Today we are happy to announce the release of version 0.9.5. We have added a new InnoSetup parser and a PascalScript disassembler to handle all those pesky Inno malware. But that's not all, you will also find a lot of small improvements which should make your life a bit easier:
- Added a AR archive parser (.lib)
- Improved/redesigned several GUI controls (file switcher, user script loading, undo/redo history)
- Added three threat intelligence providers
- You can now download a sample by hash (queries the available threat intel providers)
- Debian 12 builds
- .. and the usual doc / anomalies / Yara signatures updates
If you want to see the complete list of improvements, have a look at the changelog, at the bottom of this article.
New InnoSetup parser
InnoSetup installers
Malware authors often used legitimate software such as installers to encapsulate and/or obfuscate their malicious programs and scripts. MSI installers (which we support) are a popular choice, as well as NSIS installers (we support them too). InnoSetup installers are slightly less popular, but gained some attention recently due to their use in the Socks5Systemz malware campaigns:
Don't worry, we have you covered: support for InnoSetup installers has been added to Malcat 0.9.5! You'll be able to identify/carve Inno installers, explore their internal structures, disassemble their install scripts and of course unpack and open the bundled files inside Malcat.
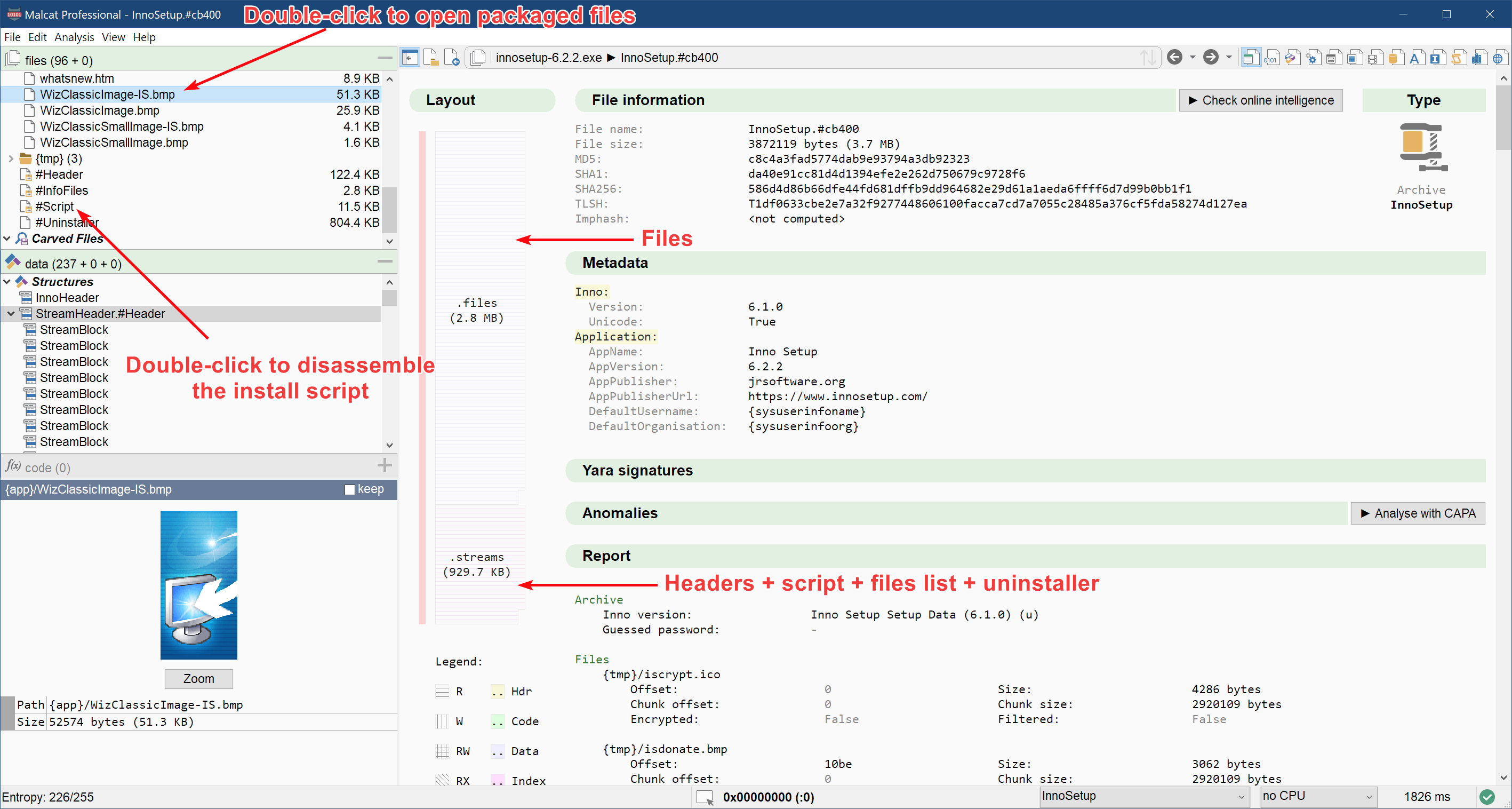
Malcat currently supports InnoSetup ranging from version 4.0.0 up to 6.2.0. Compression using either lzma1, lzma2, bzip2 or zlib are supported (this should cover 99% of the installers). InnoSetup also offers a password-based RC4 encryption, which Malcat also supports.
InnoSetup is an open source installer. As such, a few unofficial variants have been created over the years. Unofficial versions may or may not be supported depending on the extent of the modifications.
PascalScript disassembler
InnoSetup installers are programmed in Pascal, and often embed an install script to drive the installation process. This install script is written in a language named PascalScript: this is a bytecode-based interpreted language, like a (very) simplified version of python with some Pascal-like features. Inno scripts can be pretty powerful, as they have access not only to the installer API, but can also use DLL plugins and even call Windows API directly! As you can imagine, these advanced features are a gift from heaven for threat actors.
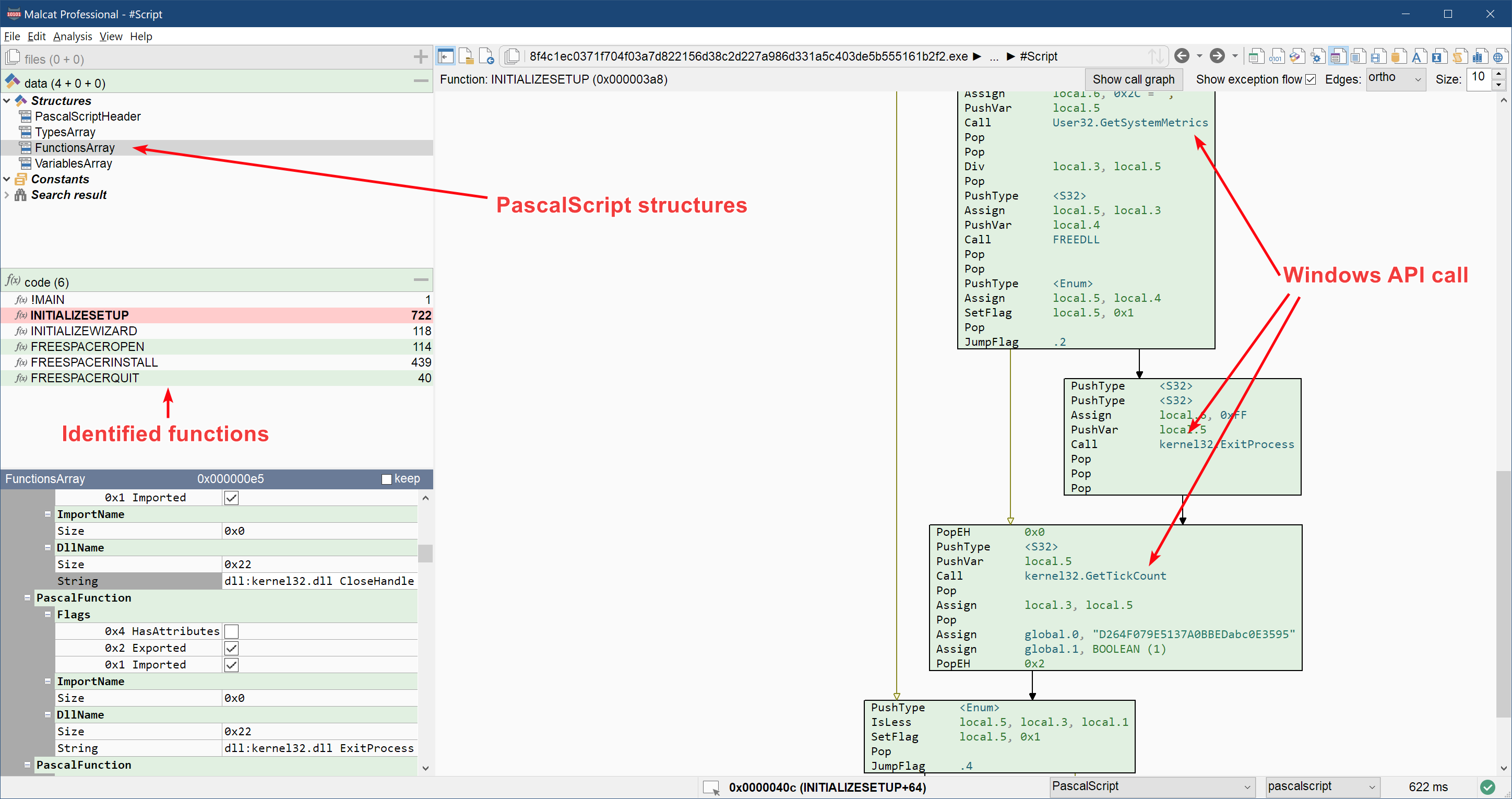
Since these scripts are heavily used by malware author, we have also added a new PascalScript disassembler to Malcat. If you double-click on the #Script special file inside Malcat, you will be able to dissect it and use all of Malcat's code-related features. Note that this new CPU architecture is not available in the lite version, which is limited to x86/x64. But lite users will still be able to inspect the various script structures.
