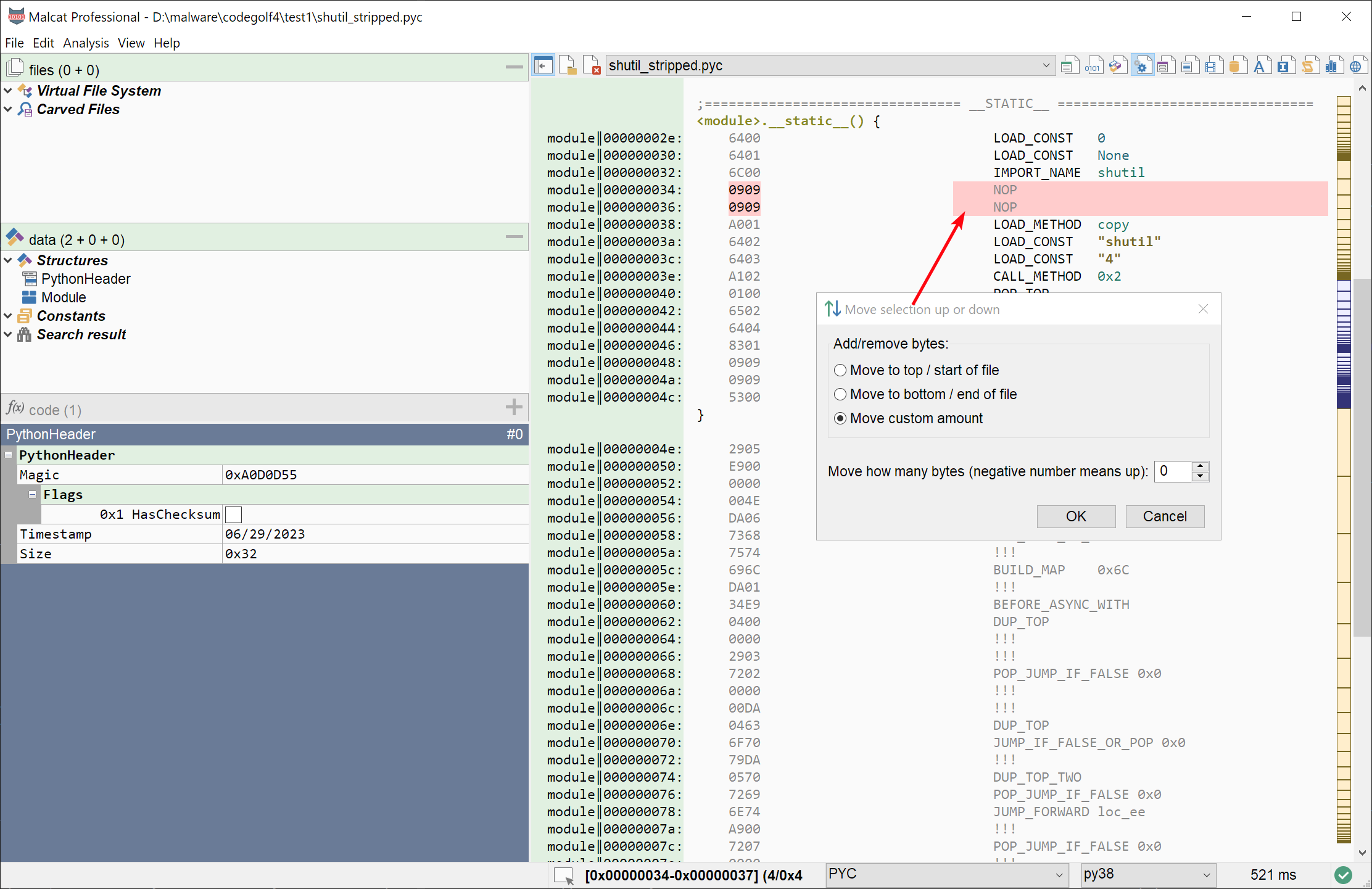
If you chose this option, you will be able to move the selected bytes up or down. The bytes located between the selection and the new destination will be moved in the opposite direction: if you move the selection up for instance, the content will be pushed down. Again, not the most useful operation, but it comes handy from time to time.
