
Malcat scripting tutorial: deobfuscating Latrodectus
In this tutorial, we will learn how to leverage Malcat's scripting and patching capabilities to deobfuscate an unpacked Latrodectus sample.
Read more →

Get your swimsuit, we're diving into a black SEO scheme
What started like an easy unpacking session to fill a Friday afternoon lead us to a singular black-SEO campaign. Together, we will unravel 4 different malicious loaders written in 4 different programming languages, briefly analyse the final 10MB black-seo client and reverse engineer its command and control protocol. All of this for XXL swimsuits.
Read more →
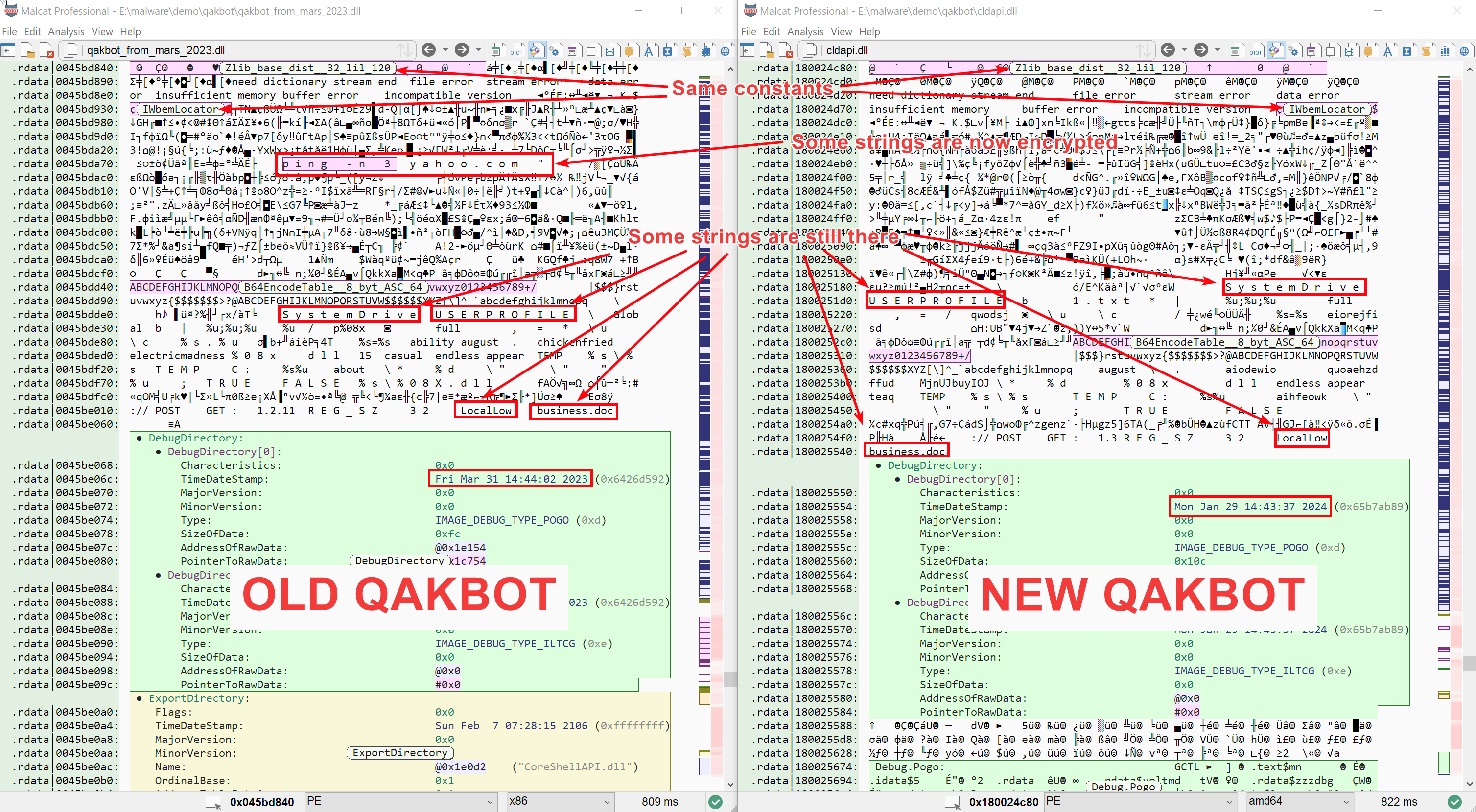
Writing a Qakbot 5.0 config extractor with Malcat
Starting from a (backdoored) MSI installer, we will unroll the infection to chain to get the final Qakbot sample. Sticking to pure static analysis, we will then decrypt Qakbot's configuration and finally write a script in Malcat to automate the process.
Read more →
LNK forensic and config extraction of a cobalt strike beacon
Windows shortcut files can contain valuable data. We will see how to extract the most information out of a .lnk downloader and will manually extract the configuration file of the final cobalt strike beacon using malcat
Read more →
Reversing a NSIS dropper using quick and dirty shellcode emulation
We will statically unpack and emulate a malicious NSIS installer running multiple shellcodes, up to the final Lokibot password stealer and its configuration.