A few of the tricks that we have seen so far in malicious Inno installers are listed below:
- Scripts fingerprinting their environment (language, screen resolution, date) before running their payload
- Scripts using either Windows API or the
idp.dllplugin to download the second stage payloads - Script patching packaged files (e.g. restoring their
MZheader) in order to bypass static scanners - Encrypted installers
The last trick is a simple but clever one: InnoSetup supports encryption for its stored files (like a zip archive). Internally, the files are encrypted using the RC4 algorithm, the key beeing derived from a user-supplied password (upon installation, a dialog appears asking the user to give the password). Without the password (and thus the RC4 key), static scanners cannot inspect the content of the installer, which is something malware authors are big fans of.
So how could malware author benefit from InnoSetup's encryption mechanism, without having to tell infected user to enter a password? That's when the script magic happens: the script will first hide the password dialog, and then fill a hardcoded password inside the text control of the password dialog, allowing the installation to silently continue.
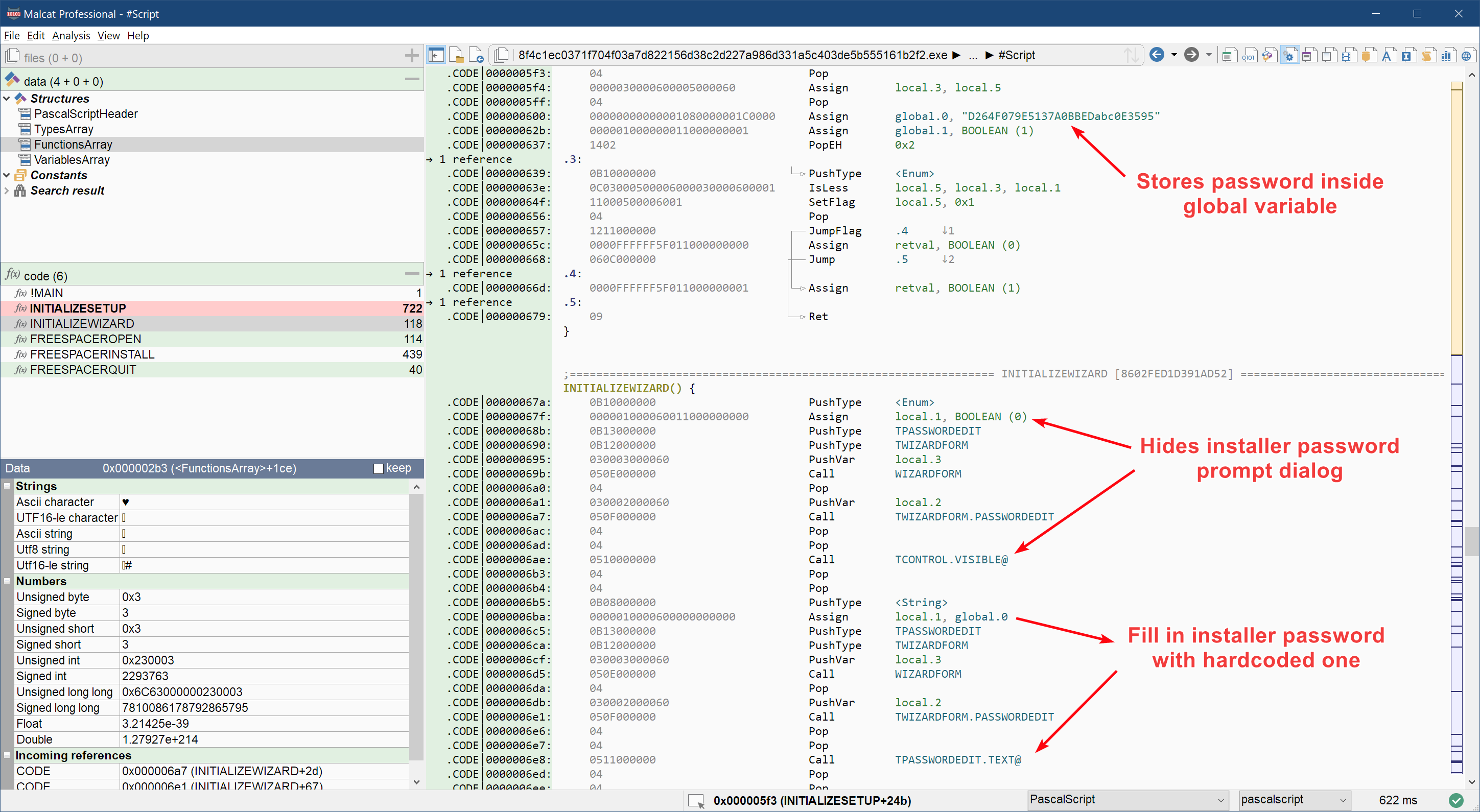
Since this can be relatively annoying to manually search through the script for such passwords, Malcat's InnoSetup file parser will do it automatically for you. Upon encountering encrypted files, it will scan the PascalScript code and try to decrypt the first entry using every hard-coded string it sees. It's of course not fail-proof, but it works in most cases. You can see the result of this bruteforce pass in the script editor window.
AR archives support
The AR file format is an old unix archive format. It has mainly one use nowadays: static libraries. It is indeed used to gather collections of object files in static libraries under Linux (.a file extension) and under Windows (.lib file extension).
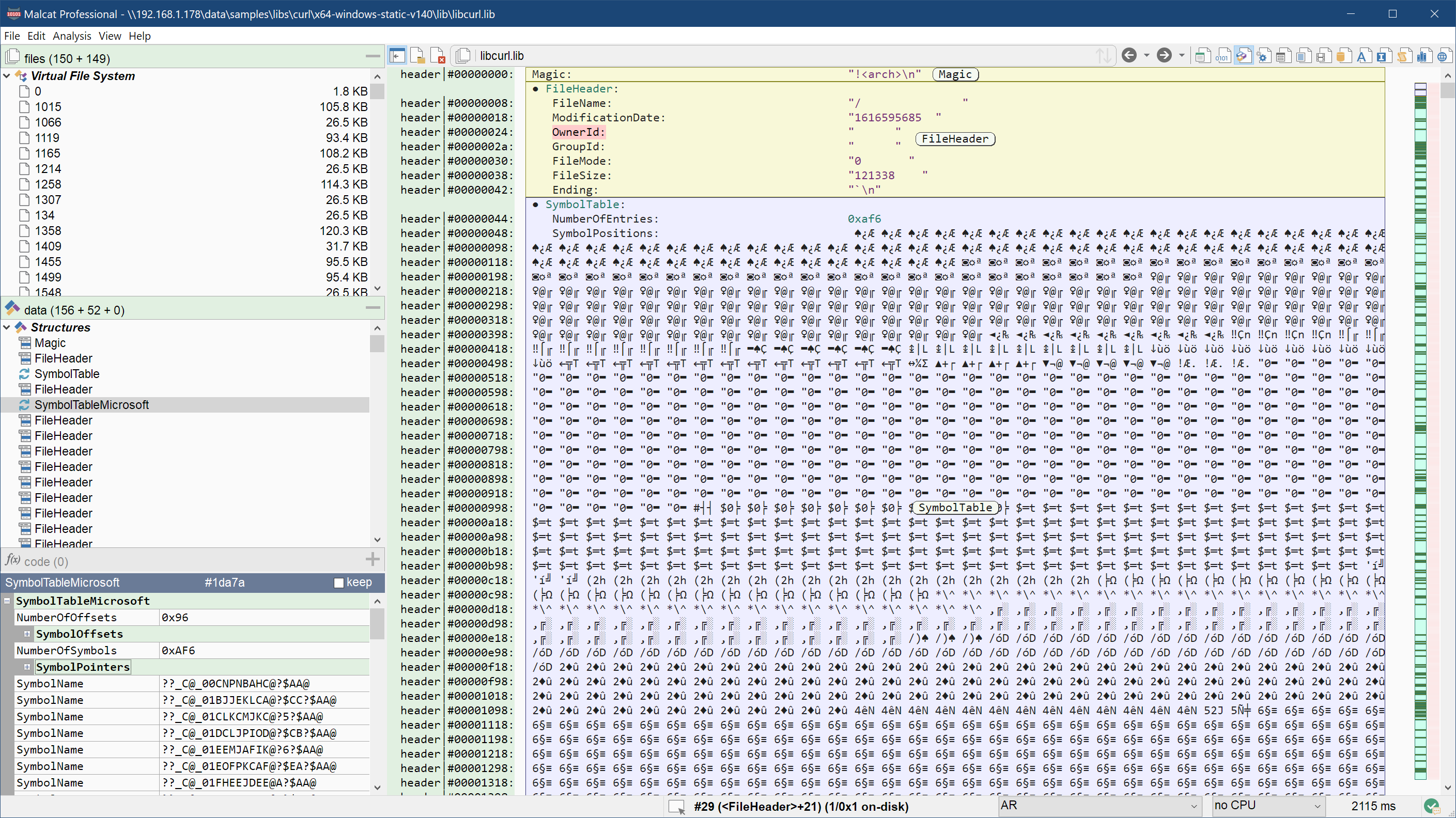
You can now open this type of archive directly under Malcat. You'll be able to see its structures, list the archive members and unpack them directly in Malcat. Why did we add this file format you may ask? Well, we needed this internally in order to parse code libraries. You'll see why in the next update hopefully ^^.