Quality of life changes
Goto previous / next recent locations
In order to ease the navigation inside the file, two new buttons have been added to the project toolbar. They will allow you to jump back and forth in the recent locations history. The recent location history is populated automatically by the interface every time you jump to a new location (by clicking on an object or an address for instance). Note that both these buttons have drop-down menus which will allow you to jump directly to a file location deeper in the history.
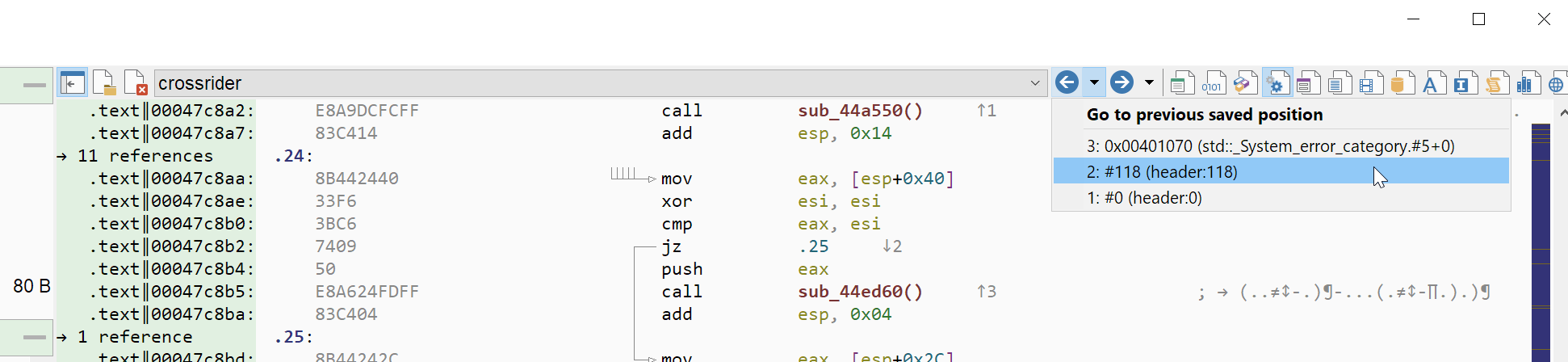
View python code of anomalies
The paid version of Malcat features a powerful anomaly scanner which can point malware analysts to the most interesting locations of a file. If you click on an anomaly in the summary view, you can see the name, category and description of the anomaly, as well as all the locations where it was reported.