Read more →
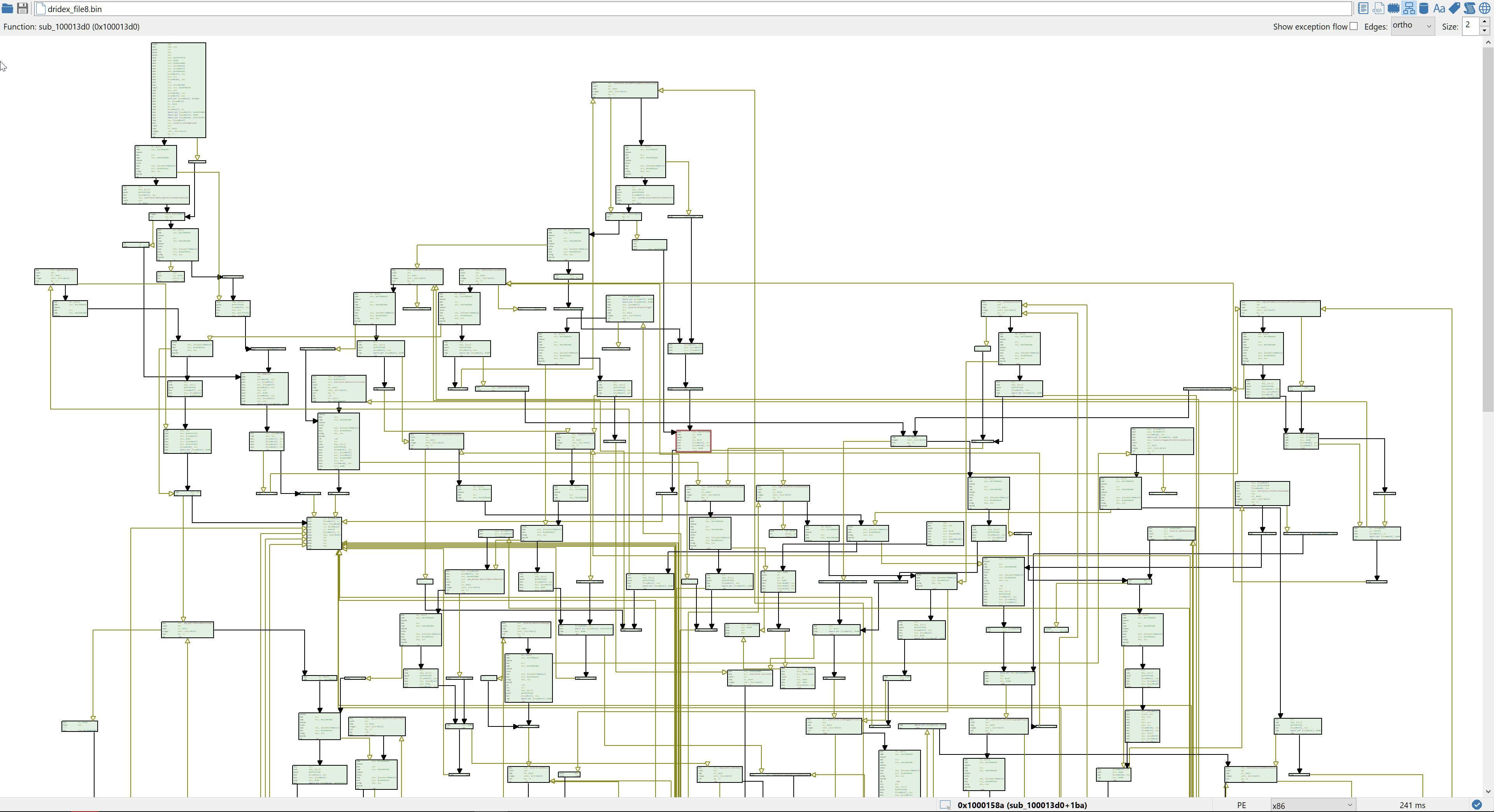
Cutting corners against a Dridex downloader
When one faces obfuscated code, it is sometimes more efficient to focus on the data instead. By using Malcat's different views and analyses (and a bit of guessing as well), we will show how to statically unpack an excel downloader and the following obfuscated native dropper without (much) reverse engineering.
Read more →
Exploit, steganography and Delphi: unpacking DBatLoader
We will unroll a maldoc spam exploiting CVE-2018-0798 leading to a multi-staged Delphi dropper abusing steganography and cloud services to conceal its payload
Read more →
Statically unpacking a simple .NET dropper
Our target is a 2-layers .NET dropper using multiple cipher passes (XOR, AES ECB and AES CBC + PBKDF2) to finally drop a Loki sample. Without even starting a debugger, we will show how to unpack it 100% statically using Malcat's builtin transformations and the python scripting engine.
Read more →