User interface improvements
New file switcher control
The file-switcher control is the UI control located at the top of the project window in Malcat. It allows the user to switch between projects. Until now, it was implemented using a simple drop-down control which looked ok-ish under Windows and rather ugly under Linux. And beside its bad look, a few users were a bit lost and did not see the purpose of this control, wondering how to switch between projects. These are the signs of bad UI design and called for a redesign.
We have thus refreshed the look and feel of this control. It is now drawn manually: it not only looks better, but has now a consistent look across operating systems. And since we now have control over its look, we can also display more information. You will now see the number of open projects in a small badge over the file icon (when more than on project is open).
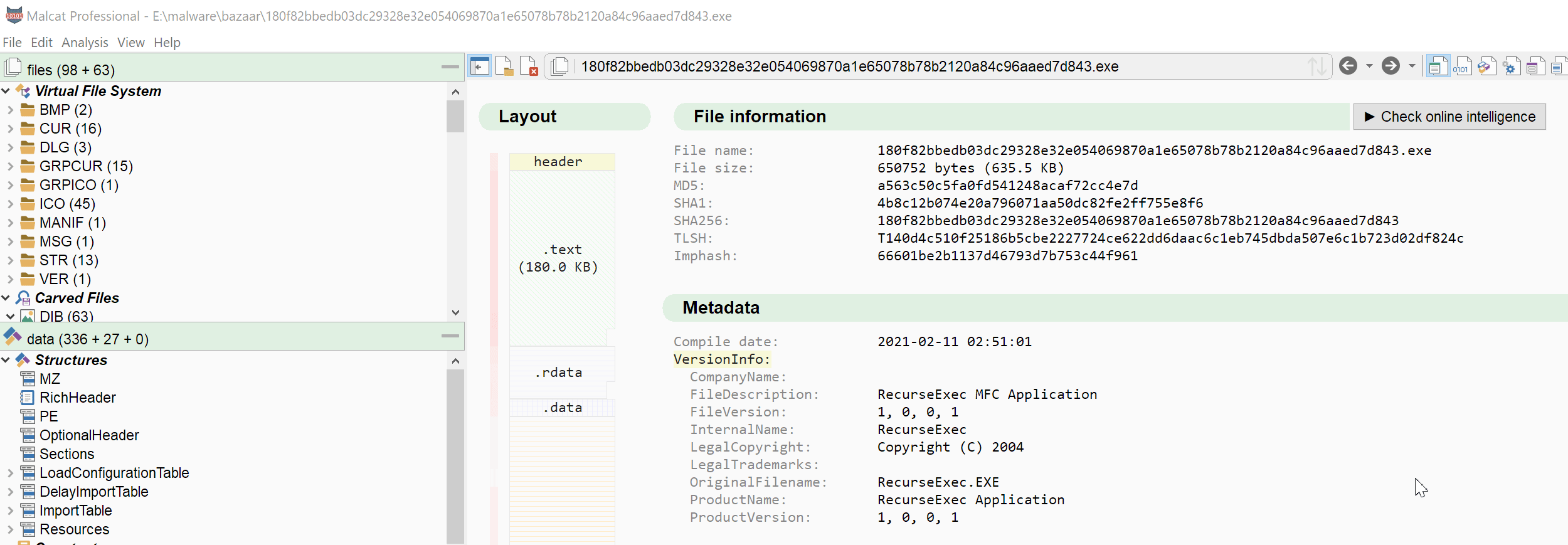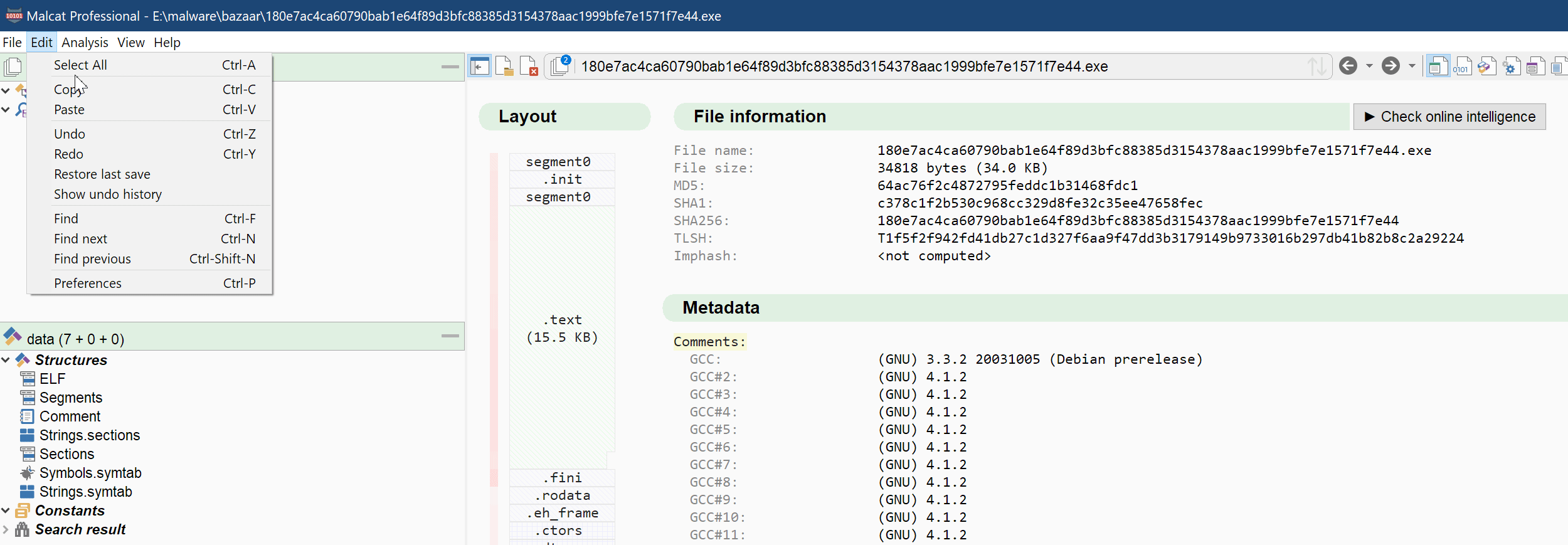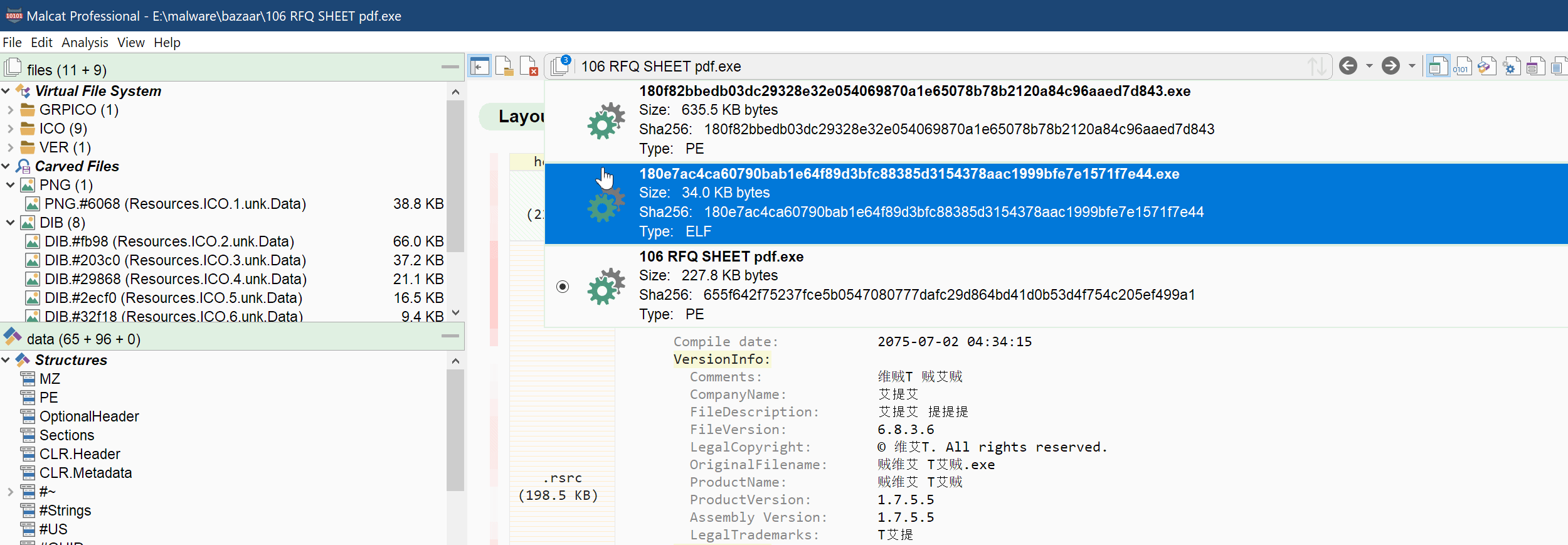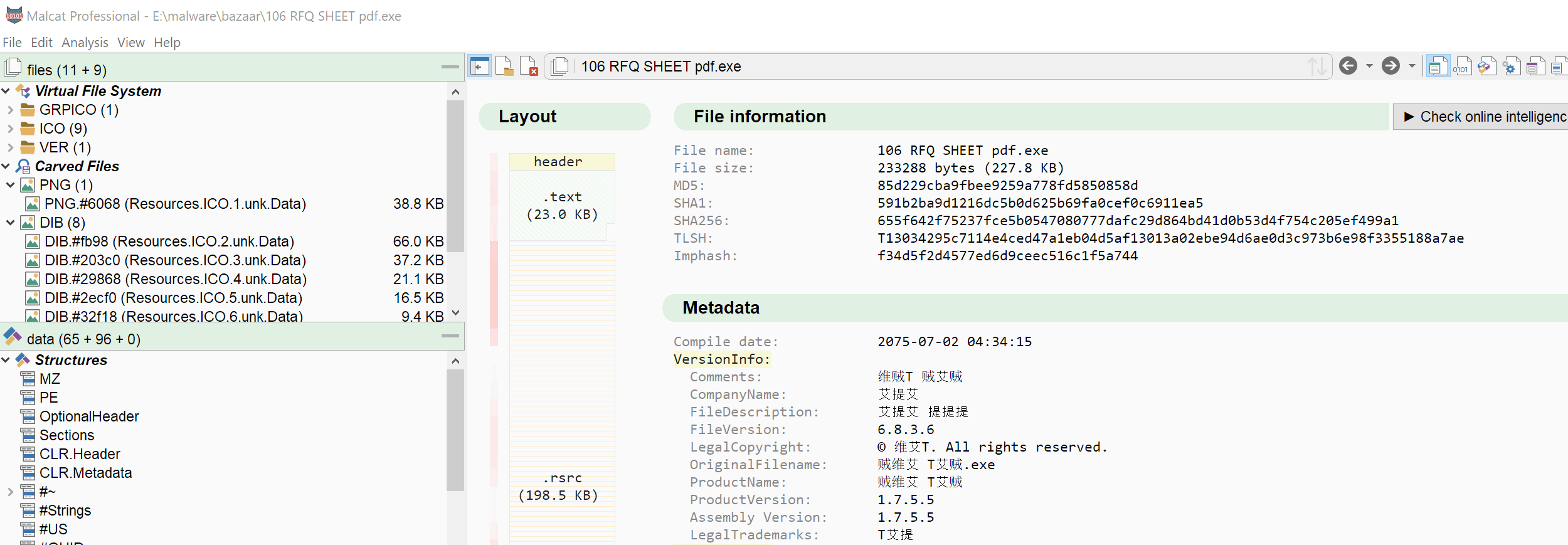
Last but not least, when opening or closing a project, the control will briefly blink. This will hopefully indicates to new users that something happened there and that they can switch between projects using this control.
Improved user script loading dialog