In release 0.9.2, a button was added to this quick view. It displays the python source code of the anomaly inside Malcat's in-app python editor. This comes in handy for complex anomalies, where the description is not enough (or if you are just curious).
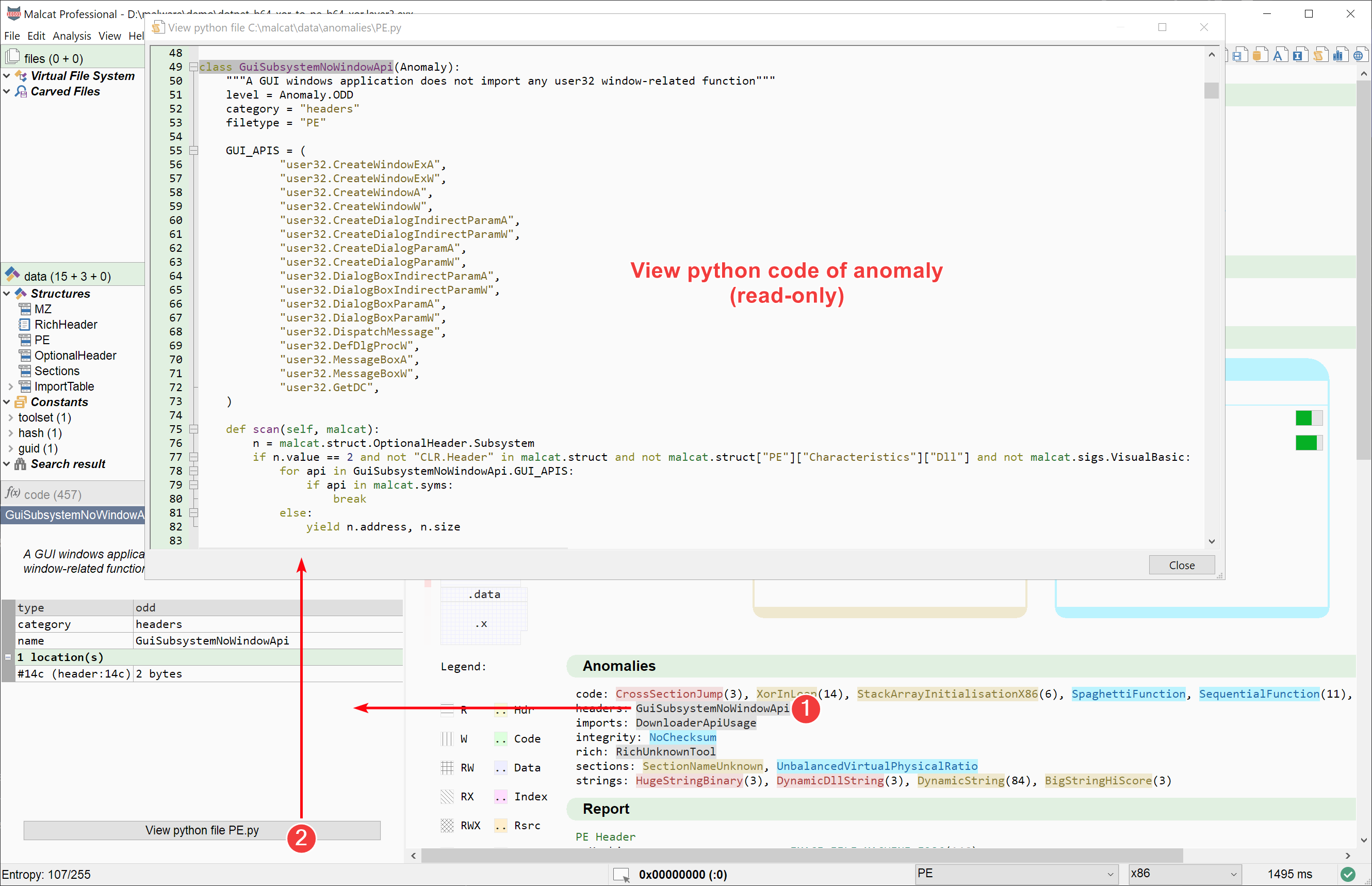
Note that while it is currently not possible to modify the python code using the in-app editor currently, it is pretty easy to create and/or modify existing anomalies in Malcat. Just patch the python files and hit Ctrl+R! In-app edition will come in the future.
Yara file organiser
The Yara editor in Malcat also got a small improvement. It is now possible to add, remove and rename Yara file from within the Yara file browser control located on the left. Note that the Yara file browser is hidden by default. You need to click on left-most button of the toolbar first to make it visible.