Malcat comes with a few utility scripts to make malware analysis easier. You can for instance emulate stuff with speakeasy (if you have the lib installed), decrypt office documents or concatenate Excel sheet cells values. It was a bit annoying to load these scripts using the standard file open dialog though, mainly for two reasons:
- It is not always clear what a script does by just looking at its file name
- If you have scripts in your user data directory, it can be a chore to switch between the
data/dir and your user dir every time
So we have left the standard file open dialog for a custom one specially made for this purpose. In this dialog, you will see listed all the scripts from the default data/scripts AND your <user data dir>/scripts directory together. Also some metadata and a verbose description of what the script does are now displayed if you click on a script:
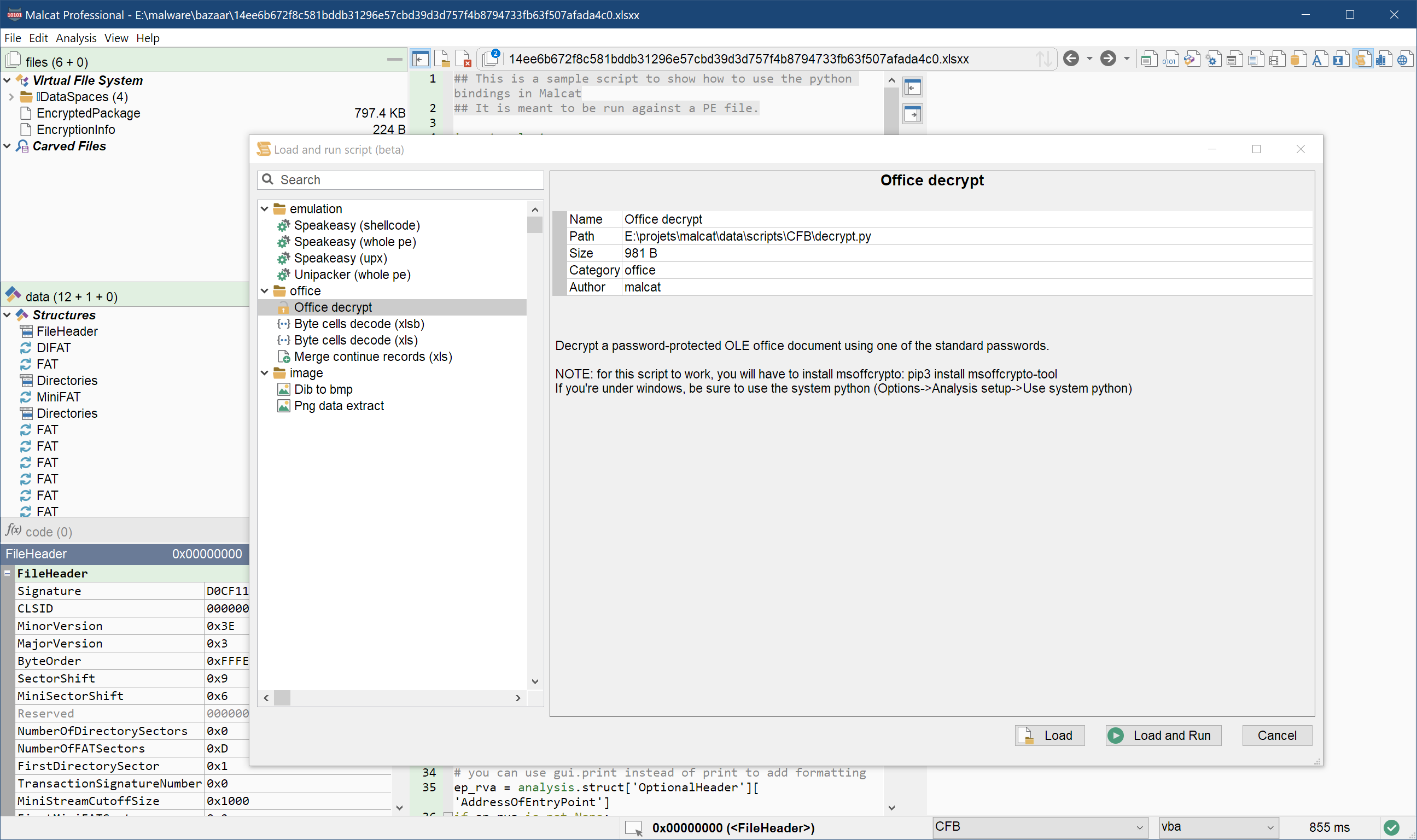
Note that user scripts now have to start with a doc string containing a few metadata elements. The name metadata is mandatory: script missing it will not appear in the script load dialog. The other metadata (category, author and icon) are nice to have, but optional. Text following these metadata elements will be considered by Malcat as the module's description text. Below is an example for our XLSB cell concatenation utility script:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 | |
New undo/redo history dialog
If you make many changes to a file, it can be sometimes hard to keep track of what did change and where. This is particularly true if these changes are issued programmatically by a script.