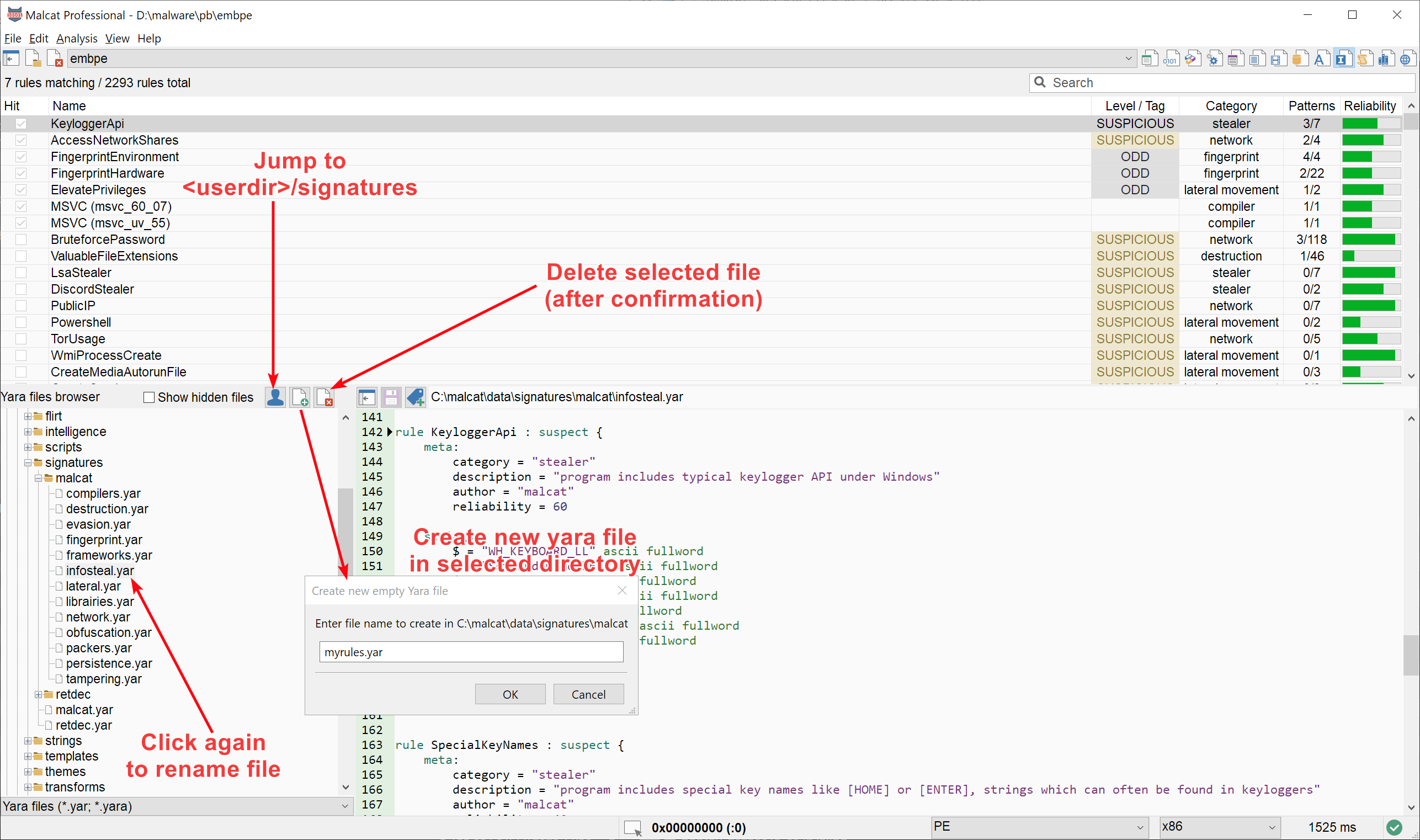
We have also added a small shortcut button to the Yara file browser control that will take you to the signatures/ subdirectory of your user directory directly (if you have setup one). It comes in handy when you want to quickly add a new Yara rule in your user data directory, or if you just want to review your custom Yara rules.
Confirmation before memory-heavy operations
If you are editing very large files or if you have very little resources, you may exhaust all your computer memory at some point. While this is pretty rare (you need to edit files bigger than a few gigabytes), it can be annoying since it make the whole computer unresponsive. In order to prevent this edge case, we have added a few checks in the application before most of the memory-intensive operations (mostly file loading and editing):
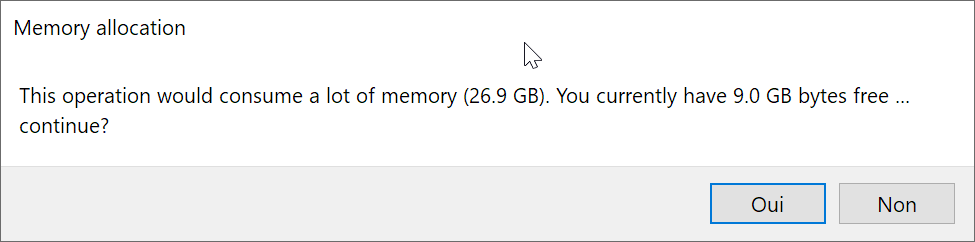
This dialog will be shown if the operation would consume more than the "Big file mode" threshold in memory (defaults to 256Mb) and/or more than 80% of the free memory available in your system. See it like a small safety net against misclicks.