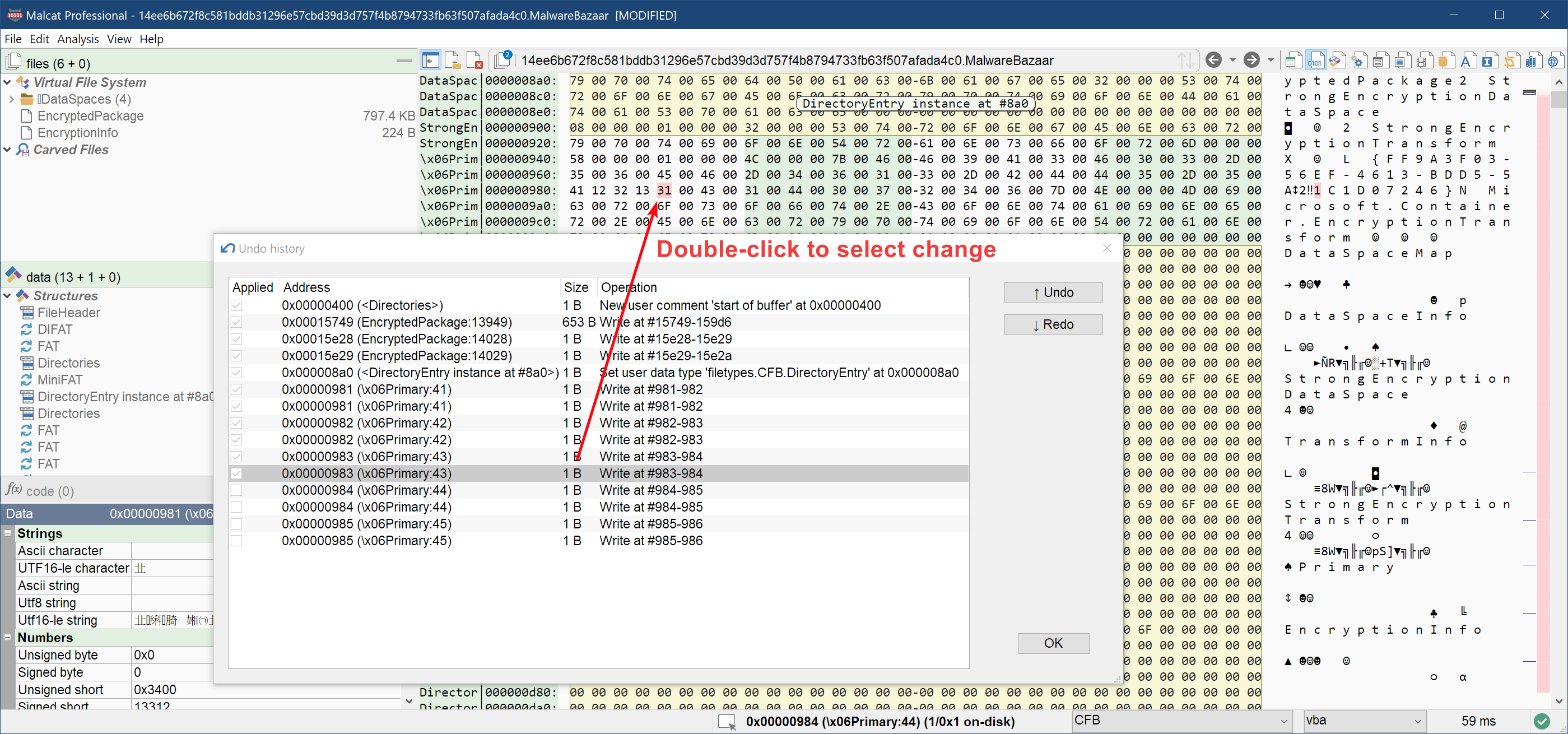
In order to improve the user experience, we have added a new undo/redo history dialog to Malcat. You can show the dialog using the menu Edit>Show undo history. There you will see the complete list of your changes (file edits, new comments, types or functions) and undo/redo them easily. Double-clicking on a change will jump to the location of the change and select what has changed. We hope you'll find this feature handy.
New VGA theme
I don't think that the VGA theme in Malcat was used by anyone. We won't blame you: while it has some neat retro vibes, it was not really suitable for daily use. So we have completely redesigned it and gave him a black background for more comfort. Hopefully this will make a second usable dark theme for Malcat.
Also a quick note regarding dark themes: I have a good news for Windows users. WxWidgets should have (finally) support for Windows dark mode in the upcoming 3.3.0 release! I know, we're in 2024, but just a bit more patience.
Threat intelligence
New providers: Kasperksy OpenTIP, MalShare and VirusShare
We have now added Kasperksy OpenTIP, MalShare and VirusShare to the list of online threat intelligence lookup services (NB: this feature is not available in Malcat lite). Make sure to enter your API keys for these services (you can setup an account for free) into Malcat's preferences dialog, and run the online threat intelligence lookup (Ctrl+I).
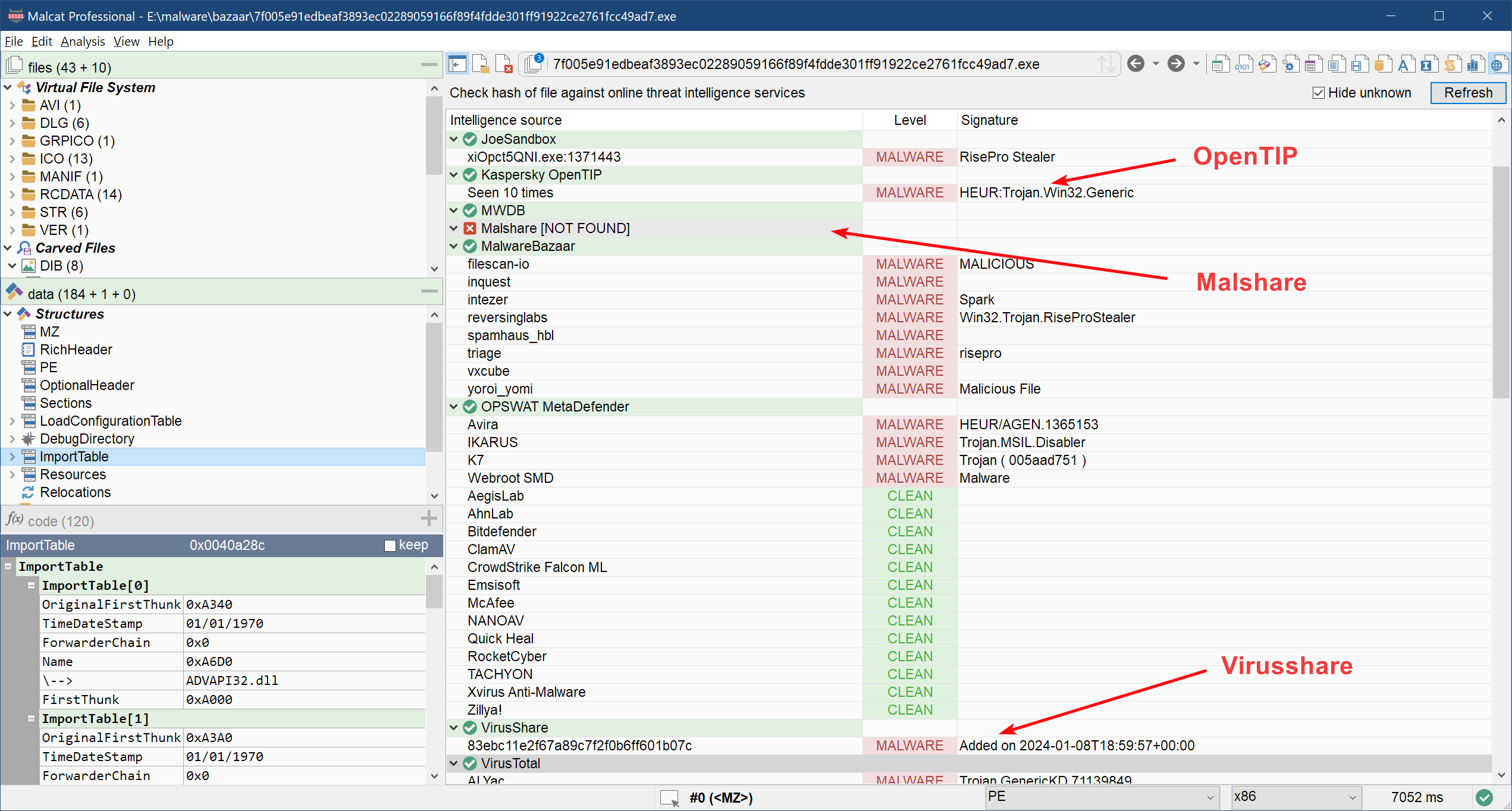
Note that MalShare and VirusShare APIs don't give back any threat score or detection levels for a given hash, you will only be able to check if a given hash is in their database or not. While the probability that a file is malicious if present in their database is high, it's not a guarantee. That's why Malcat will always set the threat level to Unknown for these two services.
A small tip: you can double-click a detection line in the threat intel view, and it will open the result page of the threat intelligence provider in your default browser
Download a sample by url / hash
If you are a heavy reader of malware analysis reports and/or cybersecurity twitter, you know that samples are most of the time referenced by their sha256 hash. And I don't know for you, but to me "find the sample" is a game that quickly gets old. Where has it been uploaded? Where is my API key for this service? Where should I download & unpack it?
In order to ease this process a bit, we have added a new dialog accessible via the menu File>Download from url/hash. If you give an http(s)/ftp url there, the sample will be downloaded directly. But you can also specify a md5, sha1 or sha256 (prefered) hash. In this case, the sample will be searched across the threat intelligence services that you have setup in Malcat. The following intelligence services are currently supported:
- MalShare
- VirusShare
- MalwareBazaar
- MalwareDb
NB: Virustotal is not supported for now, since I don't have a VTI key to test sorry
If the file can be found online, it will be downloaded, unzipped (if needed), its hash will be double-checked, and the file will finally be open in Malcat. Note that the file is open IN MEMORY and will NOT be saved to disk by default until you hit Ctrl+S. This has the added benefits of not triggering your local antivirus and you won't load your disk with a sample that you'll most likely discard anyway.
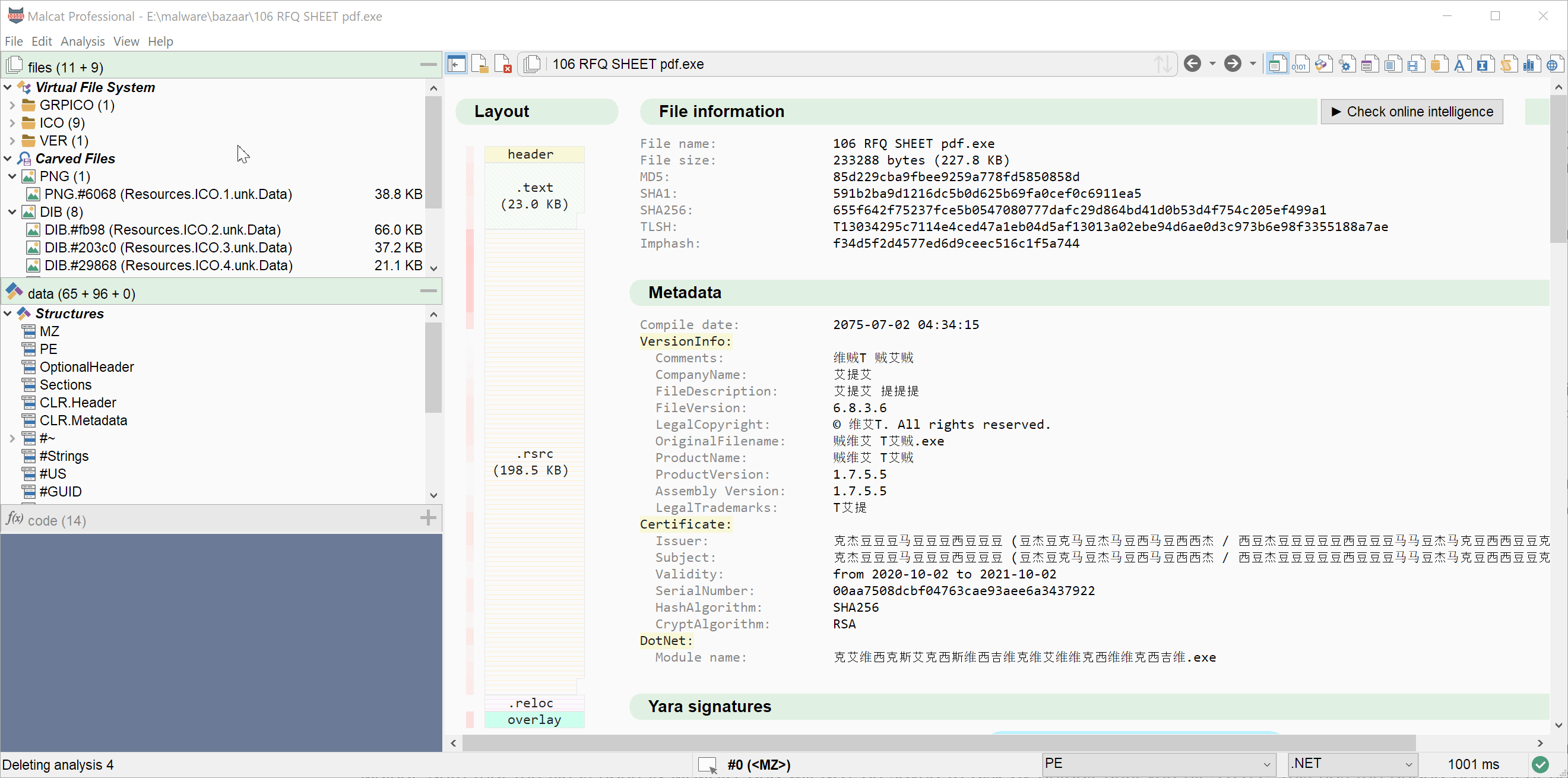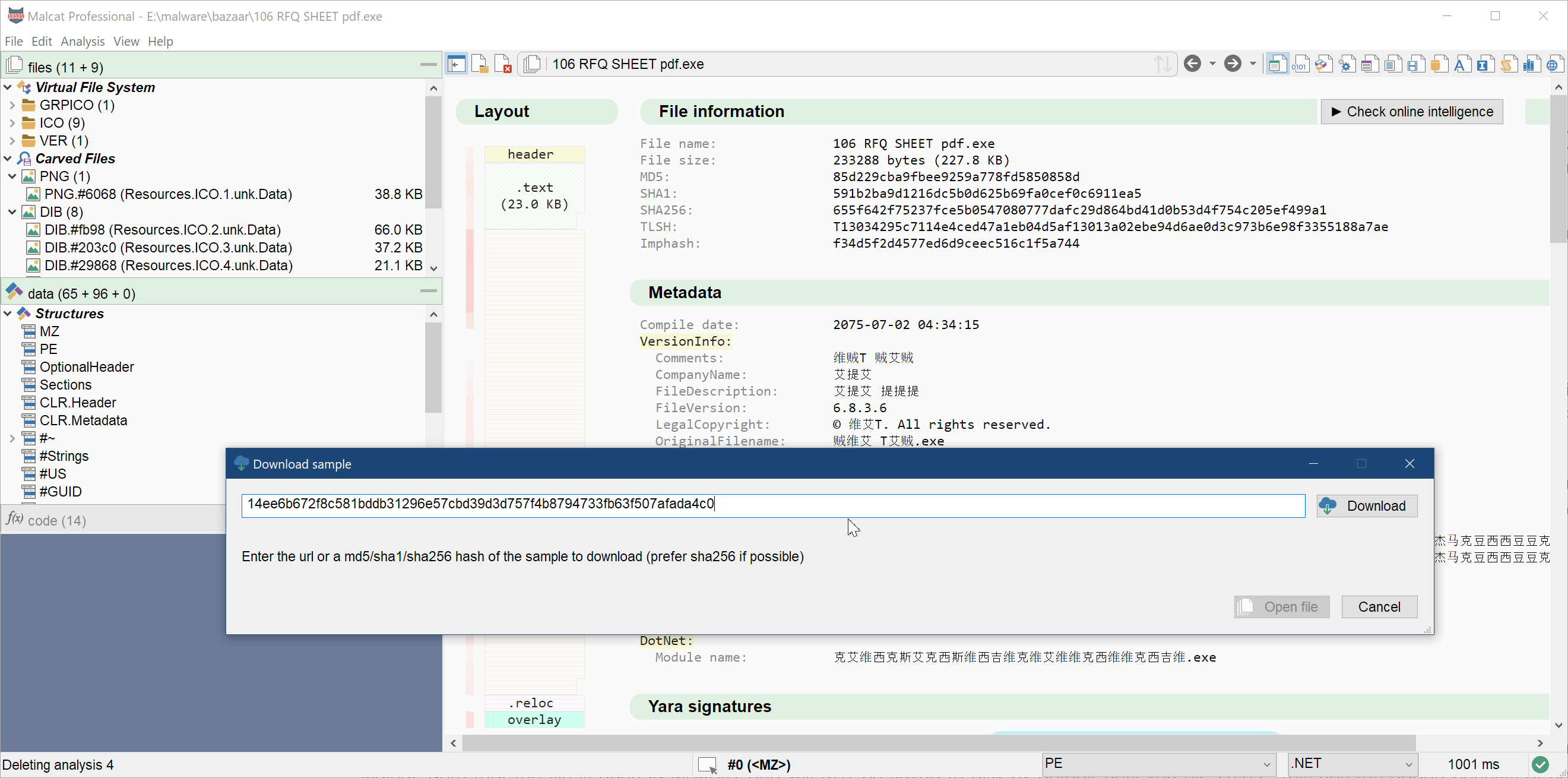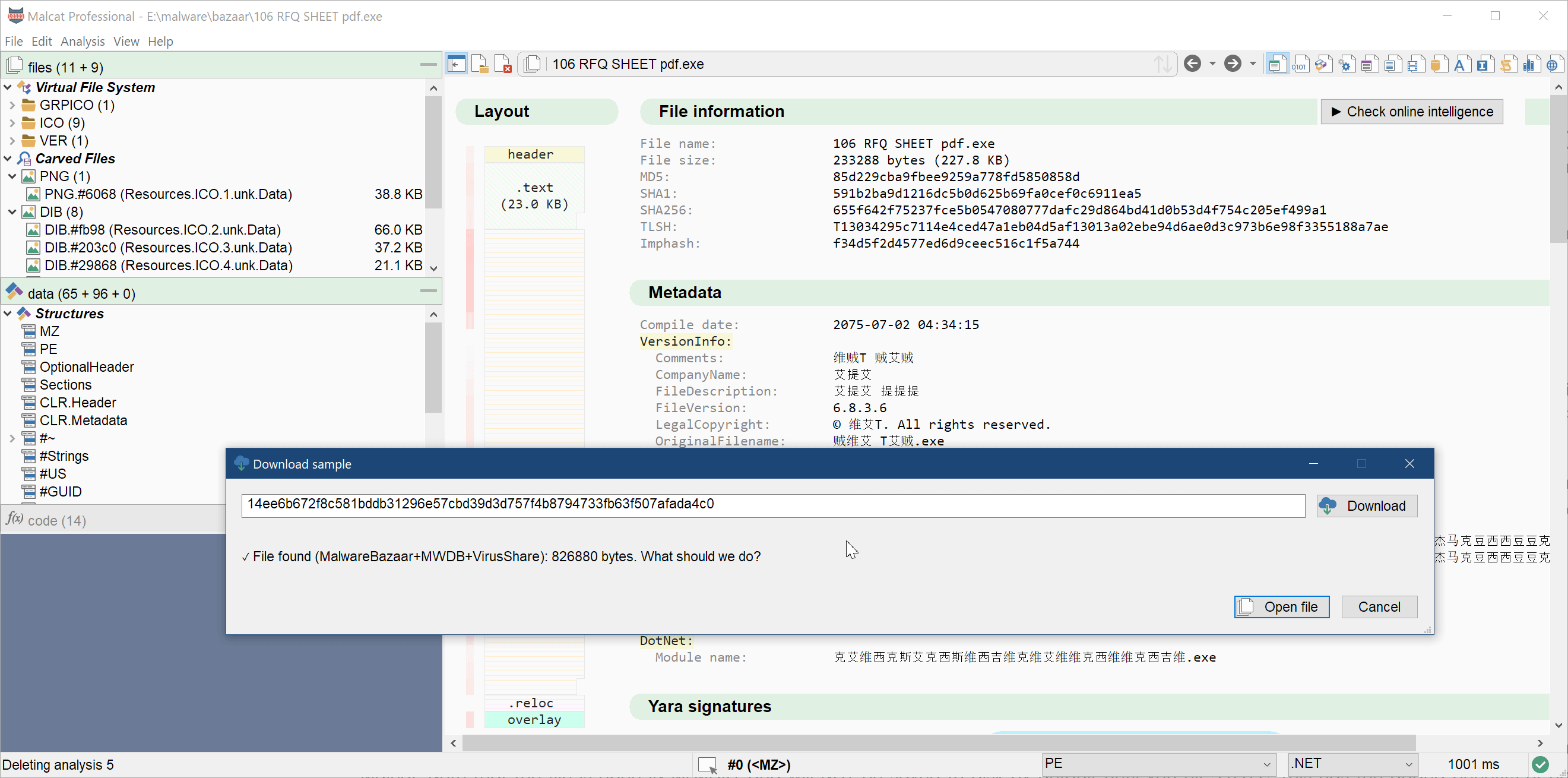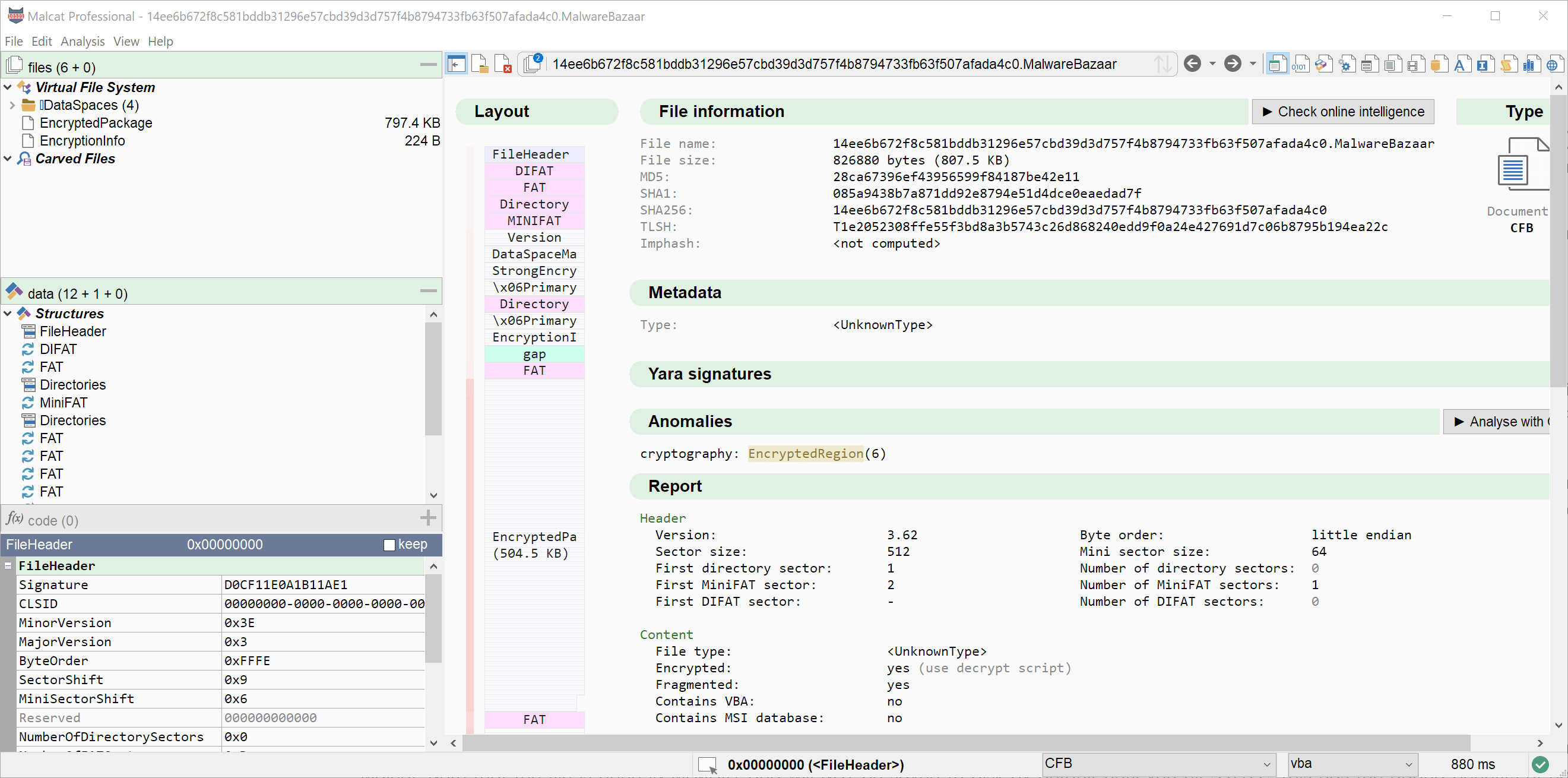
We find this small feature quite convenient and we hope you'll also like it. Please note that it is also available for Malcat lite users.