Note that the memory checks are not foolproof. For some analyses for instance like the CFG reconstruction or the strings extraction, Malcat can't possibly know in advance how much memory would be consumed.
User directory QoL
Also a small QoL improvement: when you setup your user data directory from the Preferences dialog, Malcat will now offer you to create the initial directory structure for you. Also a button was added to the Preferences dialog to unset the user data directory. Additionally, user data directory changes no longer require you to restart the application to take effect.
Full changelog
Here is the complete changelog of this release:
● Source code view:
- The source code view (F4) got a revamp: folding and syntax highlighting added
- Pure ascii/utf8/utf16-le text files can now also be viewed as text in the source code view (F4).
● Transforms (Ctrl+T):
- Completely redesigned the transform dialog
- Added the ability to chain transform steps (request from @Cm)
- You can now search&filter transform operators
- Added the ability to view or edit python files of transform operators in-app
- Transform previewing is now done in a background thread
- Transform dialog is now modless (i.e. you can continue to use Malcat in parallel)
- Transforms can have different icons
● CHM format:
- Added support for .CHM archives
- Can extract archive content in-app!
● .NET:
- Parsing of obfuscated .net method headers should be more robust
- Identify and highlight static field initialisation data
● File editing:
- You can now removed selected bytes from the current file using the selection context menu
- You can now insert an aribtrary amount of bytes at the selected location using the context menu
- Added an option in Preferences > General to automatically reanalyse the current file after every insert/delete
- You can now shift the selected bytes up or down using the selection context menu
● User interface:
- "Select All" command ("Ctrl+A") now acts according the current view, i.e will select all strings in string view or all text in source code view
- Source code folding added to the script editor (F8) and other python editors
- The analysis progress bar (in the status bar) should better adapt to analysis times when some analyses are deactivated
- Reduced redraws of the augmented scroll bars in hex view and structure view
- You can now add, delete and rename .yar files from within the file lister control of the Yara editor (request from @Cm)
- Added button in options dialog to clear user data dir (request from @Ben)
- User data dir changes no longer requires to restart Malcat: just re-analyse (Ctrl+R) for the changes to take effect
- When chosing a new user data dir in the Options Dialog, Malcat will now offer to create the initial dir structure for you
- Added a button in anomaly preview to view the anomaly's code inside the python editor
- Show a confirmation dialog for operations (mainly file loading without mmap) consuming a lot of memory and/or more than 80% of the available free memory
- The augmented scrollbars should be somewhat more precise
- In malcat scripts, malcat.file.path is now also available as sys.argv[1] (request from @disasm.re)
- Recent files list size increased from 10 to 16
- Added back / next buttons in the project's toolbar (request from @epicout)
● Bug fixing:
- [LINUX] some views would reraise the window when mouse cursor is over, preventing alt-tab when on this view (thx @wisdomsocks)
- Fixed a race condition in the summary view section layout mouse hover code that could lead to a crash (thx @Squiblydoo and @voidofone)
- Fixed improper index construction of the HasFieldMarshal index in .NET which could lead to bad parsing for .NET programs having more than 32K #Param entries (thx @Squiblydoo)
- Lack of validation for exception infos would lead the CFG reconstruction algorithm to abort early (thx @Squiblydoo)
- The augmented scrollbar would (in some very rare configurations) display an annotation twice
- PE: early catch of pyasn1 decoding errors (make the certificate parsing more robust)
- Histogram's tip label would not be destroyed consistently (regression in 0.9.1)
- [LINUX] crash when hovering histrogram's bar: wxTipWindow would be destroyed twice (thx @Ben)
- assertion error when importing yara rules from the user data dir (thx @Ben)
- C formatting of strings in structure view would display extra 0xFFs for chars >= 0x80
- Fixed bug in .PYC disassembler
- Fixed: address column would not be redrawn correctly in disassembly view when "Delta addresses" option (Ctrl+B) is chosen
- Current view window now correctly gets focus after double-clicking on the side bar
- Fixed display quirk in structure view when displaying strings longer than the screen surface
- [WINDOWS] Fixed file lock issue in big file mode (thx @Squiblydoo)