Debian 12 builds
It was time, but we now provide binaries for the recent Debian 12 (bookworm) distribution! The binaries should also be compatible with other python 3.11-based Linux distributions.
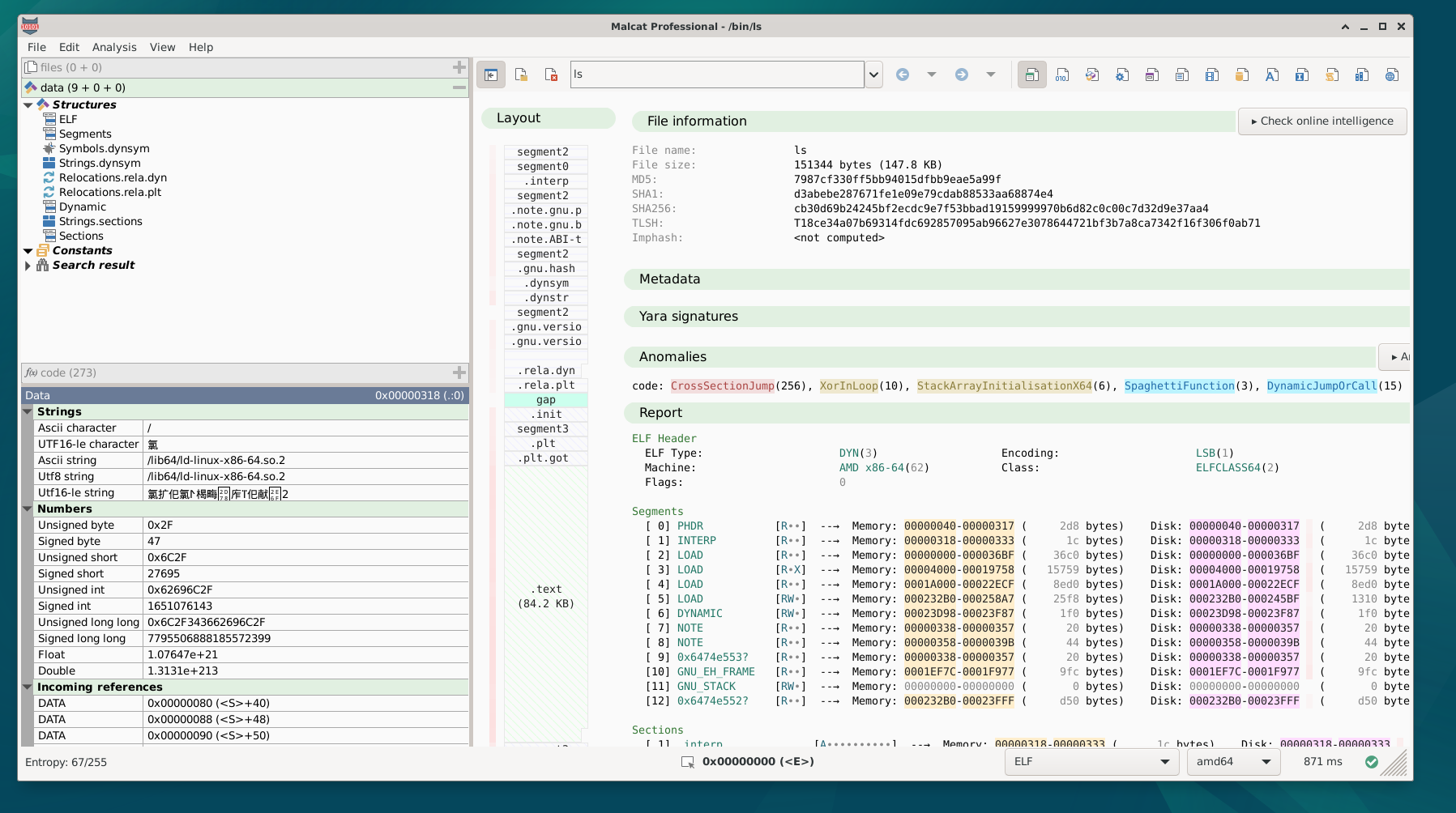
If you own a purchased version of Malcat and want to test on debian 12, just visit the download link you got in the email: the debian 12 archive has been added to the bundle. For free user, it is available in the download page.
Full changelog
Here is the complete changelog of this release:
● Parsers:
- Added parser for InnoSetup archives from version 4.0.9+
- Added AR archive parser (.ar, .lib)
- Improved OBJ parsing
- Improved 7Z parsing
- Improved EMF parsing
● Disassemblers:
- Added new PascalScript disassembler (binary pascal-like bytecode used in innosetup installers)
● User interface:
- Redid & improved the file-switching control
- Previously entered text in the search dialog is now always selected (saves some clicks if you want to replace it)
- In asm view, Ctrl+C copy selection as hexadecimal bytes (instead of disasm) if the last mouse click was in the hex column
- Transform dialog "new file" option now opens result in new tab
- Image previews for virtual files are now generated in the background for better UI responsiveness
- The files panel folder labels now show the number of descendant nodes instead of the number of direct children
- Added an option (Preferences>Interface>Panels on the right) to put the quickview + navigation panels on the right side
- Added option to manually pin the current quickview
- Redesigned & improved the user script load dialog
- Added '*'/'?' shortcut in hexa/struct/disasm/dna views: go to next/previous selected area
- Added '.' shortcut in hexa/struct/disasm/dna views: go to last file modification and select it
- Reworked the UI theme 'vga'
- Added a menu entry to switch theme
- Added a new undo/redo history dialog (Edit>Show undo/redo history)
- Saving the current file under a different file name (save as) adds the new path to the recent files list
● Scripting:
- Added shortcut to iterate over all basic blocks in a function: for bb in the_function:
- Added shortcut to iterate over all instructions in a basic block: for instr in the_bb:
- Added new "khash" attribute to function objects: a 64bits hash of the function code that masks out all position-dependent bytes (i.e. offsets).
- Added new function metric: fn.num_highvalue_immediates
- Added new function metric: fn.num_unique_immediate_bytes
- [GUILESS scripting] Python bindings don't automatically throw an error if the analysis failed anymore. Use the new method analysis.raise_if_failed() for that.
- Added new attributes analysis.failed and analysis.ok
- Added new attribute analysis.log which contain all analysis errors and warnings
● Transforms:
- Added 'calculate' transform in text/scripts
- Added 'hex2dec' transform in text/scripts
- Added 'fill' transform
- Added LZNT1 compress/decompress transforms
● Anomalies:
- Added new code anomaly ManyHighValueImmediates
- Added new code anomaly ManyUniqueImmediateBytes
- Added new Ole anomaly OleExternalLink
- Added new Ole anomaly EncryptedWorkbook
● Intelligence:
- Added VirusShare online lookup
- Added Malshare online lookup
- Added a new dialog <File>download from url/hash> that can download a sample from TI providers (currently only MWDB, MalwareBazaar, Malshare and Virusshare)
● Diffing:
- The diff window size is now correctly taken into account when diffing
- Diff window parameter limit has been increased
- Better diff progress report in status bar
● Bug fixing:
- Fixed a focus issue when selecting data happening to be inside a structure from the data view under Linux
- [Linux] Fixed Codeview debug information parsing issue on linux
- install_api.py -u now correctly uninstalls malcat even if you moved/deleted the malcat directory beforehand
- Fixed a regression where (big) image previews in the quick view panel had incorrect size on HiDPI screens
- Fixed a regression where the CAPA bindings would miss imports-based rules
- choosing "new file" in the transform dialog when inside the source code view would replace the current file with the new one
- fixed a regression where keyboard shortcut in hex/struct/disasm views could not jump to the first annotation in file
- sometimes, the msvc demangler would return empty function names: use the original symbol name in this case
- recovered RTTI virtual function names would override exported symbols, which is unlucky since exported names are often more descriptive. Do it the other way around.
- fixed a rare crash when iterating backward through overlapping strings in a data view using keyboard shortcuts
- [Linux] fixed a crash when dumping a non-ascii virtual file to disk
- [Lite] fixed a crash in the summary view
- Fixed GUI staying unresponsive for a long time when decompiling very large AutoIT scripts
- Fixed trailing 00s in unpacked TAR archive member file names